Scan Network Range
1
2
3
4
5
6
7
8
9
Shuciran@htb[/htb]$ sudo nmap 10.129.2.0/24 -sn -oA tnet | grep for | cut -d" " -f5
10.129.2.4
10.129.2.10
10.129.2.11
10.129.2.18
10.129.2.19
10.129.2.20
10.129.2.28
Nmap Stylesheet
We can use the following github repo to represent in a better way the outcome of the XML file we do this by providing the .xsl file’s URL to the nmap Scan:
1
nmap -p21,53,80,135,139,389,443,445,464,593,636,3268,3269,5985,5986,9389,47001,49664,49665,49667,49668,49677,49688,49689,49691,49694,49700,49712,52849 -sCV -Pn -n -vvv -oX targetedBootstrap 10.10.10.103 --stylesheet=https://raw.githubusercontent.com/honze-net/nmap-bootstrap-xsl/stable/nmap-bootstrap.xsl
Then install the tool nmap-parser-output then we can move all the files from the cloned git to any of the PATH environment folders, in my case I move them to the /usr/sbin folder and access your previously outputed XML file, the nmap-parser-output tool will parse it directly: 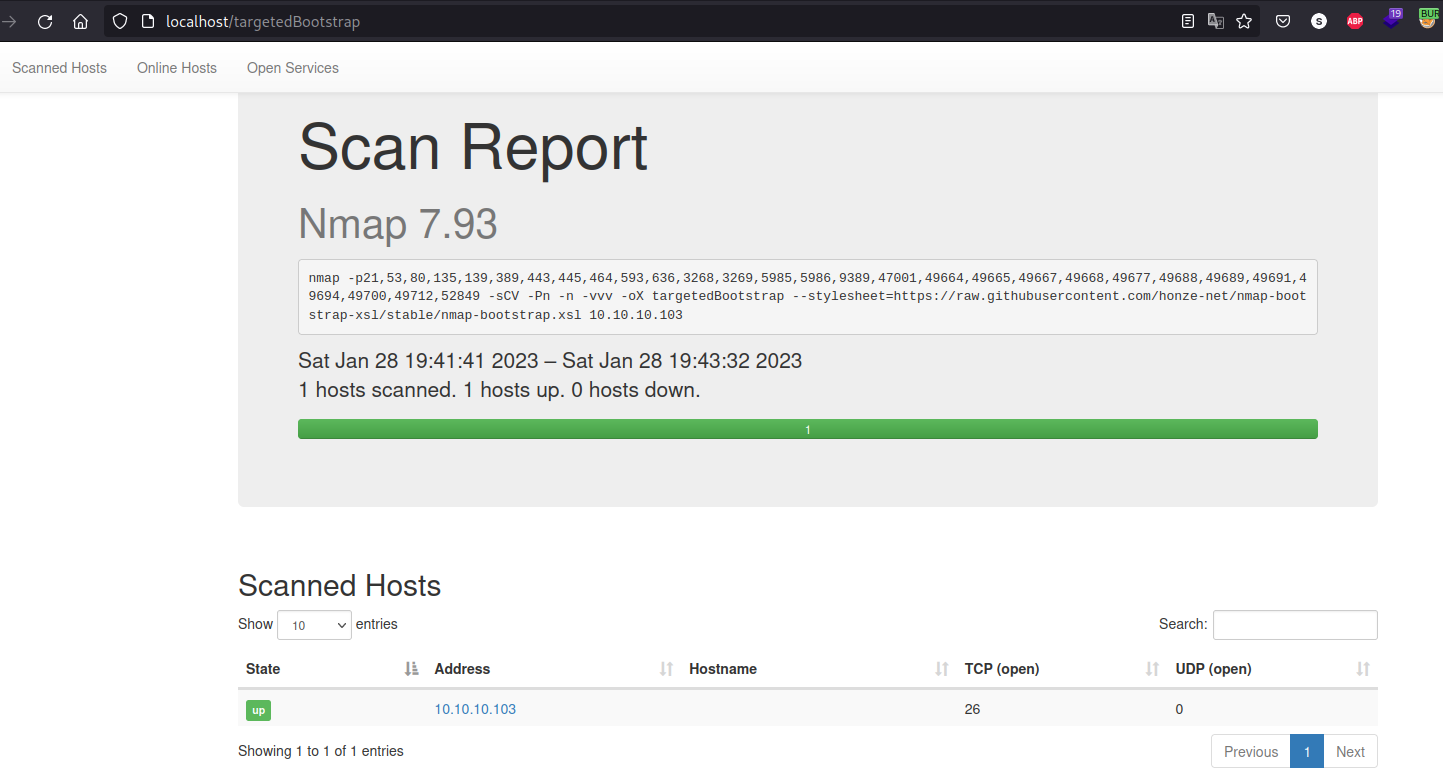 Examples: Sizzle
Examples: Sizzle
Parsing NMAP through Web server
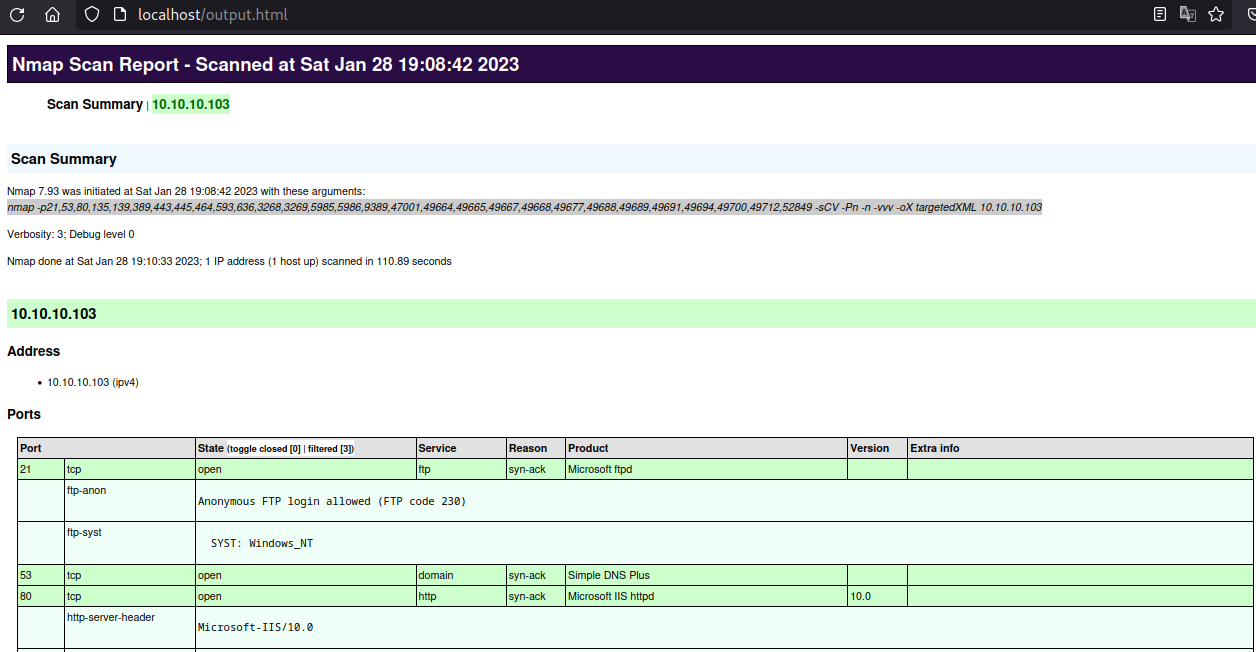
First execute -oX flag to save it in XML:
1
nmap -p21,53,80,135,139,389,443,445,464,593,636,3268,3269,5985,5986,9389,47001,49664,49665,49667,49668,49677,49688,49689,49691,49694,49700,49712,52849 -sCV -Pn -n -vvv -oN targeted 10.10.10.103
Then we can transform the XML format to an html format with xsltproc:
1
xsltproc targetedXML > output.html
And finally we can start a web server so the input is shown prettier:
1
php -S 0.0.0.0:80