LDAPDOMAINDUMP
Dumping useful information from the domain controller via LDAP:
1
2
3
4
5
6
ldapdomaindump -u 'htb.local\amanda' -p 'Ashare1972' 10.10.10.103
[*] Connecting to host...
[*] Binding to host
[+] Bind OK
[*] Starting domain dump
[+] Domain dump finished
Then we need to start a web server:
1
python3 -m http.server 80
And all the information will be available on localhost: 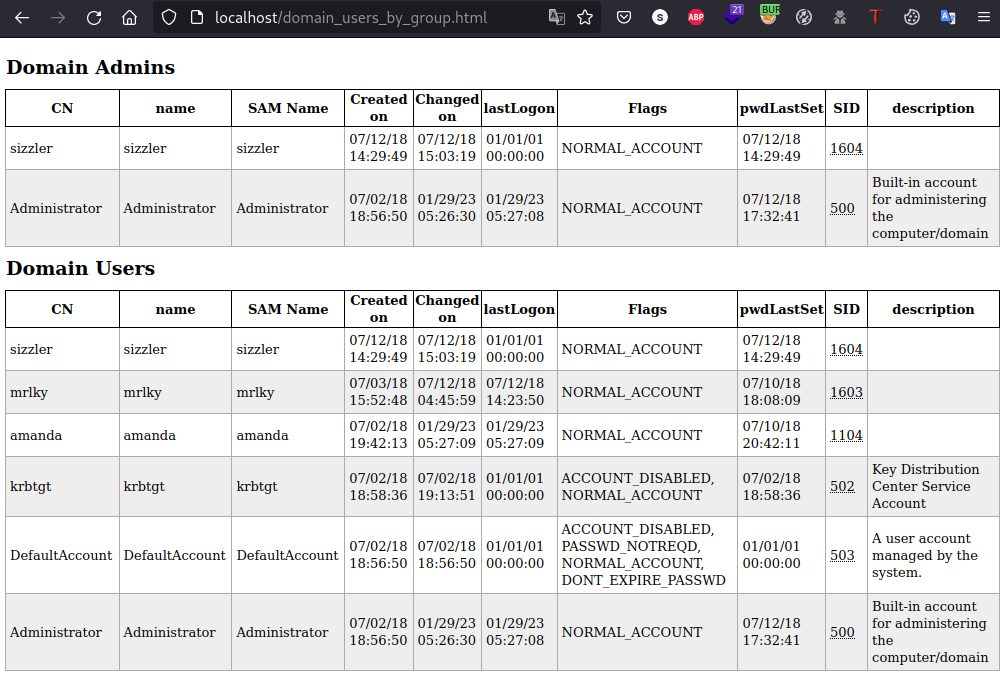 Examples: Sizzle
Examples: Sizzle
LDAPSEARCH
Basic Search
Perform a LDAP search query without binding to the admin account.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
ldapsearch -x -H ldap://10.10.11.168 -s base namingcontexts
# extended LDIF
#
# LDAPv3
# base <> (default) with scope baseObject
# filter: (objectclass=*)
# requesting: namingcontexts
#
#
dn:
namingcontexts: DC=scrm,DC=local
namingcontexts: CN=Configuration,DC=scrm,DC=local
namingcontexts: CN=Schema,CN=Configuration,DC=scrm,DC=local
namingcontexts: DC=DomainDnsZones,DC=scrm,DC=local
namingcontexts: DC=ForestDnsZones,DC=scrm,DC=local
# search result
search: 2
result: 0 Success
# numResponses: 2
# numEntries: 1
Detailed Search
You can use any of the namingcontexts retrieved with the Basic Search section
Perform a more detailed query about users on the domain:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
ldapsearch -x -H ldap://10.10.11.168 -b "dc=scrm,dc=local"
# extended LDIF
#
# LDAPv3
# base <dc=scrm,dc=local> with scope baseObject
# filter: (objectclass=*)
# requesting: namingcontexts
#
# search result
search: 2
result: 1 Operations error
text: 000004DC: LdapErr: DSID-0C090A5C, comment: In order to perform this opera
tion a successful bind must be completed on the connection., data 0, v4563
# numResponses: 1
Example: Scramble
LDAP Record Addition
We can add an LDAP registry if we have permissions with the dnstool.py as follows:
1
python3 dnstool.py -u 'intelligence\Tiffany.Molina' -p NewIntelligenceCorpUser9876 -r webos1 -a add -t A -d 10.10.16.7 10.10.10.248
Examples: Intelligence
Authenticated
We can enumerate LDAP if we have credentials as follows:
1
proxychains ldapsearch -x -H ldap://192.168.122.130 -D "FULCRUM\LDAP" -w 'PasswordForSearching123!' -b 'DC=fulcrum,DC=local'
Example: Fulcrum
Nmap
1
nmap -sT -Pn -n --open 192.168.73.20 -p389 --script ldap-rootdse
Example: Timelapse