DnSpy
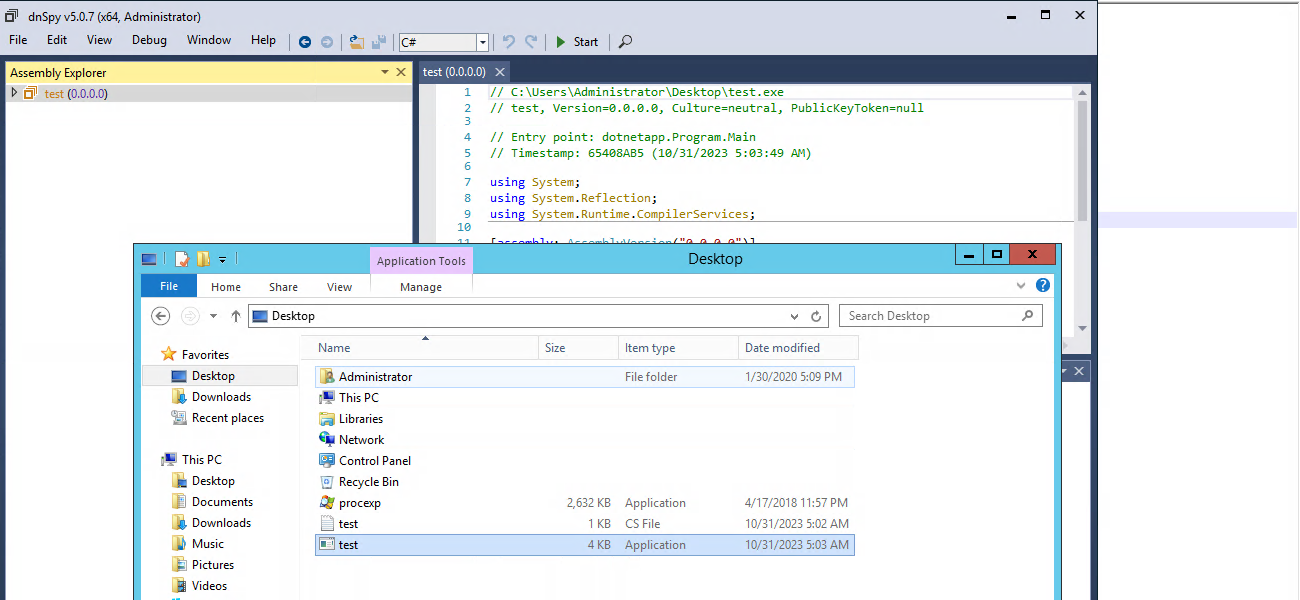
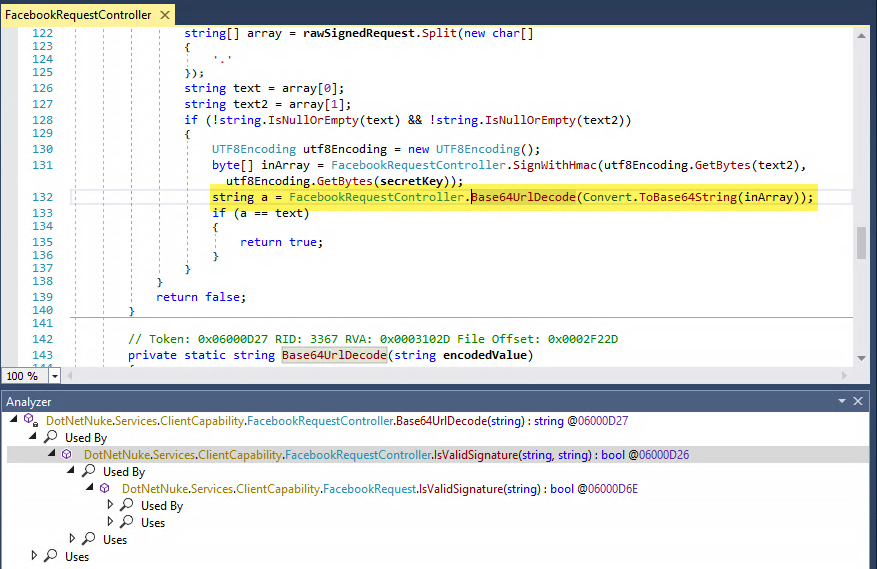
We use dnSpy and attempt to decompile an executable’s code. We’ll drag the test.exe file to the dnSpy window, which automatically triggers the decompilation process in dnSpy.
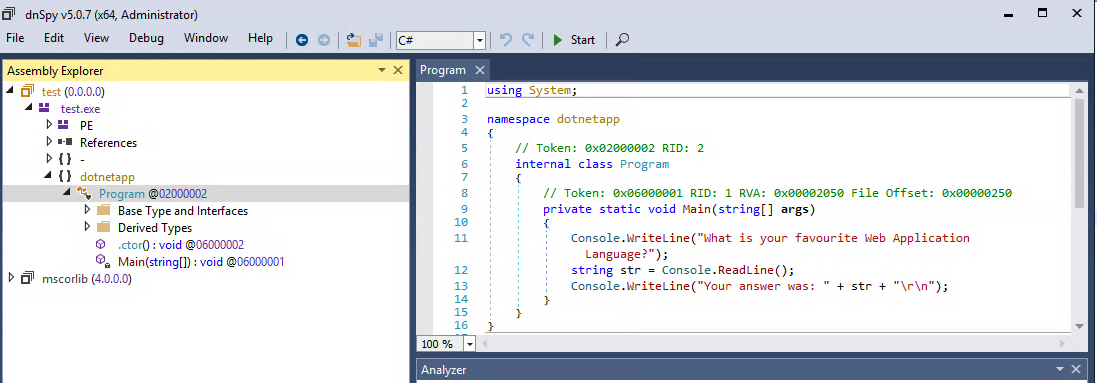
To view the source code of this executable, we’ll have to expand the test assembly navigation tree and select test.exe, dotnetapp, and then Program. According to the output, the decompilation process was successful.
Cross-References
When analyzing and debugging more complex applications, one of the most useful features of a decompiler is the ability to find cross-references to a particular variable or function. We can use cross-references to better understand the code logic. For example, we can monitor the execution flow statically or set strategic breakpoints to debug and inspect the target application. We can demonstrate the effectiveness of cross-references in this process with a simple example.
Let’s suppose that while studying our DotNetNuke target application, we noticed a few Base64-encoded values in the HTTP requests captured by Burp Suite. Since we would like to better understand where these values are decoded and processed within our target application, we could make the assumption that any functions that handle Base64-encoded values contain the word “base64”.
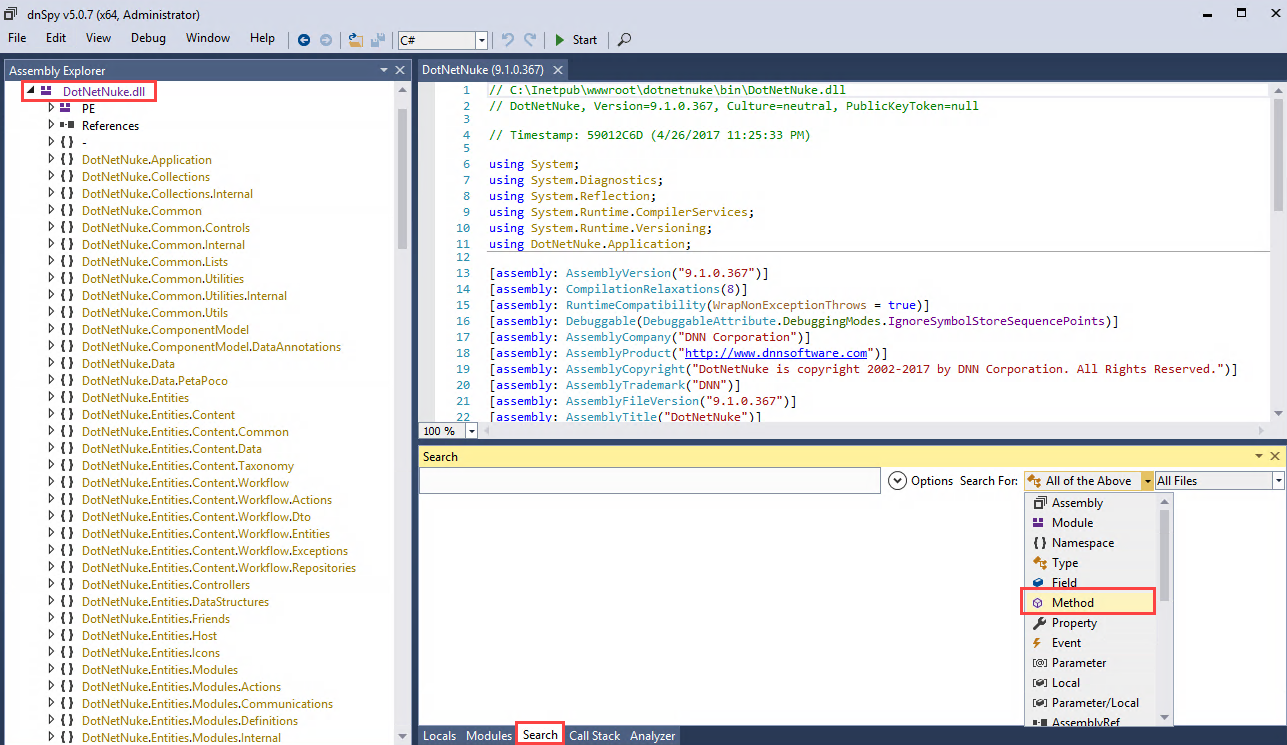
We’ll follow this assumption and start searching for these functions in dnSpy. For a thorough analysis we should open all the .NET modules loaded by the web application in our decompiler. However, for the purpose of this exercise, we’ll only open the main DNN module, C:\inetpub\wwwroot\dotnetnuke\bin\DotNetNuke.dll, and search for the term “base64” within method names as shown below:
The search then throws the following results: 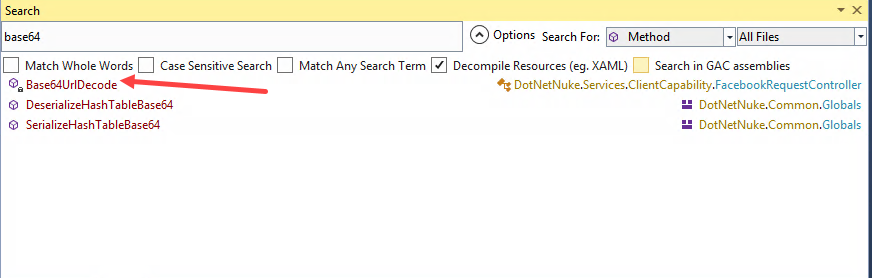
To retrieve such results we need to go to Options and unmark “Search in GAC assemblies” option
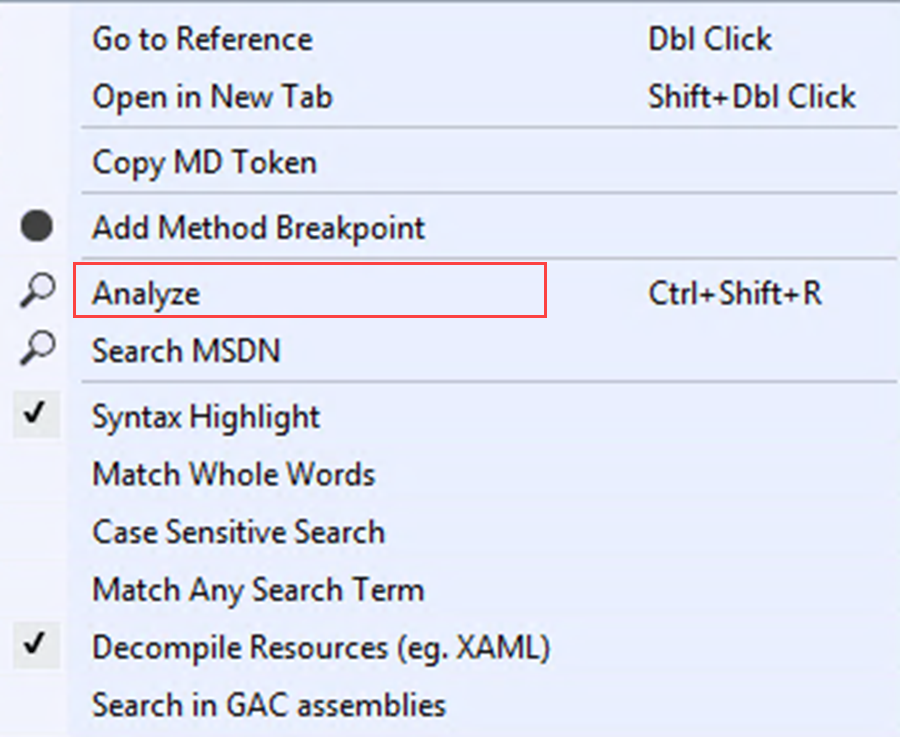
By picking one of the functions and try to find its cross-references. We’ll select the Base64UrlDecode function by right-clicking on it and selecting Analyze from the context menu.
The results should appear in the Analyzer window. Specifically, expanding the function name reveals two options: Used By and Uses: 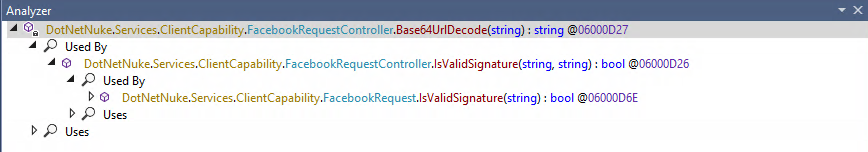
As the name suggests, the Used By node expands to reveal where our example function is called within the target DLL. This is extremely useful when analyzing source code. If we now click on the cross-reference, dnSpy reveals the location of the function call in the source code: