Sharphound.exe
First upload Sharphound to the system and then run the following commands from a folder where you can write as it will download a .zip file:
1
2
3
4
5
6
# For SharpHound.ps1 (each line is a command)
PS> Powershell -exec bypass
PS> Import-module SharpHound.ps1
PS> Invoke-BloodHound -CollectionMethod ACL,ObjectProps,Default
# For Sharphound.exe: Upload the file and execute it:
PS> .\SharpHound.exe
Examples: Streamio Intelligence Outdated
Bloodhound.py
Resources: bloodhound.py If you have no access to the machine bloodhound.py can be used from the attack machine:
1
apt install bloodhound.py
Then run it to create the bloodhound files:
1
bloodhound-python -c All -u amanda -p Ashare1972 -ns 10.10.10.103 -d htb.local
Running Bloodhound
#Note To execute bloodhound we need to run the following commands (one command each line):
1
2
neo4j console
bloodhound --no-sandbox
After extract/get the .json files go to the bloodhound GUI and upload them, then you’ll have a bunch of useful information for lateral and horizontal escalation:  After loading we then can use the bloodhound tool to check for potential pivoting and privilege escalations on the machines. One of the first enumeration techniques that we need to perform is to enumerate what we can do with our current compromised user, for that we need to enter its name on the search bar:
After loading we then can use the bloodhound tool to check for potential pivoting and privilege escalations on the machines. One of the first enumeration techniques that we need to perform is to enumerate what we can do with our current compromised user, for that we need to enter its name on the search bar:  Then we click on “Mark User as Owned”:
Then we click on “Mark User as Owned”:  Then we click on user’s icon and select any of the options on the search navigation bar specifically the “Analysis” tab and then select the Domain Admin Group:
Then we click on user’s icon and select any of the options on the search navigation bar specifically the “Analysis” tab and then select the Domain Admin Group: 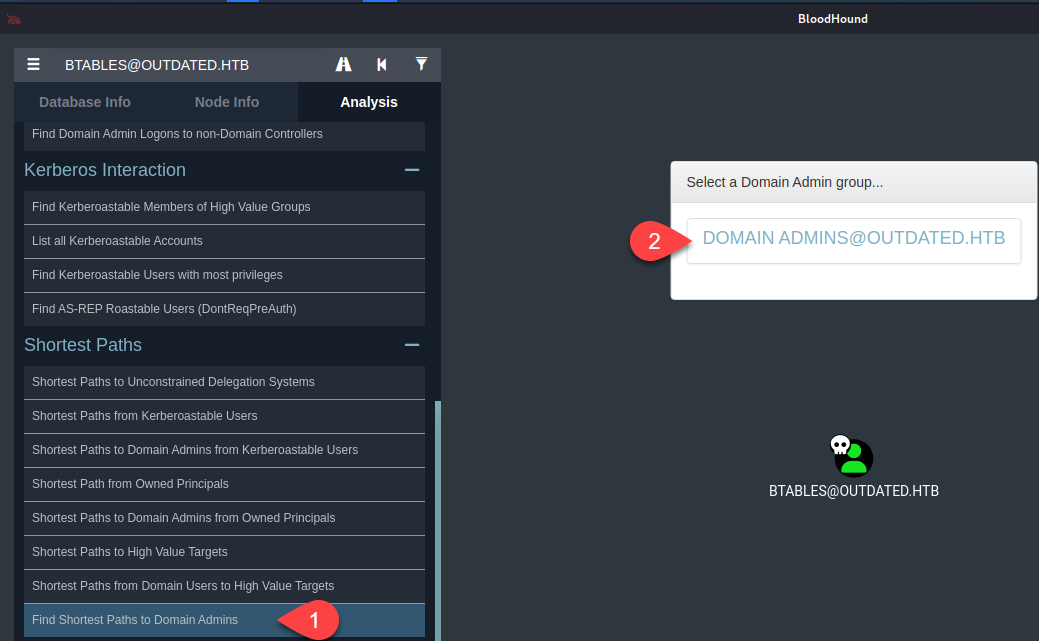 If the user is not generated on the graphic that means, there is no direct path to the Domain Admin:
If the user is not generated on the graphic that means, there is no direct path to the Domain Admin: 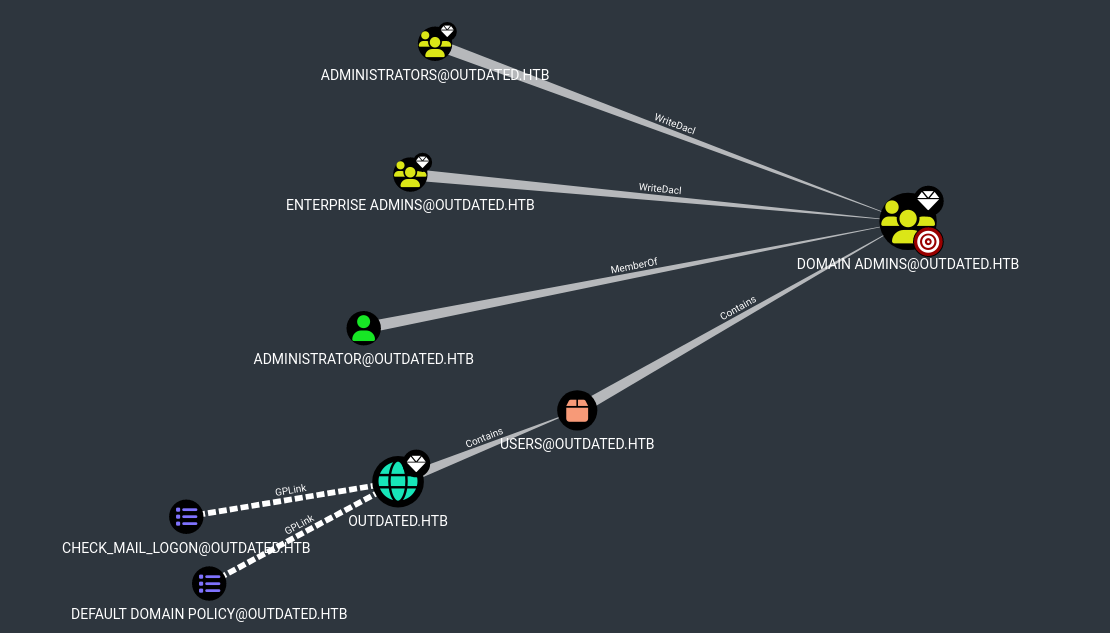 So we need to keep looking, now with the option “Shortest Path from Owned Principals”
So we need to keep looking, now with the option “Shortest Path from Owned Principals” 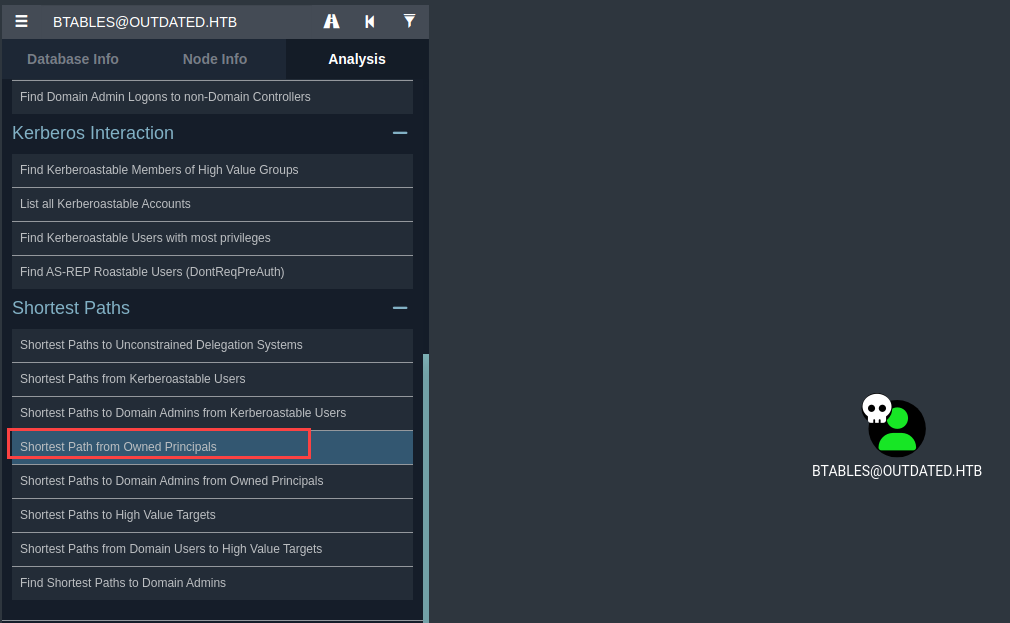 And now we get something interesting:
And now we get something interesting: 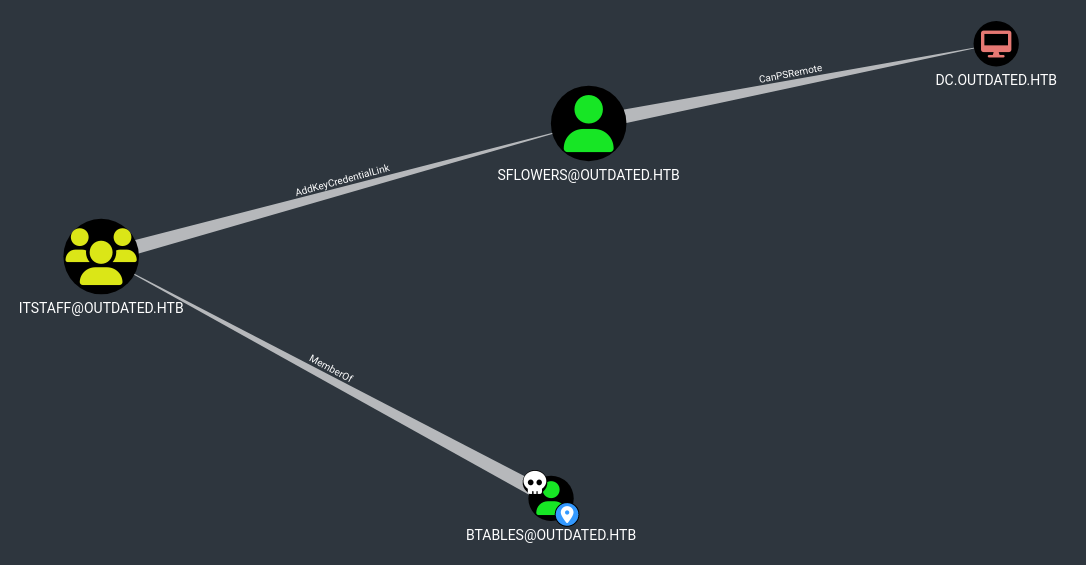 If we right -click on the “AddKeyCredentialLink” and select the Help menu:
If we right -click on the “AddKeyCredentialLink” and select the Help menu: 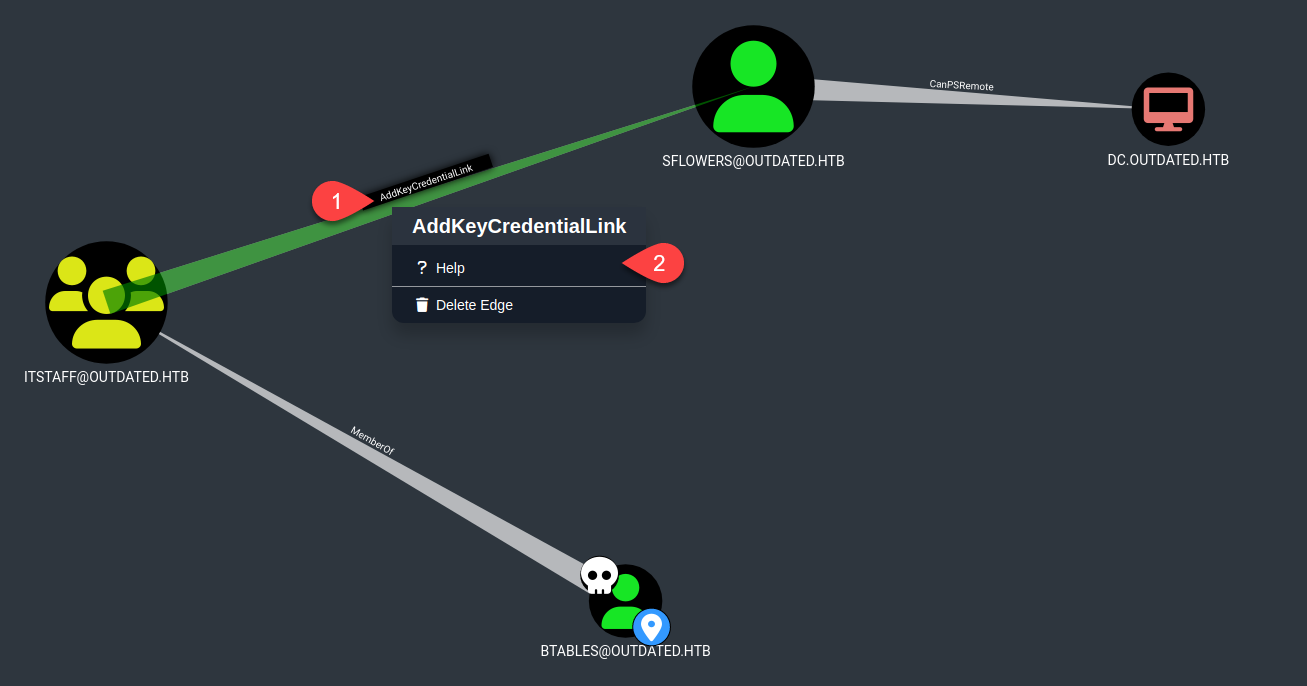 We can see that in order to escalate privileges we need to abuse of Whiskers executable:
We can see that in order to escalate privileges we need to abuse of Whiskers executable: 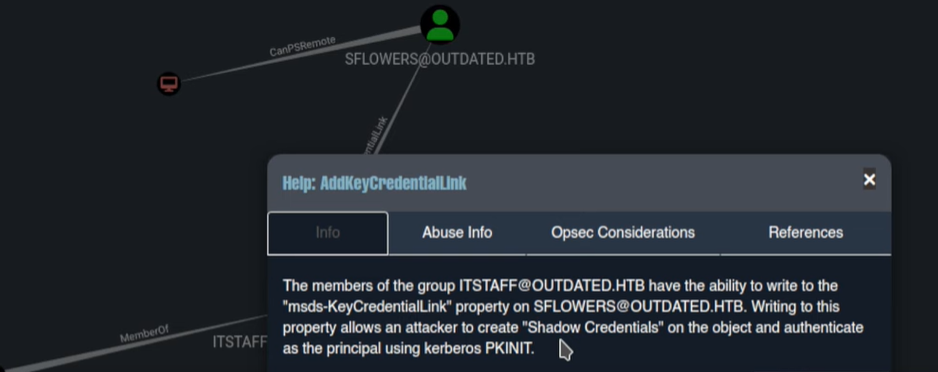 And also it gives the Info to Abuse of such misconfiguration:
And also it gives the Info to Abuse of such misconfiguration: 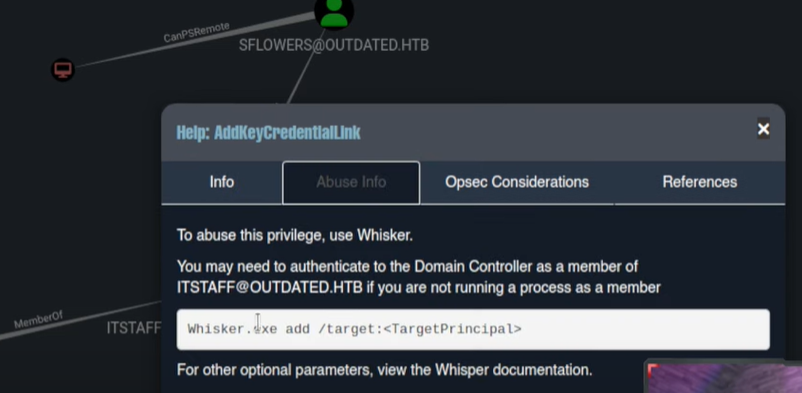 Examples: Outdated
Examples: Outdated
Clearing the database
All we need to do is click on Menu > Database Info > Clear Database: